LAW ENFORCEMENT SUCCESS and One patch: bunch of vulnerabilities
Recently, the number of vulnerabilities that come out in a single patch and the frequency of updates have been going up a lot. On the one hand it is great that vendors fix vulnerabilities fast enough, but on the other hand it is frightening to see more of them. Stay on the latest with Vulners!
- Vulnerabilities: Nagios, top vulns for ransomware, Microsoft can't patch their vulnerabilities and Netgear patch;
- Tools: QueenSono (data exfiltration), Secure Open-Source Password Manager, EXOCET, CopyCat;
- News: CISA alert, Europol and malware backdoor;
- Research: CLR research, reports and malware analysis.
Our feedback and Vulners docs
Vulnerabilities

Vulnerabilities pack
Researchers from Claroty an industrial cybersecurity company have discovered eleven vulnerabilities in widely used Nagios network management products. Vulnerabilities can lead to Server Side Request Forgery (SSRF), spoofing, local privilege escalation, remote code execution, and information disclosure. Nagios XI provides monitoring of all critical infrastructure components, including applications, services, operating systems, network protocols, system metrics, and network components.
The main ones are couple remote code execution vulnerabilities CVE-2021-37344 and CVE-2021-37346 in Nagios XI Switch Wizard and Nagios XI WatchGuard Wizard, SQL injection vulnerability CVE-2021-37350 in Nagios XI and request forgery on the side Server (SSRF), affecting the Nagios XI Docker master, as well as the post-authenticated RCE in the Nagios XI auto-discovery tool. Together, they provide the ability to reset the web shell or execute PHP scripts by elevating privileges to root, thus allowing arbitrary command execution.
Issues were fixed in updates released in August: Nagios XI 5.8.5 and higher, Nagios XI Switch Wizard 2.5.7 and higher, Nagios XI Docker Wizard 1.13 and higher, and Nagios XI WatchGuard 1.4.8 and higher.

Fix or destroy?
Updated Windows users report 0x0000011b errors when printing to network printers. This printing error is mostly seen in small businesses and home networks that cannot take advantage of the Kerberos configuration on a Windows domain. It's all about PrintNightmare - Windows Print Spooler Spoofing vulnerability CVE-2021-1678.
To fix recent 0x0000011b printing errors without uninstalling current Windows updates (KB5005565), you need to edit the registry key for CVE-2021-1678. To do this, in the registry key: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print, create a new 32-bit DWORD value named RpcAuthnLevelPrivacyEnabled and set it to 0.
When you change the value, you are no longer protected from the vulnerability, but it will allow you to print again. If that doesn't fix your problem, just go back to the default Windows settings.

