Non-typically problems with PLCs and ransomware never gets bored

A couple of years ago, vulnerabilities in medical equipment were fantastic and incomprehensible. Over the past year, there has been a trend towards the exploitation of such equipment by ransomware. Accordingly, it is worth paying more attention to critical industrial systems and equipment, which are rarely updated by default.
Create your own automation vulnerability management process with Vulners and avoid such problems!
- Vulnerabilities: INFRA:HALT pack, Cisco patch, PwnedPiper and unfixable Mitsubishi controllers;
- Tools: Powershell for pentester, go-shellcode, collect IOS from Twitter and Tshark+ELK stack;
- News: Conti leaksand and LockBit 2.0 recruiting corporate insiders;
- Research: InfoSec videos, new research articles and reports.
Feedback and Vulners docs
Vulnerabilities

Researchers from JFrog and Forescout presented in a joint report the sixth INFRA:HALT set of 14 vulnerabilities in the NicheStack stack (that is already 4 - part of a research initiative called Project Memoria), affecting a widely used stack in millions of Operational Technology (OT) devices deployed in manufacturing plants.
NicheStack is a closed-source TCP/IP stack for embedded systems that is designed to provide Internet connectivity to industrial equipment and is used by major industrial automation integrators (Siemens, Emerson, Honeywell, Mitsubishi Electric, Rockwell Automation and Schneider Electric) in their programmable logic controllers and other products.
Successful attacks can disable ICS devices and hijack their logic. Hijacked devices can spread malware on the network where they exchange data. All versions of NicheStack prior to 4.3 are vulnerable to INFRA:HALT. The bugs affect more than 6,400 OT devices, most of which are located in Canada, the United States, Spain, Sweden and Italy.

Cisco fixed dangerous vulnerabilities in RV160, RV260 and RV340 series VPN routers. Both bugs are contained in routers web interface and are related to incorrect checking of HTTP requests.
- CVE-2021-1609 affects RV340 allowing an unauthenticated attacker to remotely execute code on the device (RCE);
- CVE-2021-1602 also allows an unauthenticated user to achieve RCE.
Cisco states that they have not observed exploitation of these vulnerabilities in the wild. If you use vulnerable routers, install updates urgently.

PwnedPiper vulnerabilities
Researchers at the armis cybersecurity company have uncovered a set of nine critical PwnedPiper vulnerabilities affecting the infrastructure of more than 80% of all hospitals in North America (about 2300) and no less than 3000 hospitals around the world.
PwnedPiper lets an unauthorized attacker hijack Translogic PTS stations and take full control of the target hospital's PTS network by implementing MitM. Subsequently - the ability to steal confidential information or roll ransomware. In addition, errors allow an attacker to gain a foothold on compromised PTS stations due to an unsafe firmware update procedure leading to unauthenticated remote code execution.
The vulnerabilities are mainly related to privilege escalation, memory corruption and denial of service:
- CVE-2021-37161 - insufficient amount of resources in udpRXThread;
- CVE-2021-37162 - overflow in sccProcessMsg;
- CVE-2021-37163 - two hard-coded passwords available via Telnet server;
- CVE-2021-37164 - triple stack overflow in tcpTxThread;
- CVE-2021-37165 - overflow in hmiProcessMsg;
- CVE-2021-37166 - Denial of Service DoS caused by the Nexus Control Panel GUI process binding a local service on all interfaces;
- CVE-2021-37167 - custom script run by root can be used for PE;
- CVE-2021-37160 - firmware update without authentication, without encryption and without signature.
Swisslog Healthcare recognizes the malicious potential of PwnedPiper and is offering customers the Nexus Control Panel version 7.2.5.7 patch. At the same time, the current firmware update does not eliminate all vulnerabilities, namely the most serious error CVE-2021-37160 will be fixed only in one of the next versions.

Mitsubishi vulnerable controllers
Vulnerabilities affect the authentication mechanism in the MELSEC communication protocol, which is used to exchange data with target devices by reading and writing data to the CPU module, and include:
- CVE-2021-20594: user names used during authentication are effectively brute-force;
- CVE-2021-20598: the bruteforce protection system severely restricts any network activity for an extended period of time at the slightest attempted attack, blocking access to legitimate users;
- CVE-2021-20597: leaked password-equivalent secrets can facilitate successful authentication with PLCs; and transmitting session tokens in plaintext that are not tied to an IP address, allowing an attacker to reuse the same token from a different IP address after it has been generated.
The Nozomi Networks report did not provide technical details of the vulnerabilities or PoC code to demonstrate the attacks to avoid possible malicious consequences.
Tools

PowerShell Armoury is meant for pentesters, “insert-color-here”-teamers and everyone else who uses a variety of PowerShell tools during their engagements. It allows you to download and store all of your favourite PowerShell scripts in a single, encrypted file.

go-shellcode is a repository of Windows Shellcode runners and supporting utilities. The applications load and execute Shellcode using various API calls or techniques.
TwiTi is a tool for extracting IOCs from tweets, can collect a large number of fresh, accurate IOCs.
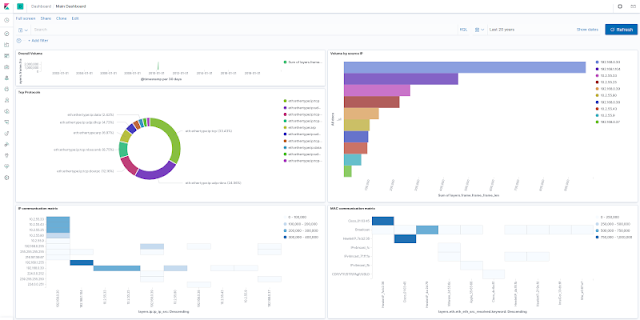
Tshark + ELK Analytics Virtual Machine project builds virtual machine which can be used for analytics of tshark -T ek (ndjson) output. The virtual appliance is built using vagrant, which builds Debian 10 with pre-installed and pre-configured ELK stack.
News
Conti leak
A disgruntled participant in the ransomware "affiliate program" Conti has leaked manuals and technical manuals used by hackers to train their "partners" into the network. The docs tell you how to access someone else's network, side-move, expand access, and then steal data before encrypting it.
Conti operates under the Ransomware-as-a-Service (RaaS) scheme. That is, malware developers are directly involved in malware and payment sites, and their hired "partners" hack victims' networks and encrypt devices. As a result, the ransom payments are distributed between the hack group itself and its "partners", and the latter usually receive 70-80% of the total amount.

LockBit ransomware developers are looking for insiders to penetrate corporate networks
The authors of the LockBit 2.0 ransomware are actively recruiting corporate insiders who can help hack and encrypt companies' networks. In return, insiders are promised a "fee" of a million dollars. LockBit ransomware was renamed LockBit 2.0 in June of this year. At the same time, the criminals announced the launch of a new RaaS program, presented updated Tor sites, as well as numerous new features, including automatic encryption of devices on the victim's network using group policies.
At the same time, in a ransom note that the malware automatically leaves on the victims' machines, information appeared that LockBit was recruiting insiders. The hackers write that they are interested in people with access to RDP, VPN, corporate email credentials, and promise insiders a "fee" of a million dollars.
picture
When experts first noticed this message, it seemed illogical to them that hackers were looking for insiders in already hacked networks. However, it appears that this message is not addressed to the employees of the affected companies, but to external IT consultants who can be recruited to investigate LockBit attacks and minimize their consequences.
Research
Amazing telemetry enrichment for SOC teams: https://blog.virustotal.com/2021/08/introducing-known-distributors.html
Unfixable Microsoft features: https://github.com/cfalta/MicrosoftWontFixList/blob/main/README.md
SEC505: Securing Windows and PowerShell Automation Scripts: https://blueteampowershell.com
https://youtube.com/playlist?list=PLiVfOzljj-46a1csp9aeG5GPOoTca2P2U
The Ultimate Guide to Phishing: https://sidb.in/2021/08/03/Phishing-0-to-100.html
Portable Executable Injection Study: https://malwareunicorn.org/workshops/peinjection.html#0
ADCS + PetitPotam NTLM Relay: Obtaining krbtgt Hash with Domain Controller Machine Certificate.
Feedback and Vulners docs
ty-experiments/active-directory-kerberos-abuse/adcs-+-petitpotam-ntlm-relay-obtaining-krbtgt-hash-with-domain-controller-machine-certificate)
Feedback and Vulners docs
