Microsoft Monthly Patch, exploit competition and attacks

The second Tuesday of each month traditionally pleases the user with a Microsoft update. The annual Tianfu Cup was also held in which researchers demonstrate zero-day vulnerabilities with exploits for them. And the final stage of our digest is the most recent attacks.
- Vulnerabilities: Microsoft weekly patch, emergency for Apple and Tianfu Cup;
- Tools: ThreatMapper, EDRHunt and Azur3Alph4;
- News: Microsoft ddos attack, malware for Huawei Cloud and Banco Pichincha under attack;
- Research: new ransomware Yanluowang and other research.
Feedback and Vulners docs
Vulnerabilities

Microsoft patches over 71 vulnerabilities in Windows products and components.
The most significant vulnerabilities from this package of fixes are mentioned in the facts of cyber espionage using 0-day vulnerabilities.
- CVE-2021-40449 (7.8 CVSS): Win32k privilege escalation vulnerability which discovered by Kaspersky. All indications are that the vulnerability was exploited by APT Iron Husky
- CVE-2021-41335 (7.8 CVSS): Windows kernel privilege escalation vulnerability;
- CVE-2021-40469 (7.2 CVSS): Windows DNS Server Remote Code Execution Vulnerability.
- CVE-2021-41338 (CVSS 5.5): Bypass security vulnerability in Windows AppContainer firewall rules.
Other more serious bugs include remote code execution vulnerabilities affecting Microsoft products:
- CVE-2021-26427: Exchange Server;
- CVE-2021-38672, CVE-2021-40461: Windows Hyper-V;
- CVE-2021-40487, CVE- 2021-41344: SharePoint Server;
- CVE-2021-40486, CVE-2021-40454: Microsoft Word.
We strongly recommend that you update your systems to avoid negative consequences.

Apple has released an emergency update to iOS 15.0.2 and iPadOS 15.0.2.
0-day CVE-2021-30883 vulnerability has been fixed, the exploitation of which could allow code execution with kernel privileges on an attacked device. Apple said that the bug is actively used in the wild, there are no details, as usual. CVE is operated as part of a combat exploit kit.
Saar Amar quickly reversed the patch, created PoC CVE-2021-30883 and successfully tested it on iOS 14.7.1 to 15.0.1.
Recommended to urgently update!