Netgear critical patch
Netgear has patched a High Severity Remote Code Execution (RCE) vulnerability found in Circle Parental Controls, which runs as root on nearly a dozen modern Netgear Small Office / Home Office (SOHO) routers.
CVE-2021-40847 can be fixed by stopping the service, updating Circle, still contains a bug and is enabled by default, and the bug can be exploited even if the service is disabled.
Tools
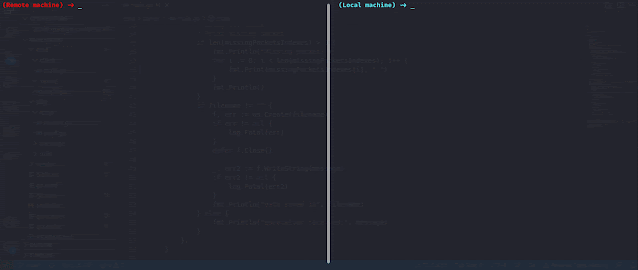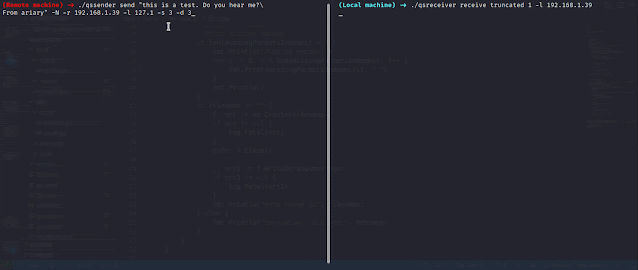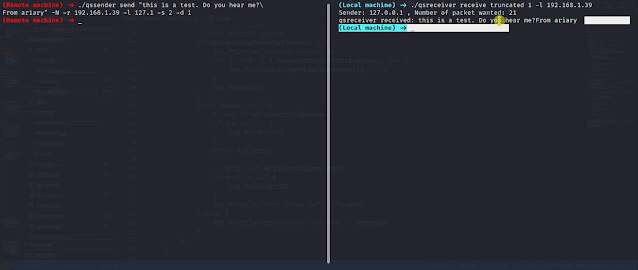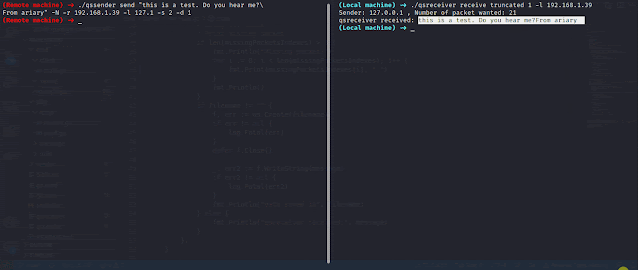
QueenSono: data exfiltration with ICMP protocol.
aes256_passwd_store: This script securely encrypts or decrypts passwords on disk within a custom database file.
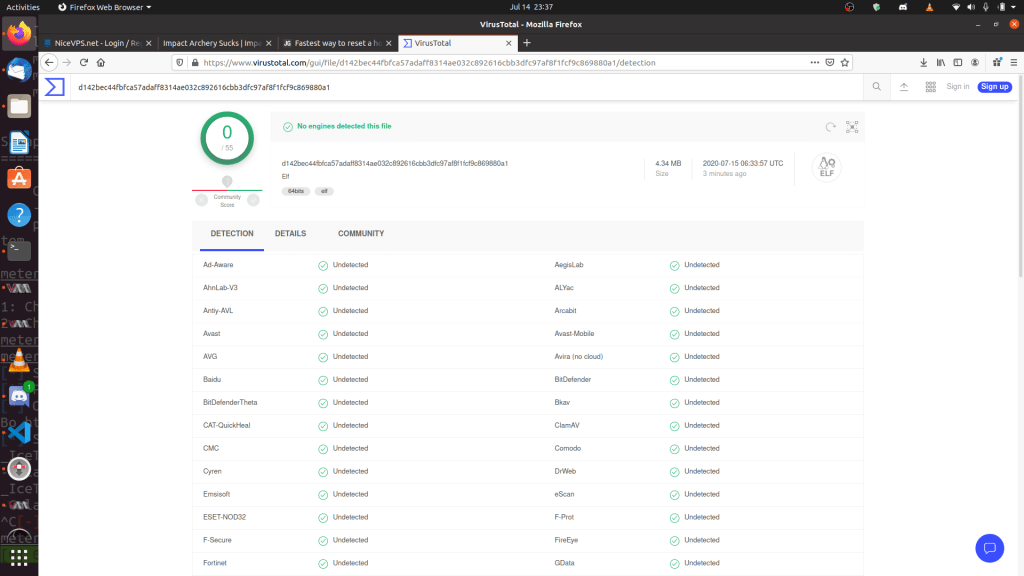
EXOCET: AV-evading, undetectable, payload delivery tool
News

The U.S. Cyber and Infrastructure Security Agency (CISA), the FBI and the NSA have issued a joint warning of an increase in cyberattacks using the Conti ransomware program. The warning says that Conti malware was used in attacks against more than 400 organizations in the United States and other countries. The warning includes technical information regarding malware, as well as recommendations to reduce the risk of hacking.

The Spanish and Italian authorities have dismantled a criminal group linked to the Italian mafia responsible for a large pool of cybercrimes ranging from online fraud to money laundering and other illegal e-commerce activities.
Law enforcement officers, together with Europol, made 106 arrests, conducted 16 home searches and froze 118 bank accounts. They seized various electronic devices, 224 credit cards, merchant terminals, SIM cards and more.
According to Europol, in 2020 alone, the criminal group earned about 10 million euros (approximately $ 11.7 million).

TinyTurla: Turla deploys new malware to keep a secret backdoor on victim machines
TinyTurla is a minor backdoor, as the malware is simple enough but capable of maintaining a long-term hidden presence on infected machines.
It is possible to hide the presence of malware in the Turla system by disguising it as the Windows Time Service. Once launched, it allows actors to fetch, load, and execute files, thus acting as a second-level dropper, if necessary of course. Moreover, it was noticed that malware every 5 seconds communicates with the command and control server via an encrypted channel to check for commands.
Research
https://twitter.com/kl\_secservices/status/1440271116593811467?s=20
iOS 15 iCloud Private Relay Vulnerability Identified: https://fingerprintjs.com/blog/ios15-icloud-private-relay-vulnerability
Account Persistence – Certificates: https://pentestlab.blog/2021/09/13/account-persistence-certificates
Technical Report: BluStealer Malware Threat: https://www.gosecure.net/blog/2021/09/22/gosecure-titan-labs-technical-report-blustealer-malware-threat
HCRootkit / Sutersu Linux Rootkit Analysis: https://www.lacework.com/blog/hcrootkit-sutersu-linux-rootkit-analysis
Our feedback and Vulners docs
cework.com/blog/hcrootkit-sutersu-linux-rootkit-analysis](https://www.lacework.com/blog/hcrootkit-sutersu-linux-rootkit-analysis)
Our feedback and Vulners docs
