Another day (week/month) -> another 0-day

Read about all the most important vulnerabilities in our digests and reviews. Update this month we have expanded the section with the Research, today it contains more research articles, analysis of new malware and attacks. Note that a button has been added for Tools to directly download utilities.
- Vulnerabilities: SonicWall, few zero-days for Chrome, 0-days in Apple devices, QNAP (weekly) and Trend Micro patch;
- Tools: DNSTake, SuperMem (Crowdstrike), QueenSono, SharpStrike and BoobSnail;
- News: CISA alarm, Chinese APT activity in Afganistan and Clubhouse db leak;
- Research: Malware research, useful detections and attacks.
Feedback and Vulners docs
Vulnerabilities

SonicWall critical update
SonicWall has patched CVE-2021-20034 critical vulnerability in 100 Series Secure Mobile Access (SMA) product access control systems, including SMA 200, 210, 400, 410 and 500v.
A discovered vulnerability relates to an incorrect file path restriction in a restricted directory. It's successful exploitation could allow attackers to delete arbitrary files from unpatched SMA 100 Secure Access Gateways to return to default settings and potentially gain administrative access to the device.
The vendor found no evidence that the vulnerability is currently being exploited in the wild. There is no temporary mitigation of the attack vector, so SonicWall urged customers to deploy security updates from MySonicWall.com as soon as possible.

zero-days in Chrome
Google released an urgent update for Chrome: Windows, Mac and Linux, caused by critical 0-day vulnerabilities, some of which are actively exploited in the wild.
- CVE-2021-37973: about after fixing flaws in Portals, Google's new web navigation system for Chrome. Successful exploitation of this vulnerability could allow attackers to execute arbitrary code on computers with vulnerable versions of Chrome. The existence of an exploit for CVE-2021-37973 was acknowledged by the developer himself. This is the 11th fixed 0-day vulnerability in the Chrome web browser since early 2021.
- CVE-2021-37974: 0-day and UAF (Use After Free), but not seen in the wild. These vulnerabilities lead to remote code execution by an attacker.
- CVE-2021-37975: is also a UAF vulnerability.
- CVE-2021-37976: concerns information leaks in the kernel and has a medium severity.
Google has since the beginning of the year fixed fourteen 0-days in Chrome.
Disclosure of three 0-day iOS vulnerabilities and critique of Apple Security Bounty program:

QNAP vulnerability QVR
QNAP has patched its QVR video management system by fixing 2 critical issues that can be exploited to execute arbitrary commands. QNAP has addressed a total of 3 command injection vulnerabilities in QVR video management software:
The fixed critical vulnerabilities affect expired QVR products (EoL). Even if the devices are no longer supported, many customers are likely still using them, which is why QNAP has released the QVR 5.1.5 software update build 20210803.

Trend Micro has released fixes for CVE-2021-36745: critical vulnerability allows attackers to bypass Trend Micro ServerProtect authentication. ServerProtect is an enterprise-grade real-time malware detection solution designed to protect servers from malware and automate security operations.
The vulnerability affects: ServerProtect for Storage (SPFS) 6.0 for Windows, ServerProtect for EMC Celerra (SPEMC) 5.8, ServerProtect for Network Appliance File Servers (SPNAF) 5.8, and ServerProtect for Microsoft Windows / Novell Netware (SPNT) 5.8.
Tools

DNSTake: Utility to check missing hosted DNS zones that can lead to subdomain takeover.

Introducing SuperMem: A Free Incident Response Tool | CrowdStrike
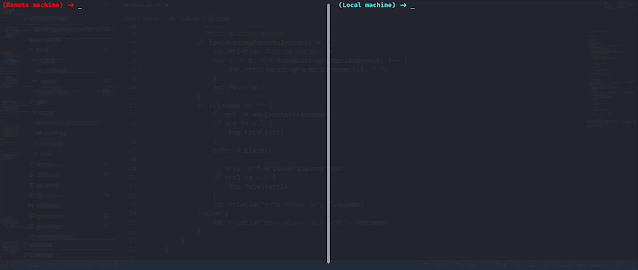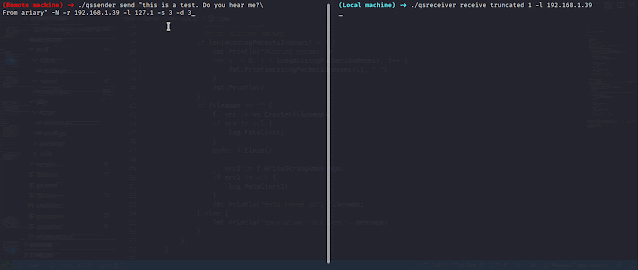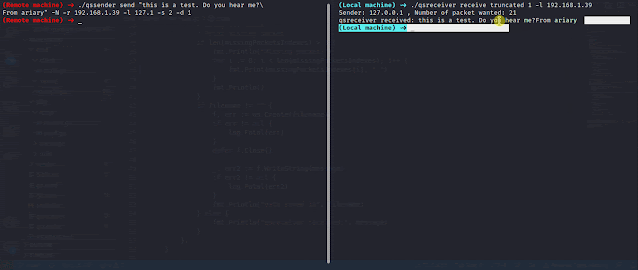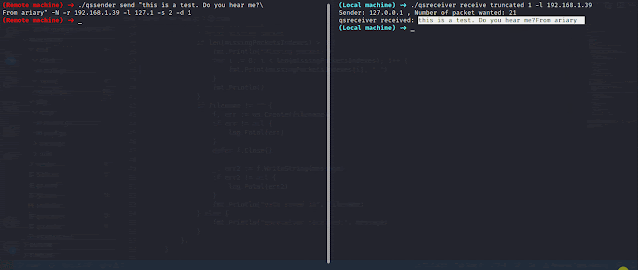
QueenSono: data exfiltration with ICMP protocol.
SharpStrike: post-exploitation tool written in C# that uses either CIM or WMI to query remote systems. It can use provided credentials or the current user's session.

