Second Tuesday patches and several attacks in weekly news

The week of the second Tuesday of the month always sees a lot of important updates from various vendors. It's been a long time since our news section was bigger than Vulnerabilities. In the Research section you will traditionally find the most useful stuff that the author couldn't pass by.
Content:
- Vulnerabilities: Microsoft patch and unfixable print problem, SAP, Adobe;
- Tools: CyberChef update, privacy analyze tool, webshell generator, reverse engineering Android APK packages;
- News: ransomware attack, malware activity via new vulnerabilities;
- Research: videos and articles from Black and Hat + other research.
Feedback and Vulners docs
Vulnerabilities

Microsoft Tuesday patch
Microsoft released a patch this week that fixes 44 CVEs of which 7 are critical, 3 are zero-day, 37 are critical, 13 are remote code execution vulnerabilities, 8 deal with information disclosure, and most importantly, contain PrintNightmare fixes (which don't work :( ) and PetitPotam.
Zero-day vulnerabilities:
- CVE-2021-36948: Windows Update Medic privilege escalation vulnerability (according to Microsoft, only this vulnerability has been seen in the wild);
- CVE-2021-36942: Windows LSA spoofing vulnerability;
- CVE-2021-36936: Windows Print Queue Manager vulnerabilities.
PrintNightmare is again not fixed, but Microsoft was trying to do so. The security update changed the procedure to install a new printer driver requiring administrator privileges, such privileges would not be required to connect to a printer if this driver is already installed. If the driver exists on the client - the connection to the remote printer will be made by the CopyFile directive for users without administrator rights.
Fix didn't work again

ProxyShell vulnerabilities are exploited to install backdoors
Researchers warn that cybercriminals are attacking Microsoft Exchange servers using ProxyShell vulnerabilities and installing backdoors for subsequent access.
ProxyShell vulnerabilities were recently discussed at the Black Hat conference. ProxyShell combines three vulnerabilities that allow remote code execution without authentication on Microsoft Exchange servers. These vulnerabilities are exploited by Microsoft Exchange Client Access Service (CAS) running on port 443.
- CVE-2021-34473: Path Confusion without authentication leading to ACL bypass (fixed in April in KB5001779);
- CVE-2021-34523: Privilege escalation in Exchange PowerShell Backend (fixed in April in KB5001779);
- CVE-2021-31207: Writing arbitrary files after authentication, leading to remote code execution (fixed in May in KB5003435).
Researchers Kevin Beaumont and Rich Warren tweet that attackers have already moved from scans to proactive attacks and attacked their Microsoft Exchange honeypots using ProxyShell.

SAP has released a huge patch of fixes, covering 9 critical and especially critical vulnerabilities.
The most important:
- CVE-2021-33698: An issue with unlimited file uploads in SAP Business One. An attacker could exploit the script file loading vulnerability, suggesting that the vulnerability could be exploited to execute arbitrary code.
- CVE-2021-33690: SSRF server side request forgery affecting NetWeaver development infrastructure. An attacker could exploit a vulnerability for proxy attacks by sending specially crafted requests, and if the target instance is available on the Internet, could completely compromise sensitive data on the server and affect its availability.
- CVE-2021-33701: SQL injection in the SAP NZDT (Near Zero Downtime Technology) service used by S / 4HANA and the DMIS mobile plugin.
Other critical issues fixed by SAP include two cross-site scripting (XSS) vulnerabilities and an SSRF issue in the NetWeaver Enterprise Portal. XSS vulnerabilities affect two portal servlets and allow an attacker to inject JavaScript code into the corresponding pages. The code is executed in the victim's browser when she accesses the compromised servlet.
SSRF vulnerability allows an unauthorized attacker to make requests to internal or external servers, tricking the user into clicking a malicious link.

