Only critical vulnerabilities of the week and the newest attacks

Too many updates from the same vendors come out every month. Either the developers make more mistakes in the development process, or security researchers have begun to actively improve their own competencies. For example, Apple releases updates almost every week. As follows from the news section, attackers regularly use such vulnerabilities in their attacks. Why not?
Read our documentation, subscribe to news and use Vulners! Stay on the latest!
- Vulnerabilities: Apple tons of staff in one patch, VMware, Siemens and Nginx critical vulnerabilities;
- Tools: OpenTelemetry pack for monitoring, SUD_KILLER audit tool and couple of offensive;
- News: only attacks and ransomware in famous organizations;
- Research: attack articles, YouTube videos and detection materials.
Vulnerabilities

Apple this week released a security update fixing three zero-day vulnerabilities that attackers have exploited in real-world attacks. Exploitation of CVE-2021-30713 allows an attacker to bypass standard TSS privacy protections and thereby gain full access to disk, screen recording, and other system functions without asking for explicit consent from the user. Two other vulnerabilities CVE-2021-30663 and CVE-2021-30665 affect the WebKit browser engine on Apple TV 4K and Apple TV HD devices and can lead to remote code execution on attacked devices.
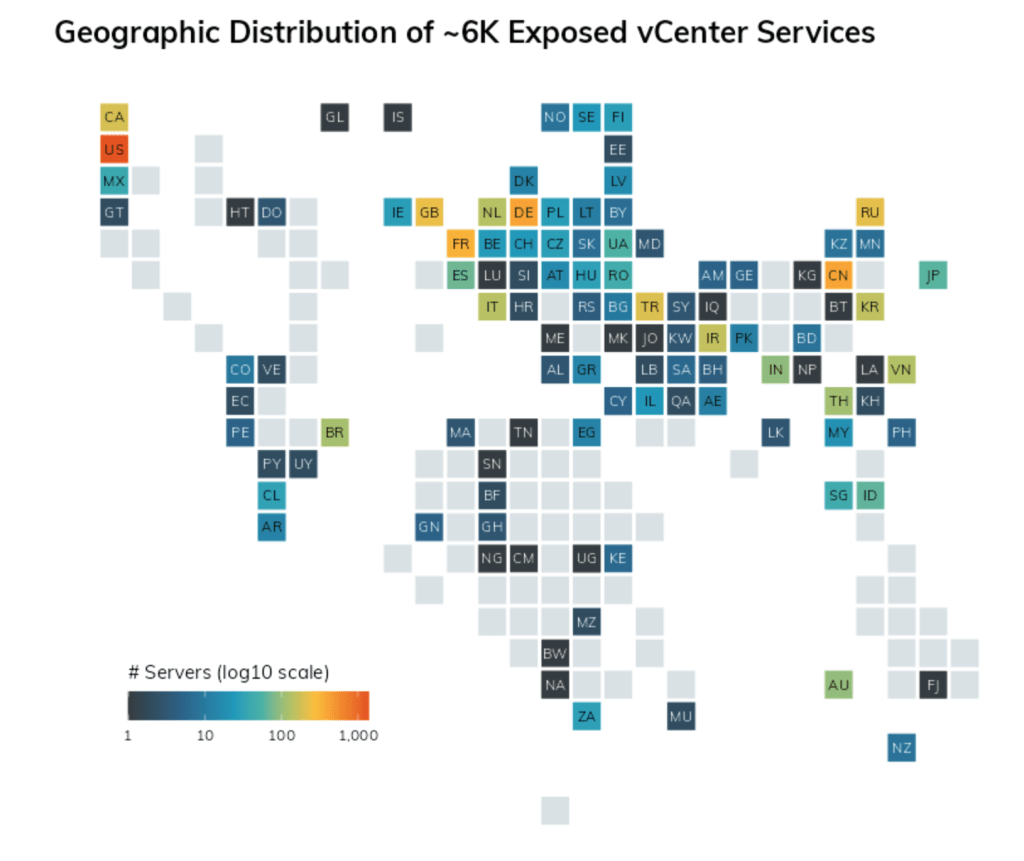
What you need to know about the latest critical vCenter Server vulnerability
VMware has identified and resolved the Remote Code Execution (RCE) vulnerability CVE-2021-21985 in the vSphere HTML5 client. The vulnerability is due to a lack of input validation in the VSAN Health Check plug-in, which is enabled by default in vCenter Server. To exploit CVE-2021-21985, an attacker needs access to port 443. In addition to RCE, VMware has fixed the CVE-2021-21986 vulnerability, which is related to the authentication mechanism in the vCenter Server plug-ins. Based on the severity of the issues found, VMware encourages vCenter users to immediately update vCenter Server versions 6.5, 6.7 and 7.0.