BoobSnail allows generating XLM (Excel 4.0) macro. Its purpose is to support the RedTeam and BlueTeam in XLM macro generation. Features:
News

Attack via Zoho vulnerability
In September, there was an attack on one of the critical infrastructure facilities in the United States. The target was one of the largest ports - Houston, located in the Houston Shipping Canal, on the shores of the Gulf of Mexico. CISA and the FBI took part in the investigation of the incident, and they reported that the attacks were carried out by the famous ART using the zero-day vulnerabilities CVE-2021-40539 in Zoho. However, the attack has not yet been publicly attributed.
CISA has once again warned the public and congressmen about the threats, as the vulnerability has been exploited from August to the present, despite the fact that Zoho patched the hole back on September 8, when CISA issued the first warning about incidents with CVE-2021-40539.
Information in our previous post -> here

Clubhouse db leak
On one of the underground forums, a database of 3.8 billion phone numbers of users of the Clubhouse social network is exposed. The base itself is of little value, but one of the attackers combined it with the 533 million base of Facebook users' phone numbers. According to experts, such an enriched database can be used by cybercriminals in various attacks on user accounts.

The largest telecommunications provider in Afghanistan, Roshan, was attacked by Chinese APT, which for more than a year managed to merge gigabytes of technical data from its systems. The attacks highlight the particular interest of Chinese intelligence in the region.
Research
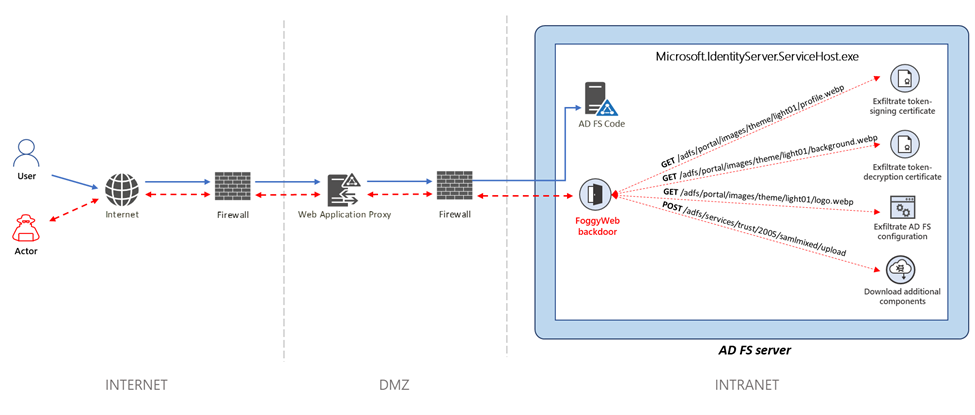
Microsoft Threat Intelligence Center (MSTIC) presented their research on the new FoggyWeb backdoor. This backdoor is actively used in attacks on AD FS servers by the NOBELIUM group, also known as APT29. According to experts, FoggyWeb is a highly targeted backdoor aimed at extracting confidential information from a compromised AD FS server. As part of its deployment, it can load additional components from an available command and control server (C2).

FinFisher research
Kaspersky Lab's researchers presented a report of the new version of FinFisher spyware, well-known as FinSpy and Wingbird. This system infection software uses a UEFI bootkit embedded in the Windows Boot Manager bootloader. This feature allows attackers to deploy malware without having to bypass firmware security checks.
HCRootkit / Sutersu Linux Rootkit Analysis: https://www.lacework.com/blog/hcrootkit-sutersu-linux-rootkit-analysis
The largest investigation in journalism history exposes a shadow financial system that benefits the world’s most rich and powerful. https://www.icij.org/investigations/pandora-papers
https://medium.com/@mazoka777/two-factor-authentication-bypass-4c814627f8c3
Privilege Escalation vulnerability in steam's Remote Play feature leads to arbitrary kernel-mode driver installation: https://vulners.com/hackerone/H1:852091
Malware Analysis in the Modern SOC: https://www.crowdstrike.com/blog/the-role-of-malware-analysis-in-the-modern-security-operations-center
DNS Tunneling Detection using Machine Learning and Cache Miss Properties: https://ieeexplore.ieee.org/document/9432279
Pass The Hash: What is? and how can we detect it? https://threathuntingreadings.com/home/f/pass-the-hash-what-is-and-how-can-we-detect-it
CobaltStrike Beacon Config Parsing with CyberChef: https://medium.com/@whickey000/cobaltstrike-beacon-config-parsing-with-cyberchef-malware-mondays-2-86d759b9a031
Feedback and Vulners docs
https://medium.com/@whickey000/cobaltstrike-beacon-config-parsing-with-cyberchef-malware-mondays-2-86d759b9a031
Feedback and Vulners docs