Adobe patched Magento vulnerabilities
Adobe has released the Patch Tuesday security update that addresses over 29 critical vulnerabilities that could lead to arbitrary code execution. 26 of them relate to Magento (the rest is Adobe Connect), 10 of which can be implemented without logging into the site, and some of these errors in preauth cause remote code execution and present security bypasses that allow you to control the site and its server.
Magento is one of the most popular E-commerce systems, integrated into over 100,000 online stores, 2,000 extensions and about 375,000 community members.
Tools
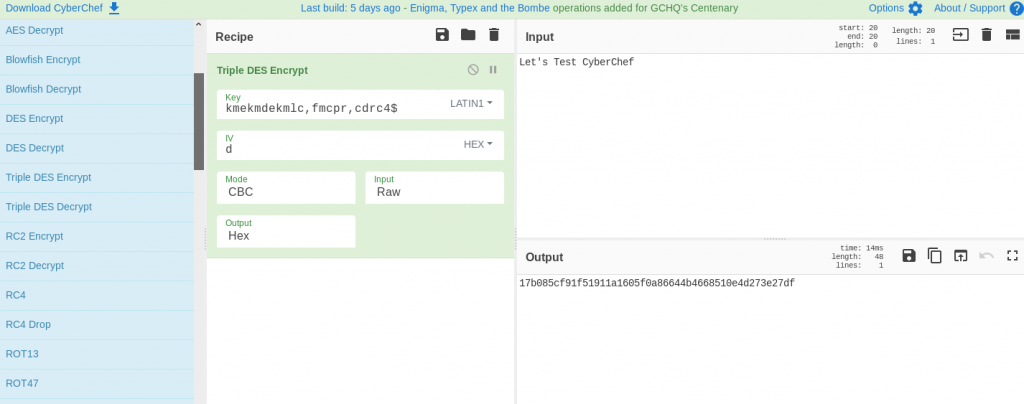
CyberChef 9.30 adds JA3 and JA3S support. Export your Client/Server Hello hex or bytes, calculate your JA3 hash and use HTTP Request to lookup via ja3er[.]com (or your own threat intelligence source)
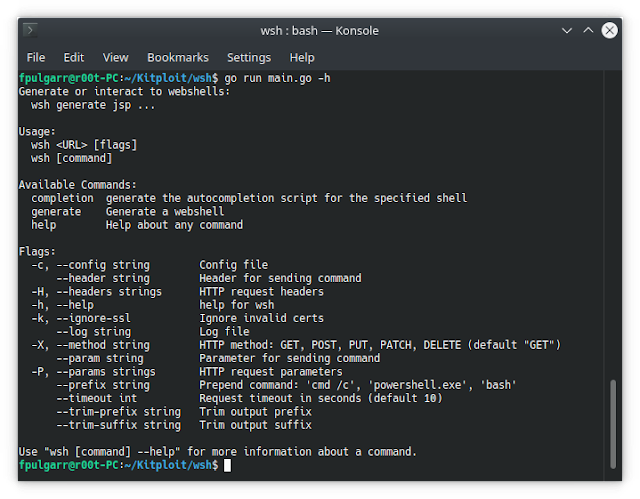
wsh is a web shell generator and command line interface. This started off as just an http client since interacting with webshells is a pain. There’s a form, to send a command you have to type in an input box and press a button. I wanted something that fits into my workflow better and ran in the terminal.
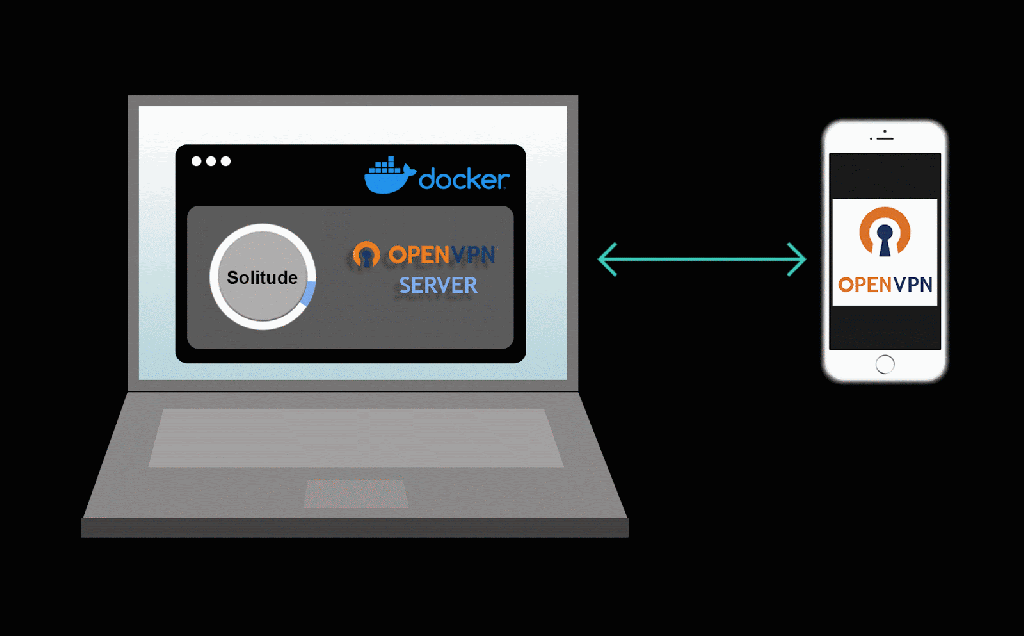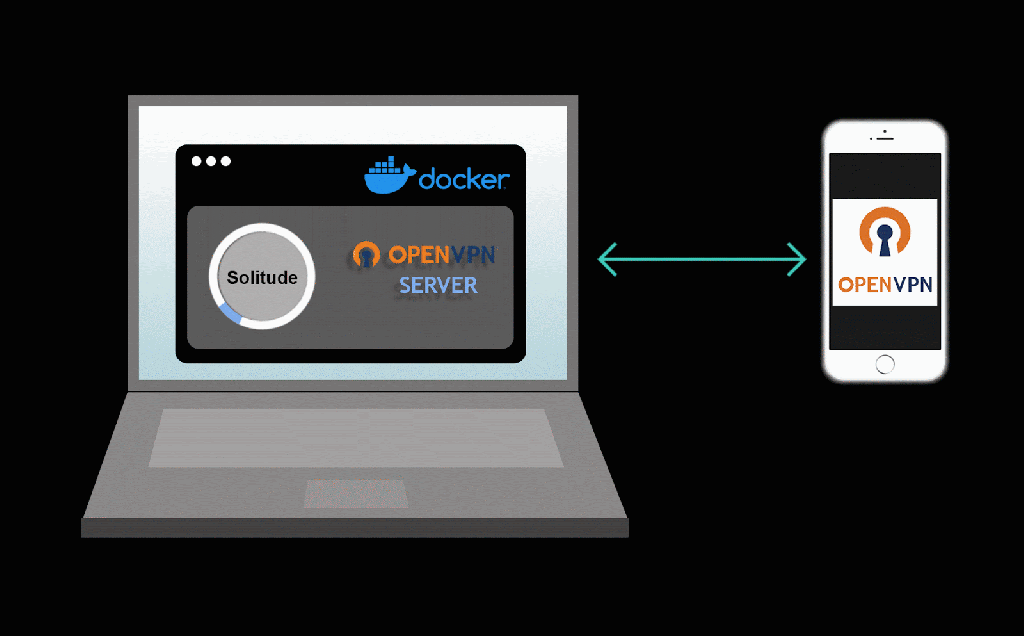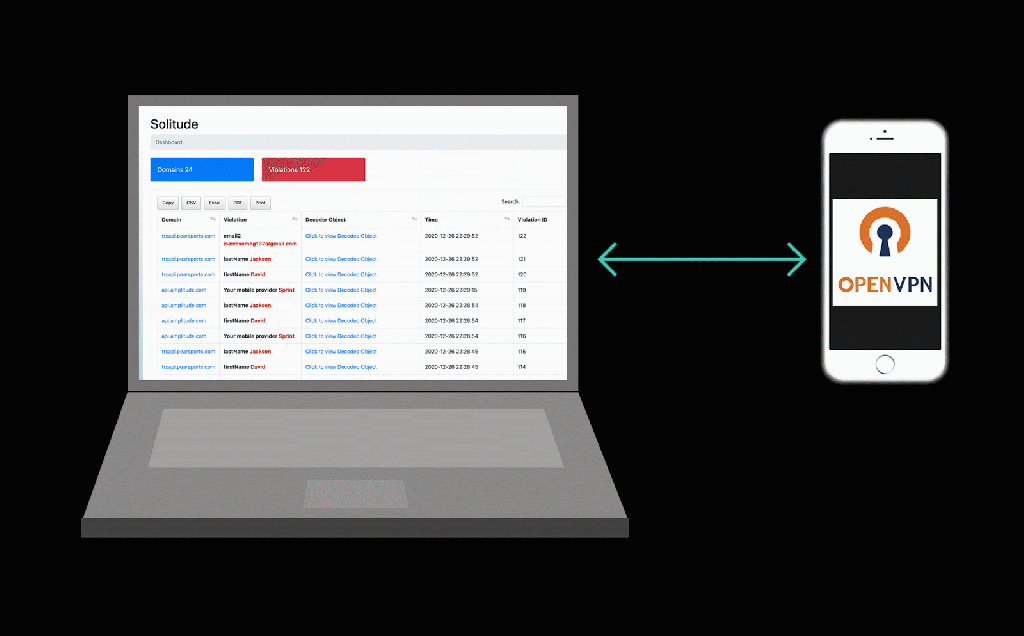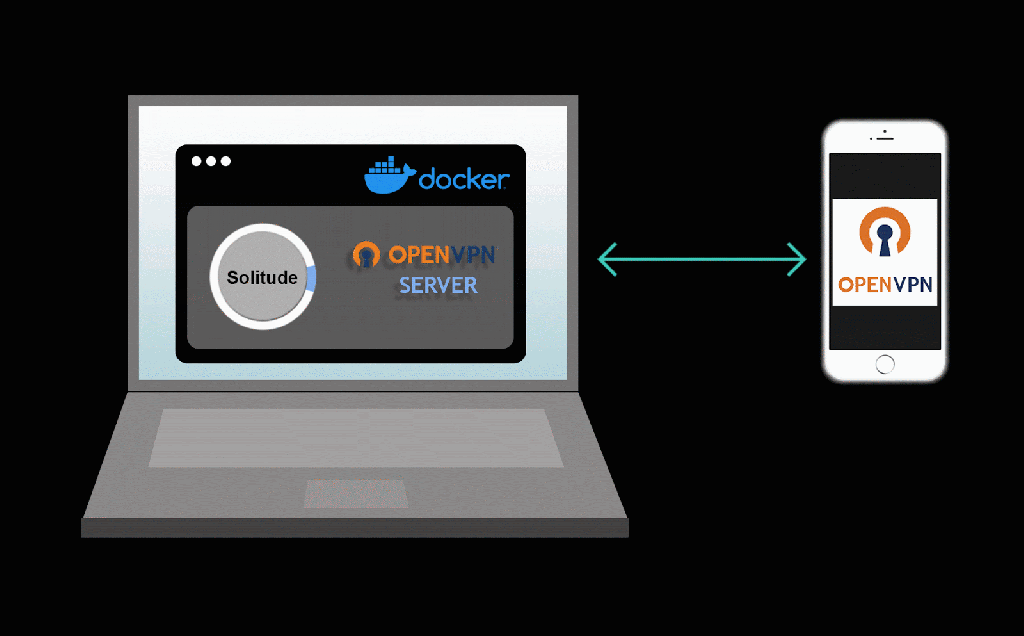
Solitude is a privacy analysis tool that enables anyone to conduct their own privacy investigations. Whether a curious novice or a more advanced researcher, Solitude makes the process of evaluating user privacy within an app accessible for everyone.

NinjaDroid is a simple tool to reverse engineering Android APK packages.
News

Mirai exploits a vulnerability affecting millions of routers with Arcadyan firmware.
Juniper Threat Labs have detected new attacks implemented by exploiting the critical CVE-2021-20090 vulnerability, which allows unauthenticated remote attackers to bypass authentication in the web interfaces of routers with Arcadyan firmware.
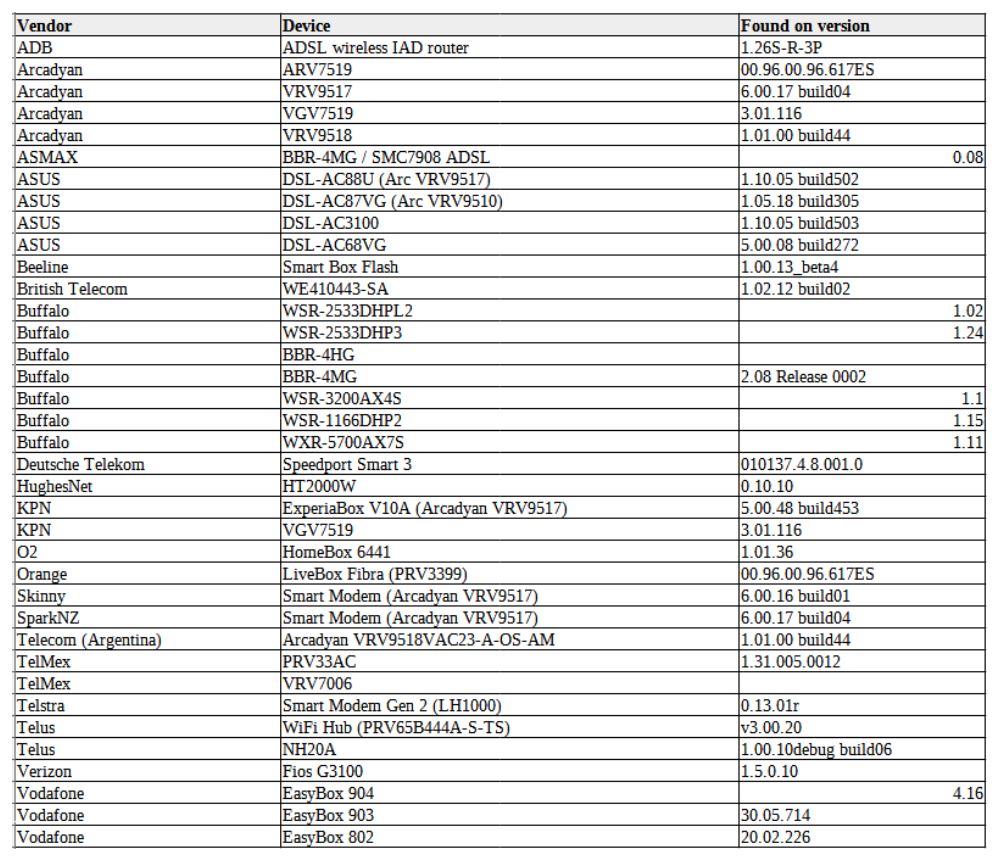
Hackers are attempting to extend vulnerable devices into their botnet via the critical CVE-2021-20090 vulnerability. Among the vulnerable devices there are dozens of router models produced by completely different companies: Asus, British Telecom, Deutsche Telekom, Orange, O2 (Telefonica), Verizon, Vodafone, Telstra and Telus. Since the breach affects many models and manufacturers of routers, experts believe that a total of millions of users could be at risk.
List of routers:

