Weekly Digest: How many patches does it take to fix one vulnerability? And for more?

Microsoft has made several attempts since June, but the author of the mimikatz continues to bypass all the patches. Likewise, other vendors have tried to close a bunch of zero-day vulnerabilities, so you can protect yourself (or not) from ransomware.
Even though the most dangerous of ransomware gangs are out, most of them continue to evolve and upgrade. More power and more money $$$ :)
- Vulnerabilities: Microsoft monthly patch, Google zero-days, SolarWinds again and SAP critical patch from ransomware;
- Tools: Attack and Defense staff;
- News: REvil out, TrickBot evolution and SonicWall alarm;
- Research: REvil, TrickBot and SonicWall alarm.
Feedback and Vulners docs
Vulnerabilities

Microsoft patch Tuesday July 2021
Microsoft has patched a total of 117 security vulnerabilities, including 9 zero-day vulnerabilities that are exploited in the wild. Updates cover Windows, Bing, Dynamics, Exchange Server, Office, Scripting Engine, Windows DNS, and Visual Studio Code.
The fixed zero-day vulnerabilities also affect:
- Microsoft Exchange Server: CVE-2021-34473 - RCE and CVE-2021-34523 - privilege escalation;
- Active Directory: CVE-2021-33781 - security feature bypass;
- Windows ADFS: CVE-2021-33779 - security feature bypass;
- Windows: CVE-2021-34492 - forging certificates and CVE-2021-34458 - remote code execution;
- Windows DNS Server: CVE-2021-34494 - remote code execution.
And of course, the patch includes the problematic print spooler CVE-2021-34527, which again does not fix the vulnerability 100%. The best way to prevent this vulnerability is to restrict Point and print to a list of approved trusted servers!

Google released technical details on four zero-day vulnerabilities that were used this year for targeted hacker attacks. Exploitation of vulnerabilities was used to attack users of Chrome, Internet Explorer and Safari for iOS browsers.
- CVE-2021-21166 and CVE-2021-30551 in Chrome,
- CVE-2021-33742 in Internet Explorer
- CVE-2021-1879 in WebKit (Safari).

SolarWinds has released security updates that resolve CVE-2021-35211. The bug has traditionally been effectively exploited in the wild, until Microsoft started sounding the alarm.
The vulnerability is a RCE remote code execution bug in Serv-U file transfer technology up to and including 15.2.3 HF1, which can be exploited over SSH to run malicious code with elevated privileges in SolarWinds applications. Its implementation allows you to install programs, modify or delete data, or run programs on a vulnerable system. Serv-U technology is of limited use and has been used exclusively in Serv-U Managed File Transfer and Serv-U Secure FTP products.

SAP has released 12 security fixes
- CVE-2021-33671: authorization without check affects SAP NetWeaver Managed Procedures (SAP GP) in the Composite Application Framework (CAF), which provides access to back-end systems. Lack of authorization was detected in the centralized administration tool for GP and could lead to unauthorized access and data manipulation.
- CVE-2021-33670: Denial of Service is associated with the incorrect operation of Java (http-service) in SAP NetWeaver AS and allowed a potential attacker to manipulate HTTP requests, causing a denial of service state.
SAP also released nine vulnerability fixes for CRM ABAP, NetWeaver AS ABAP and ABAP Platform, Lumira Server, Web Dispatcher and Internet Communication Manager, NetWeaver AS for Java (Enterprise Portal), Business Objects Web Intelligence (BI Launchpad), and 3D Visual Enterprise Viewer.
In addition, the company has released updates for Hot News, one for the Chromium browser in the SAP Business Client, and the other for the NetWeaver ABAP Server and ABAP Platform.
Tools
Ventoy: is an open source tool to create bootable USB drive for ISO/WIM/IMG/VHD(x)/EFI files.

