Build exploits for zero-days and try to test their Confluence

Over the past week, the main zero-day vulnerabilities with unreleased patches from Microsoft, which, as usual, very quickly began to be exploited in the wild. And a couple of demonstrative news about why it is worth fixing vulnerabilities in your networks as quickly as possible.
- Vulnerabilities: Microsoft unpatched fail with exploit/PoC, Netgear devices, Android and Microsoft again;
- Tools: SharpStrike, Autoharness, Nettacker, Graphw00F;
- News: Jenkins confluence hacked via last vulnerability and Fortinet via old one;
- Research: Bug Bounty, research and article.
Feedback and Vulners docs
Vulnerabilities

CVE-2021-40444 with exploit
Microsoft has reported a critical RCE vulnerability CVE-2021-40444 in the MSHTML browser engine for Internet Explorer. An attacker who successfully exploited this vulnerability could create a malicious ActiveX control that the victim would run from a Microsoft Office document. CVE-2021-40444 is already being exploited in real attacks. As a temporary measure, the manufacturer recommends disabling ActiveX controls until security updates are released.
CVE-2021-40444 PoC
https://videopress.com/v/LkzkOYpw?resizeToParent=true&preloadContent=metadata
Several hacking forums have published tutorials on how to create a payload and a CAB file containing a vulnerability snippet (directory traversal) that anyone can use to create a working version of the exploit.

Vulnerable Netgear devices
3 critical security vulnerabilities PSV-2021-0140, PSV-2021-0144, PSV-2021-0145 were found in 20 different models of the GC, GS and MS series of various versions with an extremely high degree of risk, since it allows an attacker to control cloud storage and produce setting up equipment via the Internet.
The technical details and PoC for the two vulnerabilities have already been posted by Guinvael Coldwind:
- The first Demon's Cries vulnerability allows authentication bypass, which could allow an attacker to take control of a vulnerable device. The main condition for the scenario is the enabled Netgear Smart Control Center (SCC) function, which is disabled in the default configurations.
- The second Draconian Fear is defined as "Authentication Hijacking". To implement it, an attacker would need the same IP address as the administrator in order to "hijack session bootstrapping information." As a result of the attack, he will be able to gain full access to the device's web user interface, which will give him control over the device.
Details of the third vulnerability, dubbed Seventh Inferno, will only become available on September 13th.

Huge Android patch
Google has released patches for Android with fixes for as many as 40 vulnerabilities, 7 of which were deemed critical. The main problem lay in the security of the Framework component, including 6 critical vulnerabilities. These include five privilege elevation errors and one information disclosure vulnerability.
The most serious vulnerability is CVE-2021-0687, which poses a threat to Android 8.1, 9, 10, 11, allowing an attacker to cause permanent denial of service using a specially crafted file.

Zero-day vulnerability CVE-2021-40539
The US Cybersecurity Agency CISA warns of active exploitation of vulnerabilities in the Zoho ManageEngine ADSelfService.
ManageEngine ADSelfService is an integrated self-service password management and single sign-on solution for Active Directory in Microsoft Windows that allows administrators to use 2FA to sign in to applications and users to reset their passwords.
The vulnerability relates to the ability to bypass REST API authentication, which could lead to arbitrary code execution (RCE) and allow an attacker to take control of an affected system. Assemblies of ADSelfService Plus prior to version 6113 are at risk.
Tools
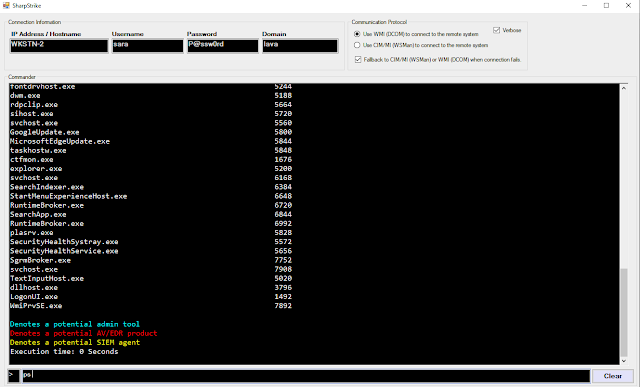
SharpStrike is a post-exploitation tool written in C# that uses either CIM or WMI to query remote systems. It can use provided credentials or the current user's session.
OWASP Nettacker now migrated to YAML-Based modules, many code enhancements and improvements, and x3 faster than before.
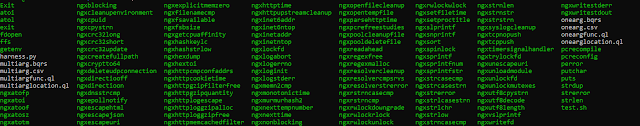
Autoharness is a tool that automatically generates fuzzing harnesses based on a library.
Graphw00F: GraphQL fingerprinting tool for GQL endpoints.
News

Jenkins Confluece
The exploitation of the CVE-2021-26084 vulnerability allowed hackers to gain access to the Jenkins internal server and deploy a cryptocurrency miner on it. At the moment, the developers have no reason to believe that the source code of the Jenkins software has been affected.
According to Censys, there are currently approximately 15,000 Atlassian Confluence servers on the web that can be accessed over the Internet. And as of September 5, 2021, 8,597 of those servers were still vulnerable to the CVE-2021-26084 issue.

Fortibet SSL-VPN vulnerability
Fortinet has confirmed the disclosure of SSL-VPN accounts to 87,000 FortiGate devices. The credentials were obtained by attackers by exploiting the old vulnerability CVE-2018-13379, which was patched in May 2019. The manufacturer recommends that organizations that have ever used the affected version perform a software update and reset their passwords.
Research
Hook Heaps and Live Free: https://www.arashparsa.com/hook-heaps-and-live-free
The babuk virus source code: https://git.disroot.org/Archive/Babuk
Feedback and Vulners docs
.com/watch?v=xOoWHKOphK0
The babuk virus source code: https://git.disroot.org/Archive/Babuk
Feedback and Vulners docs
