Keep in save your devices, patch critical systems and stay on the latest

Apparently this month there is a boom in vulnerabilities in various devices. Ransomware continues to be active, improving encryption methods and introducing new techniques in attacks. But even the largest vendors are determined, after all, it's not for nothing that they miss the pack of startups in recent months.
- Vulnerabilities: Gaming devices, Apple exploit, TOP Linus vulenrabilities, Annke Network Video Recorder and Cisco;
- Tools: dnsmonster, ACL visualizer, git secrets extractor, Android forensics toolskit.
- News: rare medical vulnerabilities, Google+Microsoft investment and non-typical ransomware,
- Research: mostly vulnerabilities, detection articles and ETW ptechnologies
Feedback and Vulners docs
Vulnerabilities

Razer and SteelSeries devices vulnerabilities
After discovering that Razer Synapse software could be used to elevate Windows privileges when connecting a Razer mouse or keyboard, security researcher Lawrence Amer discovered that the same result could be achieved when connecting SteelSeries devices.
Penetration tester Istvan Toth did not stop there and presented an attack vector that does not require a real Razer or SteelSeries device. He posted a script that can simulate Human Interface Device (HID) devices on Android, specifically for testing local privilege elevation (LPE) scenarios. SteelSeries and Razer said they are already working on fixing issues in their software.

Researchers at Citizen Lab discovered that an iMessage exploit called FORCEDENTRY was used to install Pegasus malware on the iPhones of Bahraini human rights defenders, politicians and dissidents. A key feature of the malware is the ability to bypass the BlastDoor sandbox designed to protect the processing of instant messaging data in iOS 14.4 and 14.6. For attacks on iOS 13.x, another exploit was used - KISMET, first discovered by the Citizen Lab team at the end of 2020.

TOP Linux vulnerabilities for Trend Micro
Trend Micro researchers presented an arsenal of hackers from the TOP 15 exploited vulnerabilities in Linux:
- CVE-2017-9805: Apache Struts 2, XStream RCE REST Plugin Vulnerability;
- CVE-2018-7600: Drupal Core RCE vulnerability;
- CVE-2020-14750: Oracle WebLogic Server RCE Vulnerability;
- CVE-2020-25213: RCE vulnerability in WordPress File Manager plugin (wp-file-manager);
- CVE-2020-17496: RCE Authentication Vulnerability in vBulletin subwidgetConfig;
- CVE-2020-11651: SaltStack Salt authorization bugs vulnerability;
- CVE-2017-12611: Apache Struts OGNL Expression RCE Vulnerability;
- CVE-2017-7657: Eclipse Jetty integer block length overflow vulnerability;
- CVE-2021-29441: Alibaba Nacos AuthFilter authentication bypass vulnerability;
- CVE-2020-14179: Atlassian Jira Information Disclosure Vulnerability;
- CVE-2013-4547: Nginx created a URI string access restriction bypass vulnerability;
- CVE-2019-0230: Apache Struts 2 RCE Vulnerability;
- CVE-2018-11776: Apache Struts OGNL Expression RCE Vulnerability;
- CVE-2020-7961: Liferay Portal Untrusted Deserialization Vulnerability.

Critical vulnerability was discovered by the researchers of Nozomi Networks at the Hong Kong manufacturer Annke, which offers solutions for home and business security to more than 5 million customers around the world. Nozomi Networks are profiled on industrial safety and security of IoT devices.
CVE-2021-32941 is based on a buffer overflow and can be used by an attacker to execute arbitrary code with root privileges and lead to a complete compromise of the device. Vulnerability in the Annke N48PBB Network Video Recorder (NVR), which is used to store and view streaming video and control cameras, which in operation allows access to recorded videos, delete footage, change configurations (for example, motion detection signals) and disable certain cameras or NVR to stop recording.
Cybersecurity agency CISA also stated that Annke NVR video surveillance systems are used all over the world. According to the manufacturer, the patch is available via a firmware update, therefore Annke customers are advised to update their business and personal devices as soon as possible.

Cisco new vulnerability
Cisco discovered a critical vulnerability and urgently released the corresponding patch. The threat concerns the Application Policy Infrastructure Controller (APIC) interface used in the Nexus 9000 series switches.
CVE-2021-1577 is associated with improper access control and allows an unauthenticated attacker to download a file to a device.
Cisco reported that discovered the vulnerability during internal security testing of its devices conducted by its own cyber defense group, the Cisco Advanced Security Initiatives Group. Public facts of exploitation have not yet been discovered, but not for long, right?
Tools

DNSMonster: Passive DNS collection and monitoring built with Golang, Clickhouse and Grafana: dnsmonster implements a packet sniffer for DNS traffic.
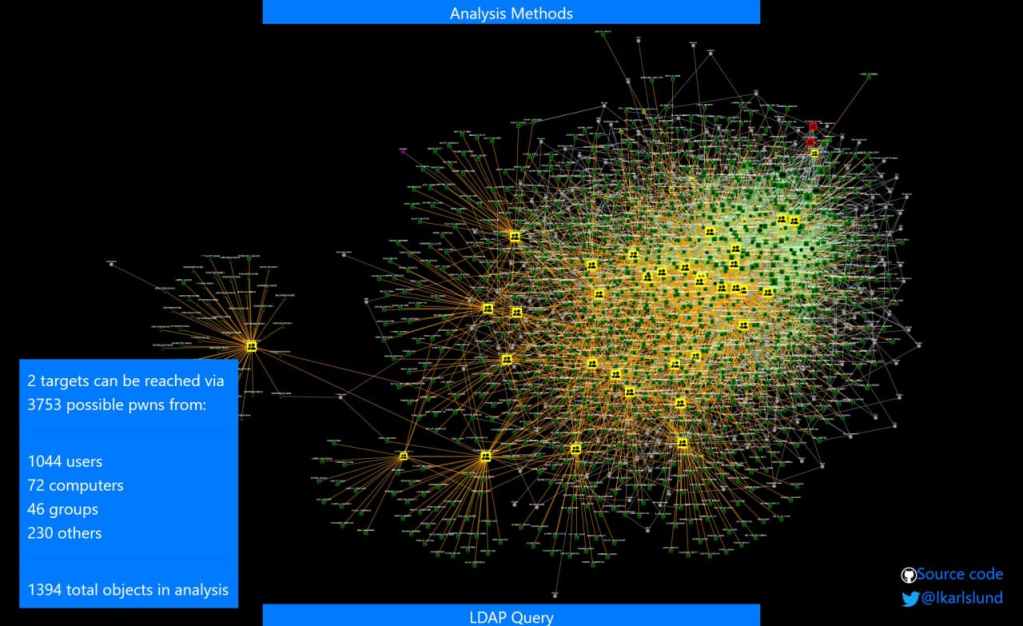
adalanche: Active Directory ACL Visualizer
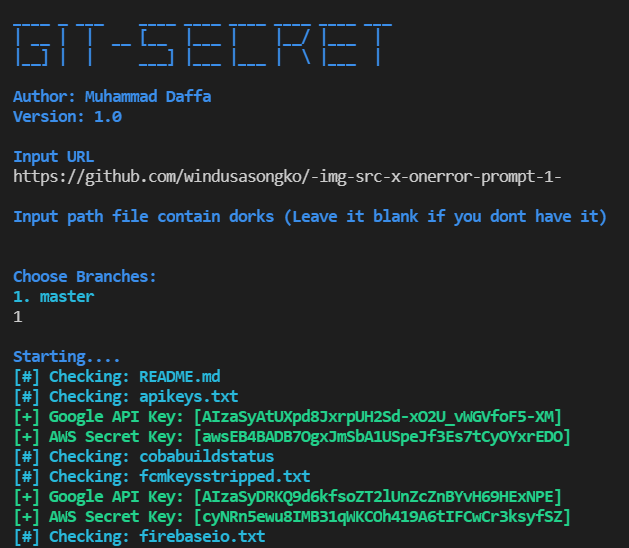
Git-Secret: Go scripts for finding an API key / some keywords in repository.
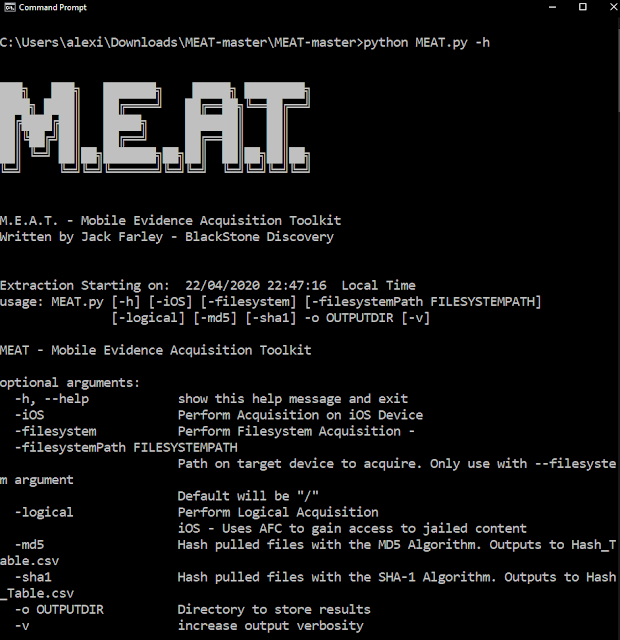
M.E.A.T. - Mobile Evidence Acquisition Toolkit
This toolkit aims to help forensicators perform different kinds of acquisitions on iOS devices (and Android in the future).
News