Bughound: is an open-source static code analysis tool that analyzes your code and sends the results to Elasticsearch and Kibana to get useful insights about the potential vulnerabilities in your code.
Redteam-Hardware-Toolkit is a collection of hardware s that aid in red team operations. This repository will help you during red team engagement. If you want to contribute to this list send me a pull request.

sx is the command-line network scanner designed to follow the UNIX philosophy.
News
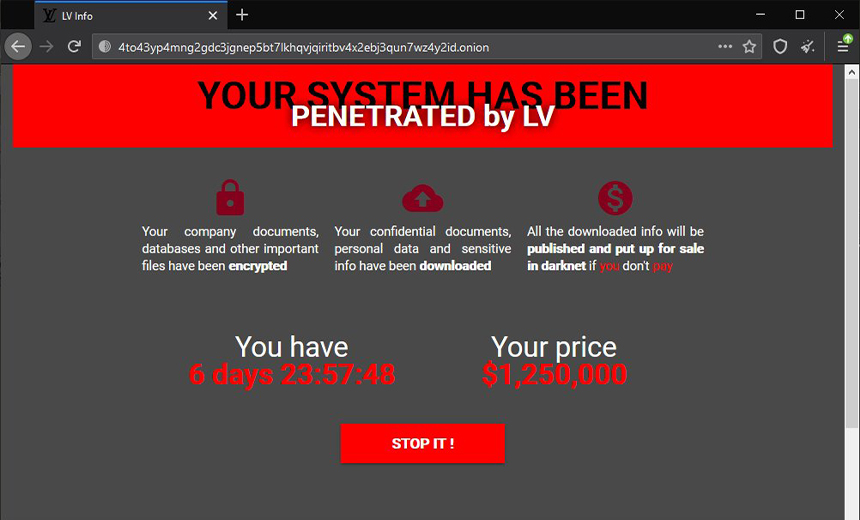
REvil ransomware out
Bleeping Computers reports that the entire infrastructure of the REvil ransomware has gone offline. All Internet sites that have been associated in any way with the notorious hacker group are currently inactive.

Bitdefender reported new activity from TrickBot operators. The attackers updated the infrastructure and even added a new module to their malware. According to experts, the attackers updated their VPO by adding a new version of the vncDll module.

SonicWall ALARM
SonicWall recommended that Secure Mobile Access (SMA) 100 series and Secure Remote Access (SRA) with outdated 8.x firmware be disconnected immediately. Personal emails were even sent out for some customers.
The exploitation targeted a known vulnerability that has been fixed in newer firmware versions. SRA 4600/1600 (EOL 2019), SRA 4200/1200 (EOL 2016) or SSL-VPN200/2000/400 (EOL 2013/2014) were targeted by hackers. For such users company was advised to upgrade to the latest available firmware and change their passwords in a non-alternative format.
At the same time, if the device does not support upgrading to firmware 9.x, further use is impossible and will inevitably lead to a targeted ransomware attack, according to SonicWall.
Research
https://fireshellsecurity.team/ssrf
https://any.run/cybersecurity-blog/introduction-to-malware-analysis
XLS Entanglement: https://www.bc-security.org/post/xls-entanglement
The Story of Jian - How APT31 Stole and Used an Unknown Equation Group 0-Day - Check Point Research: https://research.checkpoint.com/2021/the-story-of-jian
Velociraptor vs. PrintNightmare
What you need to know about Process Ghosting, a new executable image tampering attack: https://www.elastic.co/blog/process-ghosting-a-new-executable-image-tampering-attack
What I have learned from doing a year of Cloud Forensics in Azure AD: https://m365internals.com/2021/07/13/what-ive-learned-from-doing-a-year-of-cloud-forensics-in-azure-ad
Reverse Engineering AsyncRat Payload: https://blog.telspace.co.za/2021/07/reverse-engineering-asyncrat-payload.html?m=1
.telspace.co.za/2021/07/reverse-engineering-asyncrat-payload.html?m=1)https://blog.telspace.co.za/2021/07/reverse-engineering-asyncrat-payload.html?m=1