Last year, we wrote about the competitions held on October 16 and 17 in Chengdu, with a prize pool of $ 1.88 million.
During the tournament teams had three attempts, 5 minutes each, to hack the selected device or software using authoring exploits that they had been developing since July after the organizers had identified 16 possible targets.
Hackers managed to hack: Windows 10 - 5 times, Adobe PDF Reader - 4 times**, Ubuntu 20 -** 4 times**, Parallels VM** - 3 times, iOS 15 - 3 times, Apple Safari - 2 times, Google Chrome - 2 times, ASUS AX56U router - 2 times, Docker CE - 1 time, VMWare ESXi - 1 time, VMWare Workstation - 1 time, qemu VM - 1 time, Microsoft Exchange - 1 time.
As a result, 11 participants successfully implemented attacks against 13 targets, and representatives of the Kunlun Lab team won the competition (the second went to PangU, the third to the Vulnerability Research Institute (VRI). 3 targets remained intact: NAS Synology DS220j, Xiaomi Mi 11 and unnamed chinese electric car.
Tools
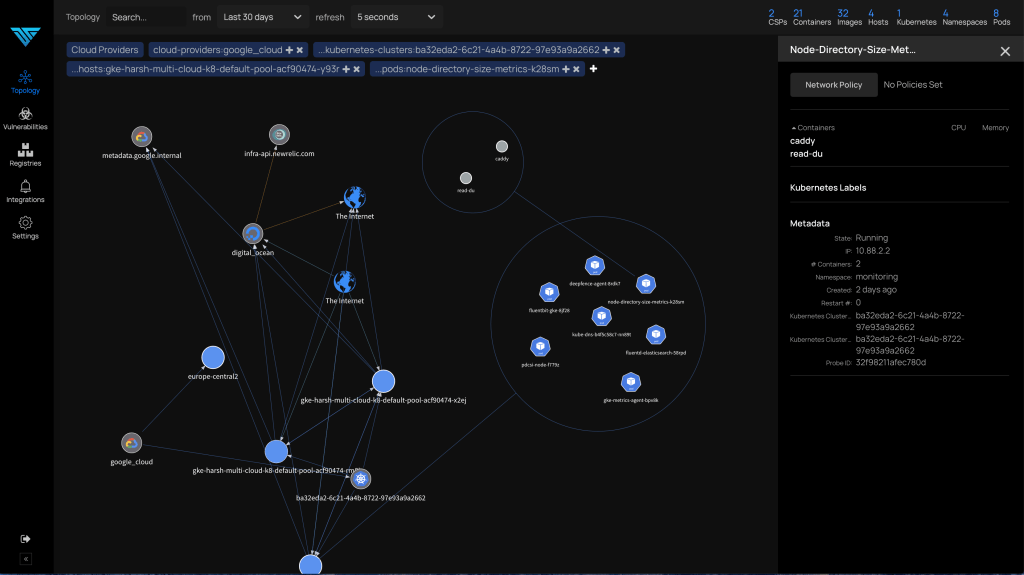
Deepfence ThreatMapper helps you to monitor and secure your running applications, in Cloud, Kubernetes, Docker and Fargate Serverless.
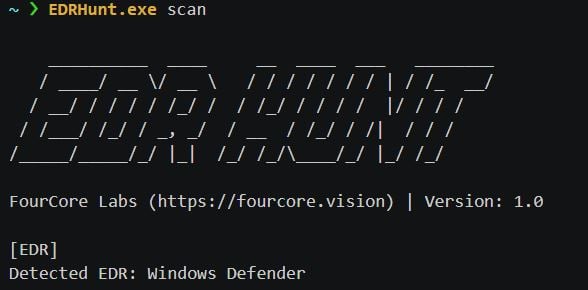
EDRHunt: scans Windows services, drivers, processes, registry for installed EDRs (Endpoint Detection And Response)
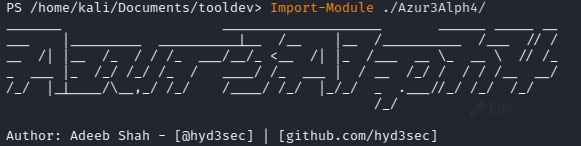
Azur3Alph4: PowerShell module that automates red-team tasks for ops on objective.
News

Microsoft announced it has successfully repelled the largest DDoS attack with a capacity of 2.4 Tbit/s. The attack took place in short waves for several minutes, however, the systems managed to successfully repel the attack of the attackers, and the work of the Azure service wasn't affected. According to company representatives, the attackers targeted data from Azure users from Europe.

TrendMicro researchers have discovered a new Linux cryptominer targeting Huawei Cloud. If the system is infected, the malware creates accounts of the attackers, assigning them root privileges. A distinctive feature of this malware is that after infection, cybercriminals use their own ssh-RSA key to make changes to the system.

Banco Pichincha under attack
Last weekend, when the country's largest private bank, Banco Pichincha, underwent a cyberattack that shut down all infrastructure, including the bank and remote banking systems.
Banco Pichincha admitted to the cyberattack and its negative consequences two days later, stating that there were no financial losses or any threats to the safety of customers' savings.
https://twitter.com/ruben\_rect0425/status/1159612616718856198
Research

Ransomware Yanluow
Symantec Threat Hunter Team Broadcom has discovered a new ransomware Yanluowang that is used in targeted attacks against companies around the world. To infiltrate the victim's devices and then pin them, they use the AdFind tool (a command line tool for sending requests to AD). According to experts, the Yanluowang malware can also be used to carry out DDoS attacks.
How cyberattacks are changing according to new Microsoft Digital Defense Report: https://www.microsoft.com/security/blog/2021/10/11/how-cyberattacks-are-changing-according-to-new-microsoft-digital-defense-report
Active Directory Discovery Detection: Threat Research Release, September 2021: https://www.splunk.com/en_us/blog/security/active-directory-discovery-detection-threat-research-release-september-2021.html
Feedback and Vulners docs
21.html](https://www.splunk.com/en_us/blog/security/active-directory-discovery-detection-threat-research-release-september-2021.html)
Feedback and Vulners docs