An infusion pump is a medical device intended for long-term, dosed, controlled administration to a patient of solutions, highly active drugs, and nutrients. B. Braun is one of the leaders in the supply of this equipment to medical institutions. According to McAfee research, in the event of exploitation of vulnerabilities, an attacker can modify the pump settings, thereby changing the dosage of drugs. The main problem is that the pump operating system does not validate the source of the commands, allowing remote attacks.

Google and Microsoft have pledged to invest $ 30 billion in US cybersecurity
Google will allocate about $ 10 billion - this money will go to hardware and security systems for the "software supply chain". Microsoft will invest almost 2 times more - $ 20 billion, and another $ 150 million on top of improving the security of government agencies.
According to vendors, this will be done in the next 5 years.
LockFile operators, actively exploiting ProxyShell and PetitPotam have adopted an advanced technology to bypass most of the standard ransomware defenses.
Malware uses discontinuous encryption when compromising Windows servers, which is usually deployed to speed up the encryption process. But unlike BlackMatter, DarkSide, and LockBit 2.0, which encrypt the first few bytes, LockFile works on all the other 16 bytes of the document. In fact, it looks like a text document remains partially readable and statistically looks like the original, but in fact it turns out to be broken, as a result the anomaly is not detected by a typical statistical analysis of encryption detection.
In addition, ransomware removes itself from the system after successfully encrypting all documents on the machine, leaving no trace of the binary at all.
Research
Cobalt Strike, a Defender's Guide: https://thedfirreport.com/2021/08/29/cobalt-strike-a-defenders-guide (lovely source)
Zoom RCE from Pwn2Own 2021 writeup: https://sector7.computest.nl/post/2021-08-zoom
How MarkMonitor left >60,000 domains for the taking: https://ian.sh/markmonitor?s=09
AWS privilege escalation: exploring odd features of the Trust Policy: https://rzepsky.medium.com/aws-privilege-escalation-exploring-odd-features-of-the-trust-policy-7a970a32861
Finding Detection and Forensic Goodness In ETW Providers: https://nasbench.medium.com/finding-detection-and-forensic-goodness-in-etw-providers-7c7a2b5b5f4f
Linux kernel tracing - "It`s hard to believe but linux kernel has almost exact copy of windows ETW - event tracing. It is just as difficult to make it work, it is poorly documented, very complex and fragile." http://redplait.blogspot.com/2021/08/linux-kernel-tracing.html
Feedback
poorly documented, very complex and fragile." http://redplait.blogspot.com/2021/08/linux-kernel-tracing.html
