EPSS: Exploit Prediction Scoring System Overview
Vulnerability management is one of the most important cybersecurity processes for organizations that care about their security posture. Companies need to identify and prioritize vulnerabilities in order to efficiently allocate resources and reduce the risk of cyberattacks, malware or other threats. While the Common Vulnerability Scoring System (CVSS) is widely used to assess the severity of vulnerabilities, it has its limitations. This article explores the key concepts of the Exploit Prediction Scoring System (EPSS) and how it can help organizations prioritize vulnerability remediation more effectively.
What is EPSS?
The Exploit Prediction Scoring System is a scale which ranges from 0 to 100. The higher the score, the higher the likelihood of exploitation. It can also be looked at as a vulnerability prioritization framework that uses a combination of metrics to estimate the likelihood that a vulnerability will be exploited in the wild. It is designed to help organizations allocate resources more effectively and mitigate all the relevant cyber risks.
EPS provides 2 similar values, let's take a closer look:
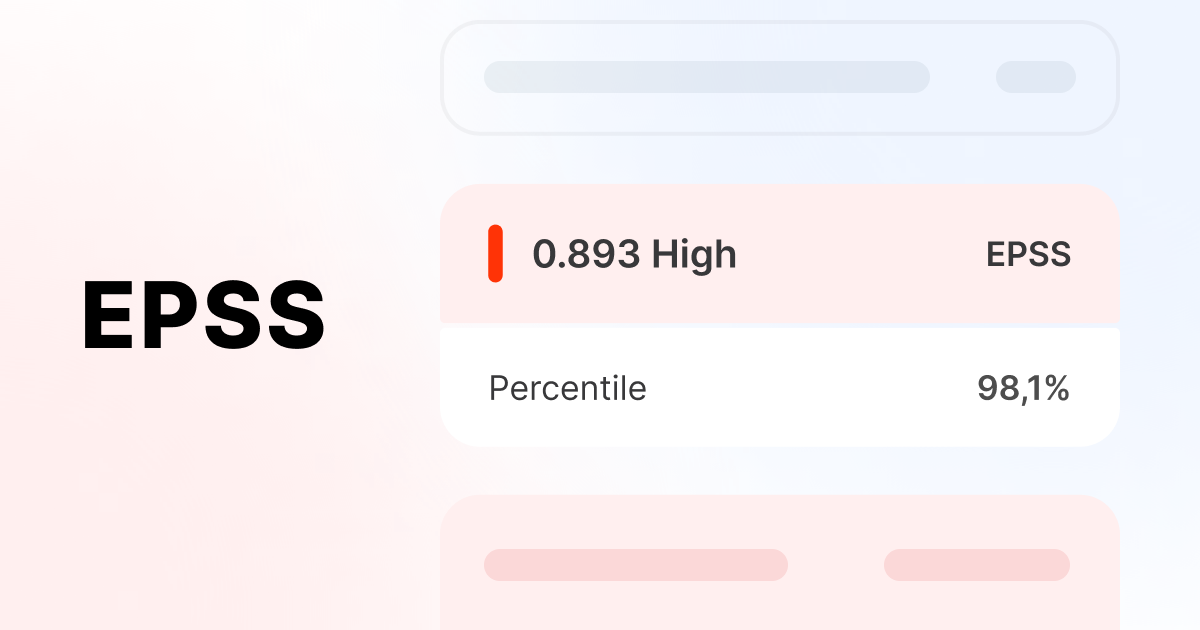
Probability
The likelihood of a vulnerability being exploited in the wild within the next 30 days.
Percentile
A value that indicates how likely it is to observe exploitation of this CVE vulnerability compared to all other CVE vulnerabilities.