Less than 24 hours after the attack that stole $ 611 million in cryptocurrency from crypto platform Poly Network, attackers began recovering the stolen funds. This comes after experts from Slowmist published details of their investigation into the attack, which includes information that could help identify the perpetrators. Already $ 256 million in crypto-equivalents have been returned.

Gigabyte under ransomware attack
According to Bleeping Computer last week computer hardware company Gigabyte was attacked by RansomEXX encryption operators. Gigabyte representatives announced that a small part of servers was affected in the attack, and the affected IT infrastructure has already aisolated. However, experts believe that the attack could have been more extensive. The incident affected the work of several websites belonging to the company, including the support site and the website of the Chinese division. And the attackers threatened to release 112GB of stolen data from the organization.
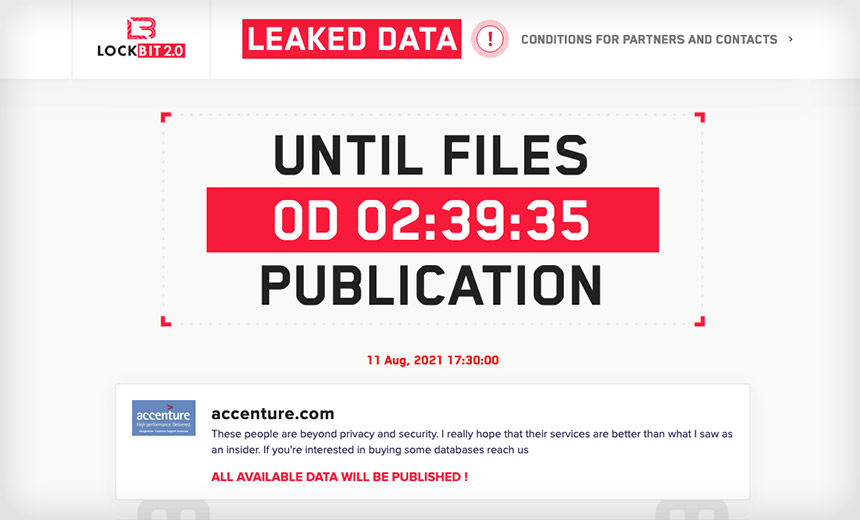
Accenture under ransomware attack
Global consulting company Accenture suffered a ransomware attack by LockBit CNN Business reports. An Accenture spokesperson confirmed that the company did have an IS incident, but the attacked assets have been recovered. Meanwhile, the LockBit darknet site posted information about the Accenture hack and threatened to release the stolen data unless a ransom was paid for it.
Research
The Red Team Vade Mecum https://kwcsec.gitbook.io/the-red-team-handbook
Weaponizing Middleboxes for TCP Reflected Amplification https://geneva.cs.umd.edu/posts/usenix21-weaponizing-censors
Learn about SUID, SGID and Sticky bits in detail practically with programs and how to drop privileges gracefully https://tbhaxor.com/demystifying-suid-and-sgid-bits
Successfully archived training materials for Conti partners - a selection of various Red Teaming videos, RedTeaming tools, malicious PowerShell scripts, etc. This is, in fact, Conti’s “continuous learning” program. https://pastebin.com/U71YVjjy
DLL reflection technique on Microsoft Windows to avoid EDR detection techniques:
https://bruteratel.com/research/feature-update/2021/06/01/PE-Reflection-Long-Live-The-King/?s=09
Feedback and Vulners docs
/01/PE-Reflection-Long-Live-The-King/?s=09](https://bruteratel.com/research/feature-update/2021/06/01/PE-Reflection-Long-Live-The-King/?s=09)
Feedback and Vulners docs
