Navigating CVSS v4.0: Metrics, Changes, and Real-World Impact
Introduction
On November 1, 2023, the cybersecurity community witnessed the official launch of Common Vulnerability Scoring System version 4.0 (CVSS v4.0), an area that last saw a major revision over eight years ago with CVSS v3.1 in June 2019. In this article, we will delve into the intricacies of this new framework and explore the reasons behind its incorporation into the Vulners database.
CVSS v4 isn't just an upgrade. It's a comprehensive refinement, introducing unprecedented granularity in Base Metrics.
The success of CVSS v4 depends not only on its technical merits, but also on its adoption by the cybersecurity community. We'll examine the challenges and opportunities of integrating this new framework into existing workflows, including ensuring vendor support and fostering community.
Expectations from a new CVSS version
As the cybersecurity community anticipates the upgrade of the Common Vulnerability Scoring System to version 4 (CVSS v4), some key expectations are emerging:
- Improved granularity: The community expects CVSS v4 to provide a more detailed breakdown of basic metrics, giving professionals a finer understanding of vulnerabilities for better decision-making.
- Real-world effectiveness: The practical effectiveness of CVSS v4 is a focus. It is expected that the refined metrics will result in more accurate vulnerability assessments, thereby supporting proactive risk mitigation.
- Timely updates and feedback loop: A responsive feedback loop is expected to ensure timely updates and refinements to CVSS v4 based on emerging cybersecurity threats and evolving landscapes.
- National Vulnerability Database (NVD) Integration: Anticipation surrounds the integration of CVSS v4 data into the National Vulnerability Database (NVD), improving standardized vulnerability assessments and supporting broader industry adoption.
As CVSS v4 evolves, meeting these expectations will be critical to realizing its effectiveness and fostering widespread adoption within the cybersecurity community.
Technical Changes in CVSS 4.0
The new score consists of 5 groups:
- Base metrics
- Supplemental metrics
- Environmental metrics (Modified Base Metrics)
- Environmental metrics (Security Requirements)
- Threat metrics
Further we provide additional details on what has changed and what remained the same.
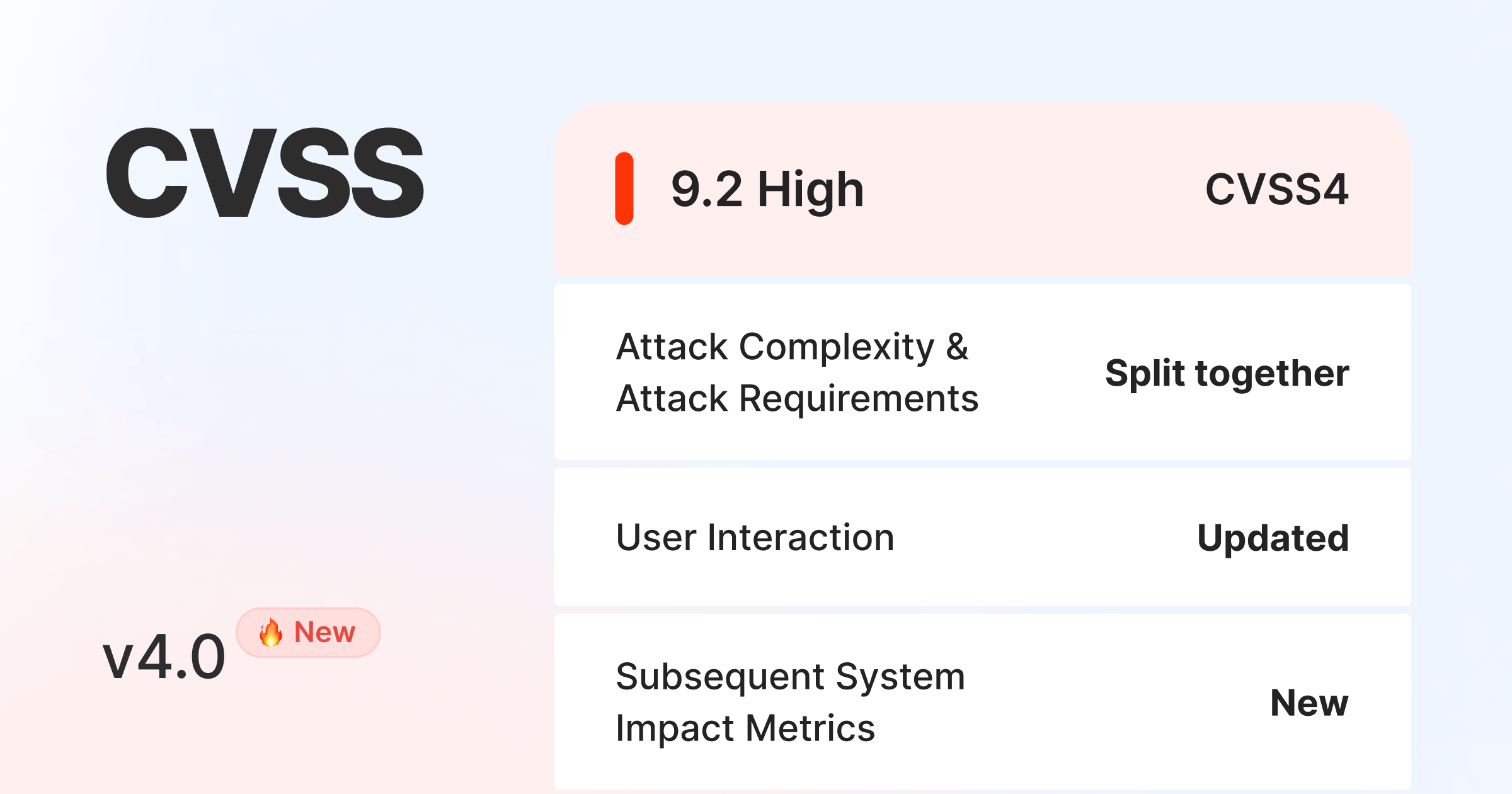
1. Base metrics (Updated)
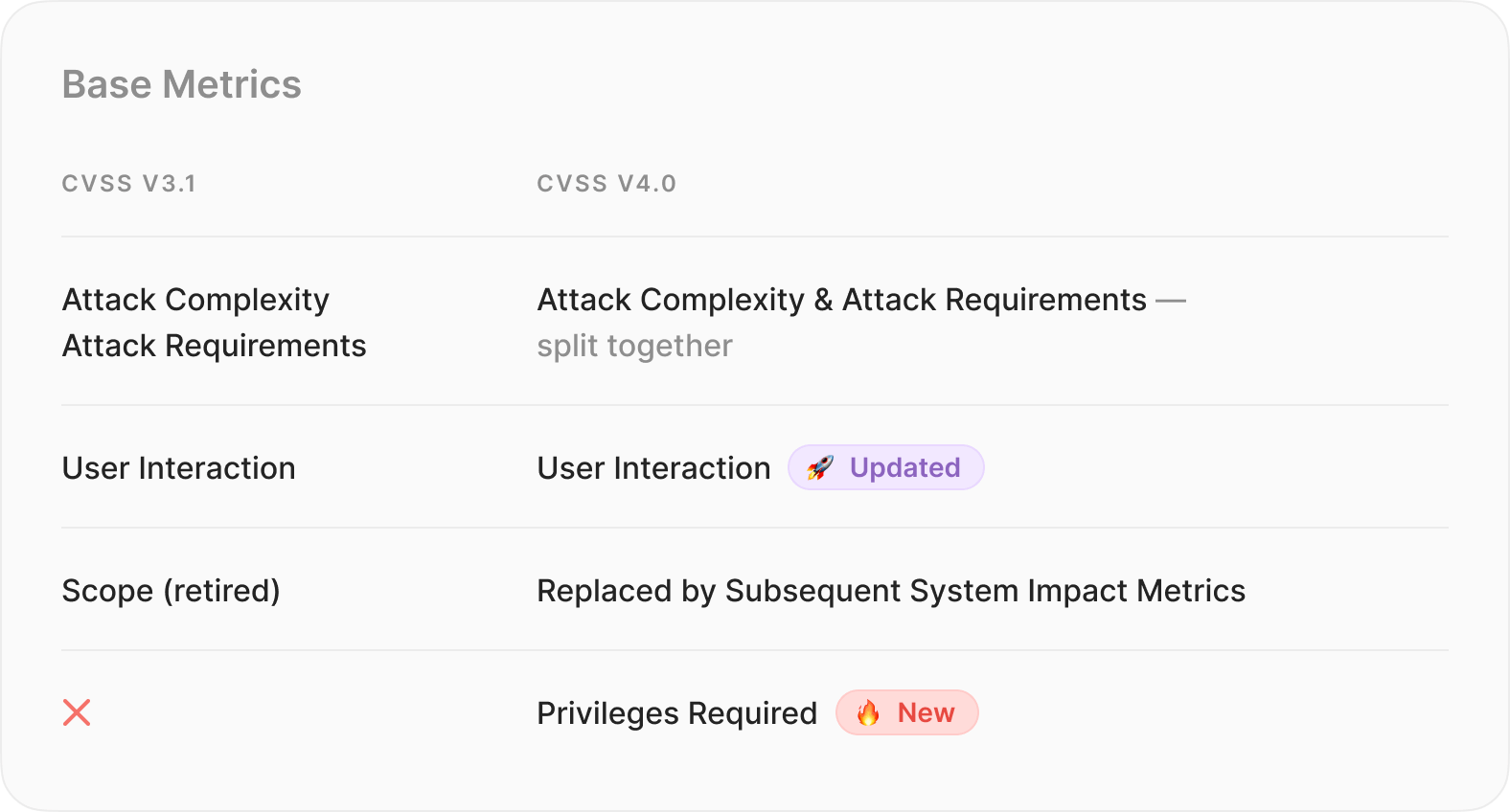
Attack Complexity and Attack Requirements (split): CVSS 4.0 brings a refined approach to the Attack Complexity parameter by splitting it into two components: Attack Complexity and Attack Requirements. This split allows for a more detailed analysis of vulnerability scenarios. Attack Complexity now addresses highly specialized attacks, while Attack Requirements covers situations where successful exploitation depends on specific usage conditions. It is expected that the open-source ecosystem will make less use of Attack Requirements, as it is tailored to specialized attacks.
Privileges Required (New): The introduction of the Privileges Required parameter in CVSS 4.0 brings small but important changes for clarity. While the value of the parameter remains largely unchanged, these adjustments are intended to provide more precise and concise wording. Anticipated usage suggests that there will be no significant changes in how this parameter is used for vulnerability assessment. However, the clarifications will contribute to a more effective evaluation of privilege requirements in the vulnerability assessment process.
User Interaction (Updated): CVSS 4.0 introduces a notable update to the User Interaction parameter, expanding it to include three values: None, Passive, and Active. This expansion provides a more nuanced assessment of attack conditions.
- None: Indicates scenarios where the vulnerable system can be exploited without any interaction from a human user apart from the attacker.
- Passive: Includes attacks that are executed through involuntary actions by the victim.
- Active: Applied when the attack relies on the victim to perform specific, deliberate interactions with the vulnerable system and the attacker's payload. Alternatively, when the victim's interactions actively subvert protection mechanisms, resulting in the exploitation of the vulnerability. This update introduces a change in how the user interaction parameter is used in vulnerability assessments.
Scope (retired — replaced by Subsequent System Impact Metrics): CVSS 4.0 marks the retirement of the Scope parameter, replacing it with Subsequent System Impact Metrics. This change is intended to provide better severity distribution and improve the accuracy of vulnerability impact assessments. The Subsequent System Impact Metrics not only parameterize the change in scope, but also determine the impact on the subsequent system. This change introduces a more accurate impact assessment that provides a comprehensive understanding of the impact of the vulnerability beyond the initial system compromise.
2. Supplemental Metric Group (new)
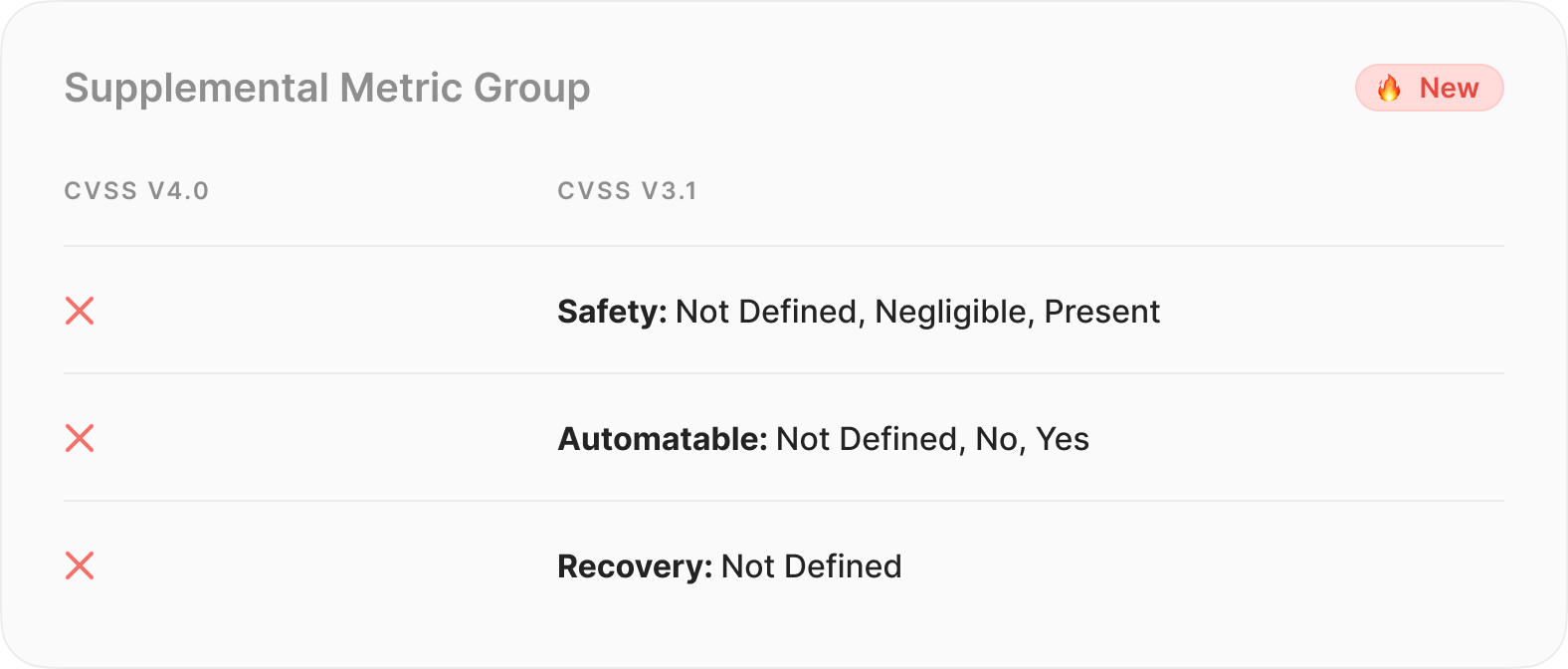
In a notable addition, CVSS v4.0 introduces the Supplemental Metric Group. This optional metric group is designed to provide a more complete understanding of vulnerabilities by offering additional extrinsic attributes. The Supplemental Metric Group is designed to provide users with contextual information that allows them to take additional steps in risk analysis beyond the core CVSS metrics.
Key Aspects of the Supplemental Metric Group:
- Optional Nature:
- The Supplemental Metric Group is entirely optional, providing flexibility in its application.
- Unlike core CVSS metrics, Supplemental metrics do not contribute to the calculation of CVSS scores. Instead, they serve as supplementary information for a more nuanced vulnerability assessment.
- Contextual Insights:
- Supplemental metrics offer valuable insights into extrinsic aspects of vulnerabilities, allowing consumers to delve deeper into specific contextual considerations.
- These metrics act as a complementary layer, enriching the overall risk analysis process by addressing diverse factors associated with vulnerabilities.
3/4. Environmental Metrics (updated and divided)
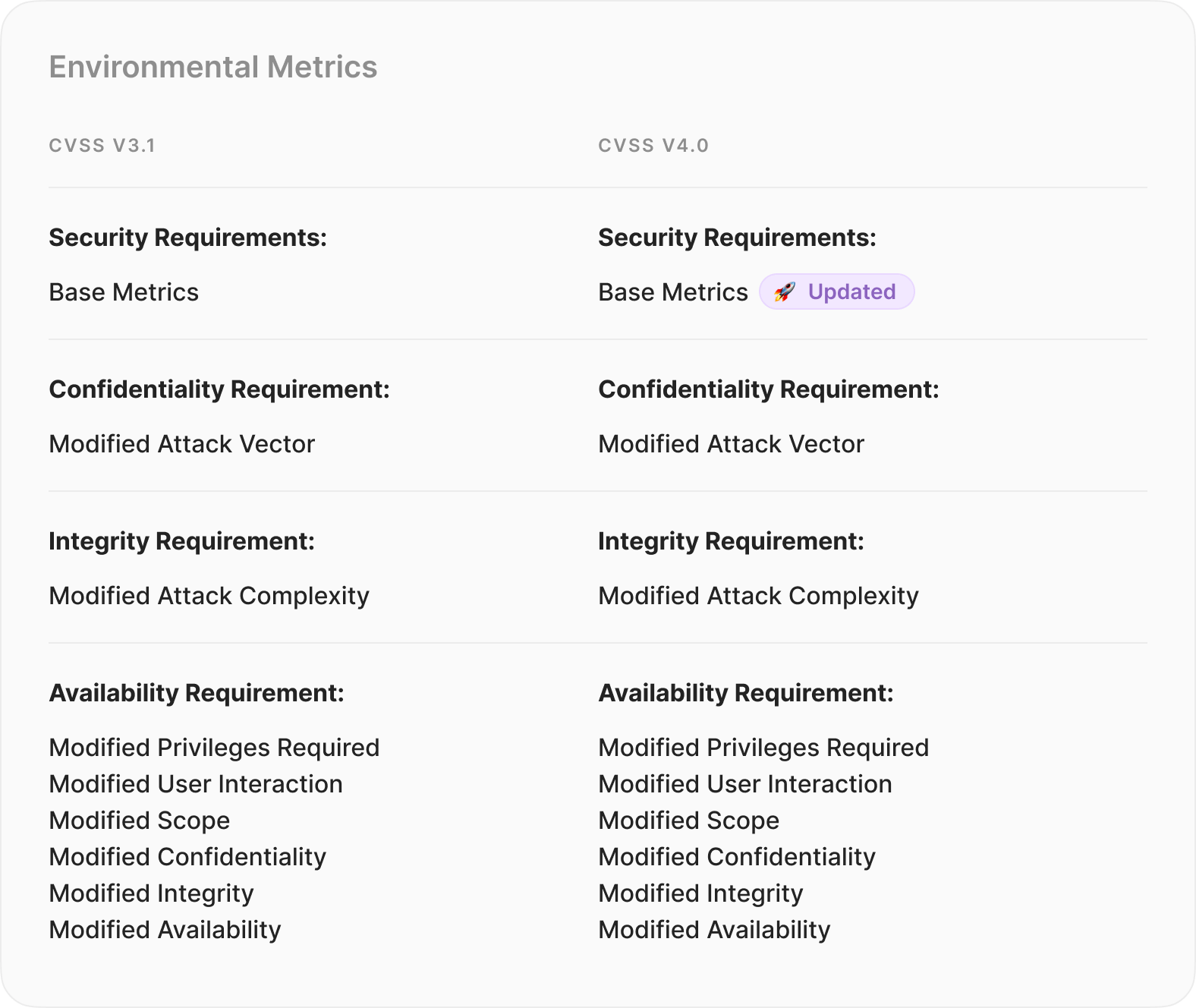
This strategic split aims to enhance the precision and depth of vulnerability assessments in diverse real-world scenarios.
Environmental (Modified Base Metrics):
- Goal: This metric focuses on comprehending the influence of vulnerabilities in specific operational setups.
- Details: It considers elements such as network structure and compensating controls customized for the unique conditions of the environment.
- Importance: Provides a more accurate assessment of the actual risk presented by a vulnerability.
Environmental (Security Requirements):
- Goal: Evaluating the efficiency of current security measures to meet various security needs
- Details: Examines present security controls, evaluating their suitability considering the identified vulnerability.
- Importance: Recognizing the varying implications of a vulnerability depending on the strength of existing security measures.
5. Threat Metrics
In the realm of CVSS 4.0, Threat Metrics introduce significant changes, especially in the part formerly known as Temporal Score. Our primary focus is on Exploit Code Maturity, which is now called Exploit Maturity, presenting a more concise paradigm with four distinct values. One noteworthy alteration is the elimination of the Functional value to consolidate the metric, enabling a more refined assessment.
The Four Faces of Exploit Maturity.
- Not Defined. When reliable threat intelligence is difficult to obtain, this value plays a crucial role in recognizing the uncertainty and encouraging vigilance in the absence of clear Exploit Maturity characteristics.
- Attacked (formerly High). Use this value when attacks have been reported or when the exploit has reached a level of maturity by integrating into solutions such as exploit kits. This indicates a significant change towards a more detailed comprehension of active threats.
- PoC (Proof-of-Concept). Deploy when a proof-of-concept is publicly available, or if there is no publicly available solutions or reported attempts to simplify exploitation. This value enhances specificity for a more targeted evaluation.
- Unreported. In scenarios where threat intel is available but neither PoC nor Attacked are applicable, the Unreported value fills the gap, acknowledging the diversity of threat landscapes and impacting Exploit.
Maturity Parameter Usage.
- This updated version redefines and consolidates values to streamline the Exploit Maturity parameter. The goal is to enhance the assessment of threats, aligning with the dynamic nature of cybersecurity in the CVSS 4.0 era. As these changes transform the way we gauge the exploit landscape, it's crucial to stay informed, empowering us to fortify our defenses with better decision-making.
Conclusions
In conclusion, the launch of Common Vulnerability Scoring System version 4.0 marks a significant milestone in the cybersecurity community. With its improved granularity and comprehensive refinement of base metrics, CVSS v4.0 is expected to provide professionals with a finer understanding of vulnerabilities, enabling better decision-making in risk assessment and mitigation.
As the cybersecurity community anticipates the impact of CVSS v4.0, it's important to acknowledge the challenges and opportunities that come with its adoption. Integrating the new framework into existing systems and workflows may pose challenges, but the potential for more accurate vulnerability assessments and proactive risk mitigation makes it a worthwhile endeavor.
We at Vulners are committed to staying at the forefront of cybersecurity and will integrate CVSS v4.0 into our database as soon as possible, meaning when major players like NIST NVD start using it and publishing the scores. This integration will allow us to add more intelligence to vulnerabilities, providing the cybersecurity community with standardized and up-to-date information for a more comprehensive understanding of potential risks.
Overall, CVSS v4.0 represents a significant step forward in vulnerability assessment, and we look forward to its widespread adoption and the enhanced cybersecurity practices it will facilitate.