Officially about EPSS indicators
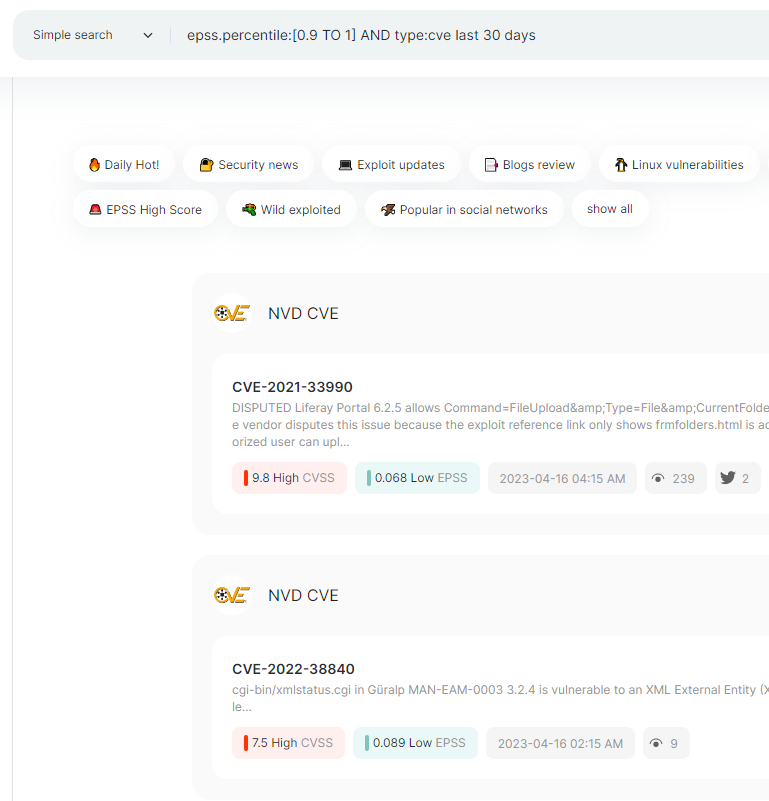
Vulners example request:
epss.percentile:[0.9 TO 1] AND type:cve last 30 days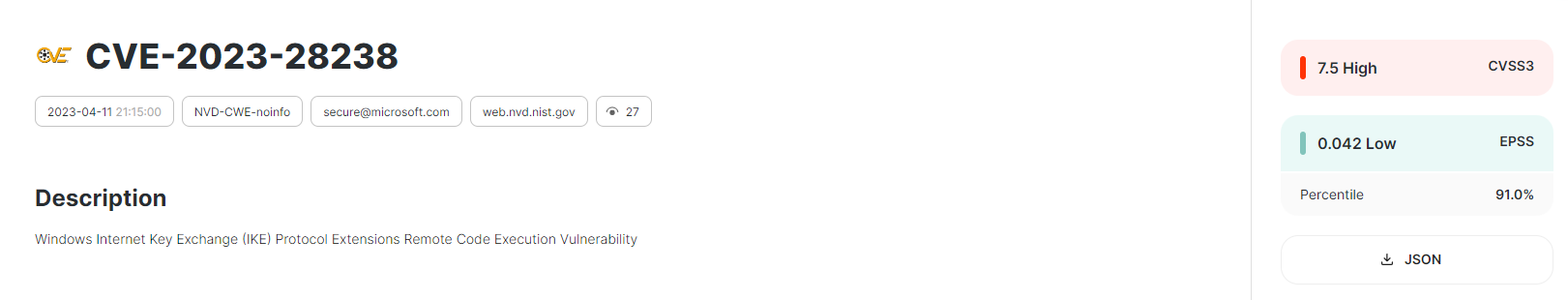
Benefits of using EPSS
EPSS provides several benefits to organizations in prioritizing vulnerability remediation. Firstly, it takes into account factors such as the age of the vulnerability, the popularity of the affected software, and the availability of exploit code. This helps organizations to focus on the vulnerabilities that are most likely to be exploited. Secondly, EPSS provides a more realistic view of the risks associated with a given vulnerability than CVSS. Finally, EPSS is more flexible than CVSS and can be tailored to meet the specific needs of an organization.
For example, consider a company that has 500 vulnerabilities to remediate. By using EPSS, they can identify the 10 most critical vulnerabilities with the highest EPSS scores and concentrate the remediation efforts on them. This ensures that they address the most critical vulnerabilities first and reduce their risk exposure significantly. Additionally, they can use EPSS to identify the 50 vulnerabilities with the lowest EPSS scores and deprioritize their remediation efforts. This frees up resources to allocate to other critical vulnerabilities, making their vulnerability management program more effective.
Limitations of EPSS
While EPSS provides many benefits, it also has some limitations:
- It requires a significant amount of data to generate accurate scores. If there is not enough data available, the EPSS score may not accurately reflect the likelihood of exploitation.
- EPSS does not take into account factors such as the skill level of potential attackers or the motivation behind an attack. As a result, it may overestimate or underestimate the risk associated with a vulnerability in certain situations.
- EPSS is not widely adopted yet, which means that some organizations may be unfamiliar with it or may doubt its results.
Conclusion
In summary, vulnerability management is a complex process that requires careful planning and execution. By using EPSS, organizations can better prioritize their vulnerability remediation efforts and allocate resources efficiently. EPSS allows organizations to identify the most critical vulnerabilities and deprioritize their remediation efforts on low-risk vulnerabilities. However, organizations should use EPSS as part of a comprehensive vulnerability management program that includes other strategies. By doing so, organizations can significantly reduce risk and improve the overall cybersecurity posture.
Vulners links the EPSS score to vulnerabilities, and now you can integrate this parameter into your own systems and processes: