Underestimated news of the month in one review + new Vulners service

The Vulners team presented a new service Vulners scanner for WordPress (plugin) this month. Everyone who signs up before the end of August will receive a free lifetime license of the Vulners API for WordPress Vulners plugin!
And according to tradition - every first Monday of the month publishes a monthly digest on events in the world of information security. In this digest, we included all the bright vulnerabilities that we did not write about and there were a lot of them, so we have the shortest "News" block for all the time of monthly digests.
Enjoy!
- Vulnerabilities: too old problem in many printers, couple vulnerabilities for WordPress, few zero-days and TOP exploitable vulnerabilities;
- Tools: Hash-Buster v3.0, Beaconator, Regexploit and Ppmap;
- News: Coursera problems and couple update for strong malware;
- Research: useful stuff.
Vulnerabilities

16 Years Old Vulnerability Affects Millions of HP, Samsung and Xerox Printers
SentinelOne researchers discovered a critical CVE-2021-3438 buffer overflow vulnerability in the SSPORT.SYS driver, exploitation of which can lead to local user privilege escalation. The driver is automatically installed with the printer software and is loaded into Windows every time the system starts up. A list of printer models that use the vulnerable driver can be found in the HP Security Bulletin and the Xerox Security Bulletin.

Automattic's popular WooCommerce and WooCommerce Blocks plugins for WordPress have been fixed a critical bug. Until the release of the patch, more than 5 million sites remained vulnerable. Both plugins have been updated to version 5.5.1. The hotfix addresses a flaw in two PHP files that allowed malicious code to be injected into SQL statements without the need for authentication. An attacker who successfully exploited this SQL injection vulnerability could obtain store information, administrative data, and order and customer data.
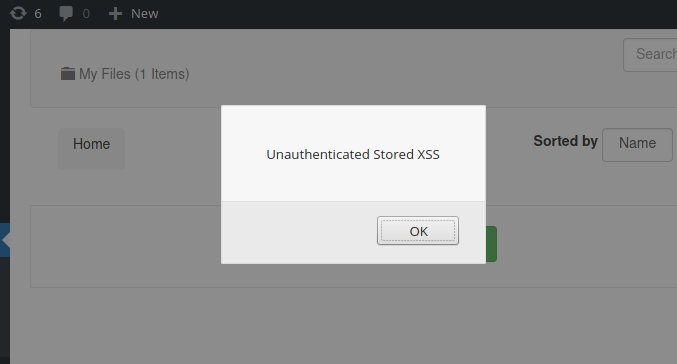
XSS in the Frontend File Manager plugin
Critical cross-site scripting (XSS) vulnerabilities were found in WordPress, allowing attackers to inject JavaScript code into web pages and create admin accounts. The problem lies in the Frontend File Manager plugin - it's the one that contains the bugs. Experts reported a total of six vulnerabilities affecting plugin versions 17.1 and 18.2. According to researchers' estimates, the vulnerable Frontend File Manager plugin is installed on more than 2,000 web resources.
It turned out that the root of the problem lies in the function "wpfm_edit_file_title_desc", which is activated when editing a post on a WordPress-site. The function itself could not identify the authorship of the person who was editing the post. As a result, an unauthenticated user was free to change content and titles on any pages.
All users using Frontend File Manager are advised to install plugin version number 18.3, which was released on June 26.

TOP 30 vulnerabilities
The U.S., UK and Australian cybersecurity agencies have published the top 30 most exploited vulnerabilities in real-world attacks over the past two years. The bulletin contains information about updates and potential solutions to problems and indicators of compromise detected as part of such attacks. It is worth noting that this top list includes vulnerabilities published back in 2017 and 2018.

Updating iOS, iPadOS and MacOS, as it turned out, fixes another 0-day vulnerability CVE-2021-30807 in the IOMobileFramebuffer kernel extension.
The vulnerability leads to remote code execution (RCE), and even with kernel privileges. But the most dangerous thing is that, according to Apple, "according to one of the reports, the vulnerability may be actively exploited in the wild." True, no more data on this operation is provided.
It is recommended to quickly update your apple devices!

Vulnerabilities in the Zimbra corporate email client could allow an attacker to gain unlimited access to the organization's sent and received email messages. According to specialists from SonarSource, exploitation of the problems allows an unauthorized attacker to break into an organization's mail server and gain access to all employee email messages.
CVE-2021-35208 is a cross-site scripting execution (XSS) vulnerability based on the DOM programming interface. The vulnerability can be exploited when a victim views an incoming email with special JavaScript code.
A server-side request spoofing vulnerability CVE-2021-35209 was also discovered. An attacker could exploit both vulnerabilities and obtain tokens and user credentials.

Chrome cero-day
Google has released security updates for the Chrome browser. This patch fixes a zero-day vulnerability that cybercriminals exploit in cyberattacks. Thus, since the beginning of 2021, the developers have already fixed the eighth 0-day bug.
CVE-2021-30563 is described as a type confusion in the V8 scripting engine. As a component of Chrome, V8 is responsible for running and processing JavaScript code.
The 0-day list for 2021 is as follows:
- CVE-2021-21148 - Chrome 88.0.4324.150, February 4th;
- CVE-2021-21166 - Chrome 89.0.4389.72, March 2;
- CVE-2021-21193 - Chrome 89.0.4389.90, 12 March;
- CVE-2021-21220 - Chrome 89.0.4389.128, April 13;
- CVE-2021-21224 - Chrome 90.0.4430.85, April 20;
- CVE-2021-30551 - Chrome 91.0.4472.101 June 9th;
- CVE-2021-30554 - Chrome 91.0.4472.114 June 17.

Researcher Gilles Lionel recently discovered a vulnerability that allows initiating the authentication process on behalf of a remote server. In this way, an attacker can obtain NLTM authentication data. The problem affects the MS-EFSRPC protocol, which is used in the system to manage encrypted data on remote servers. The specialist notes that disabling MS-EFSRPC support does not solve the problem. Microsoft, in its turn, published an article with a temporary solution to the problem.
Tools
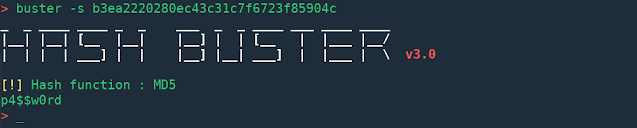
Hash-Buster v3.0 - Crack hashes in seconds
Features
- Automatic hash type identification
- Supports MD5, SHA1, SHA256, SHA384, SHA512
- Can extract & crack hashes from a file
- Can find hashes from a directory, recursively
- Multi-threading
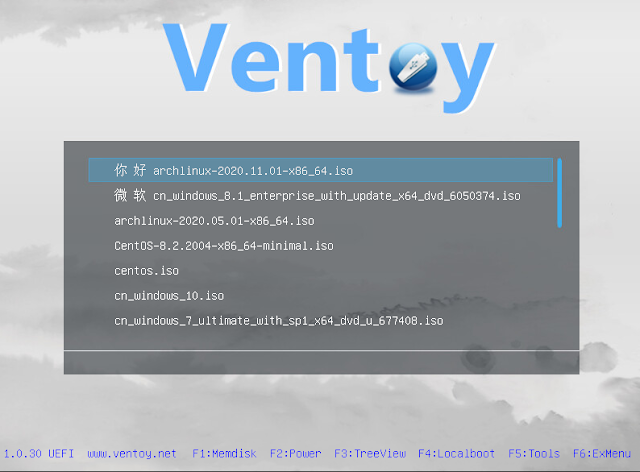
Ventoy is an open source tool to create bootable USB drive for ISO/WIM/IMG/VHD(x)/EFI files.
With ventoy, you don’t need to format the disk over and over, you just need to copy the image files to the USB drive and boot it. You can copy many image files at a time and ventoy will give you a boot menu to select them.

Sharperner is a tool written in CSharp that generate .NET dropper with AES and XOR obfuscated shellcode. Generated executable can possibly bypass signature check but I cant be sure it can bypass heuristic scanning.

GDir-Thief: Red Team tool for exfiltrating the target organization’s Google People Directory that you have access to, via Google’s People API.
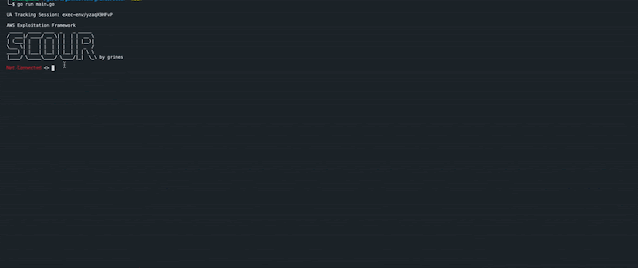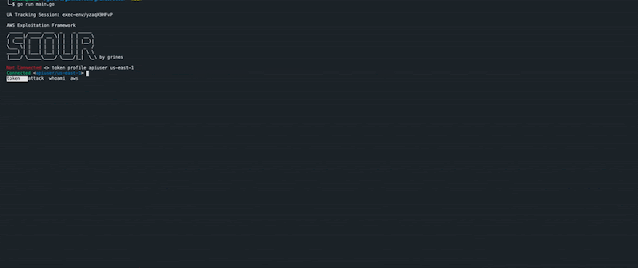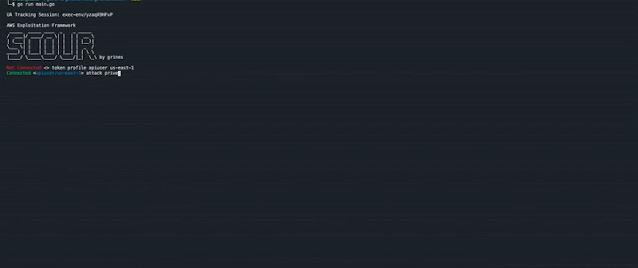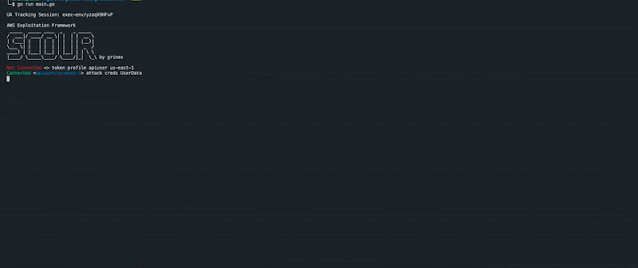
Scour is a modern module based AWS exploitation framework written in golang, designed for red team testing and blue team analysis. Scour contains modern techniques that can be used to attack environments or build detections for defense.
News

Researchers uncovered vulnerabilities in the API on the Coursera platform.
The company works with more than 200 universities and companies, including Stanford University, Duke University, Google, Cisco and IBM. Researchers found numerous bugs in the API, including an enumeration bug, resource limitations related to GraphQL and REST APIs, and misconfiguration of GraphQL.
The main problem was the BOLA (Broken Object Level Authorization) vulnerability because it was easy to exploit.
Researchers reported the vulnerabilities to the platform on October 5, 2020. By December 18, they released a patch that partially fixed the bugs. However, one vulnerability required additional testing, which delayed the final bug fix until May 24.

Trend Micro this month published a research the updated BIOPASS malware with new features
Researchers have found that a seemingly common Remote Access Trojan (RAT) in Python has a completely new feature that no other malware has: it streams video from victims' screens. The feature is implemented thanks to the use of OBS Studio RTMP (Real Time Messaging Protocol) to record the user's screen and broadcast it to the attacker's control panel.
Trojan was discovered during an investigation into attacks on Chinese gambling sites. The RAT masqueraded as the Adobe Flash Player or Microsoft Silverlight distributions, which are still in use in China, despite the fact that they have expired. Infected installers were distributed via malicious JavaScript on the technical support pages of game resources.
Despite the lack of official attribution, Trend Micro said China's Winnti or APT41 was involved in the BIOPASS attacks, which matches its style. As you know, in addition to cyber espionage, the hackers' sphere of interests also included online gaming companies throughout Southeast Asia.
LemonDuck malware
Microsoft recently published their research in 2 parts. The already well-known malware continues to actively improve and use Windows and Linux systems as targets.
Today it is actively developed and regularly updated malware. LemonDuck is primarily known for its mining purposes. After some time, he has evolved in his actions: stealing passwords, exploiting many known vulnerabilities, disabling security tools, and other features. Ultimately capable of being used as a backdoor and delivering additional human-controlled tools.
One of the main features of LemonDuck is stripping extraneous malware / miners from a compromised device, getting rid of its competitors. It also fixes vulnerabilities that have already been used to gain access to the system.
In their research, Microsoft also describes LemonCat, which is associated with LemonDuck. Experts believe that LemonCat is a targeted interpretation of its predecessor, has different purposes and is used for more dangerous operations. The new version is active from January 2021. A distinctive feature is that it was used in attacks on vulnerable Microsoft Exchange servers and these incidents led to the installation of a backdoor, information theft, followed by the installation of the Ramnit Trojan.
Research
NTLM relaying to AD CS - On certificates, printers and a little hippo: https://dirkjanm.io/ntlm-relaying-to-ad-certificate-services
Supply-Chain attack via Python.
As many as eight Python packages that were downloaded more than 30,000 times have been removed from the PyPI portal for containing malicious code, once again highlighting how software package repositories are evolving into a popular target for supply chain attacks. https://vulners.com/thn/THN:0F51157CFD66AE6ACFDC682A4632092D
Detecting LDAP enumeration and Bloodhound‘s Sharphound collector using Active Directory Decoys: https://medium.com/securonix-tech-blog/detecting-ldap-enumeration-and-bloodhound-s-sharphound-collector-using-active-directory-decoys-dfc840f2f644
meration-and-bloodhound-s-sharphound-collector-using-active-directory-decoys-dfc840f2f644)