Critical vulnerability in Siemens SIMATIC S7-1200 and S7-1500 logic controllers
Claroty discovered a dangerous vulnerability in Siemens SIMATIC S7-1200 and S7-1500 programmable logic controllers, the exploitation of which allows you to bypass the isolated software environment of the CPU to execute arbitrary code in protected memory areas. An attacker could also exploit vulnerability CVE-2020-15782 for remote read / write memory access.
Siemens has released updates for various products, including S7-1500 and S7-1200, that address the vulnerability. Users are strongly encouraged to update to the latest versions.

Vulnerability in Nginx resolver allows attacker to gain full control over attacked system
Nginx released a hotfix for a critical vulnerability in its DNS resolution implementation. CVE-2021-23017 vulnerability in the Nginx resolver allows an attacker to gain full control over the attacked system, and a publicly available exploit already exists for it.
The vulnerability could be caused by a DNS response to a DNS query from nginx when configuring a resolver primitive. A specially configured package allows you to overwrite the least significant metadata byte of the next heap block with 0x2E and execute the code.
Tools
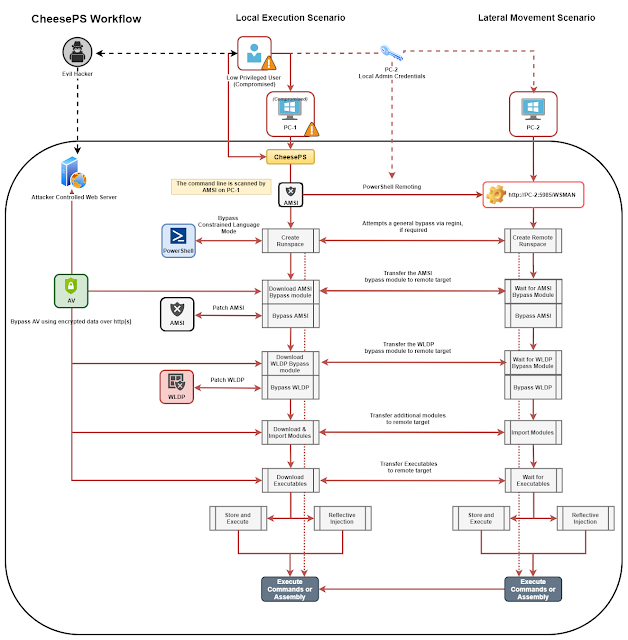
CheeseTools: Self-developed tools for Lateral Movement/Code Execution.

OpenTelemetry: OpenTelemetry is a collection of tools, APIs, and SDKs. You can use it to instrument, generate, collect, and export telemetry data (metrics, logs, and traces) for analysis in order to understand your software's performance and behavior.

SUDO_KILLER is a tool to identify and exploit sudo rules misconfigurations and vulnerabilities within sudo for linux privilege escalation
News
Several Japanese government organizations have been hacked through the Fujitsu ProjectWEB information exchange tool. According to media reports, having obtained unauthorized access to information systems, the attackers seized at least 76,000 email addresses of employees and contractors. So far, the incident has affected the Ministry of Foreign Affairs of Japan, the Ministry of Land, Infrastructure, Transport and Tourism of Japan and Narita International Airport. Fujitsu has suspended ProjectWEB until the scope and cause of the incident is fully established.

Sound hardware maker Bose reported this week that it had been a victim of ransomware earlier this year. On March 7, a cyberattack was carried out on the company's systems located in the United States, and was discovered on the same day, but the attackers still managed to encrypt the internal network. An internal investigation showed that cybercriminals managed to gain access to documents from the personnel department. The attackers were able to see the names of Bose employees, social security numbers, and data related to compensation payments.
The FBI has reported a foreign hacker attack on the local municipal government in the United States. The investigation showed that the hack was carried out through vulnerabilities in Fortinet's network equipment. The incident was discovered in May 2021, about a month after the FBI alerted the private and public sector to patching vulnerabilities in Fortinet hardware. However, despite the authorities' warning, at least one government organization did fall prey to hackers. The FBI hopes that the real-life example they have posted will encourage others to get a fix as soon as possible.
Research
Abusing LNK "Features" for Initial Access and Persistence: https://v3ded.github.io/redteam/abusing-lnk-features-for-initial-access-and-persistence
Understanding & Detecting C2 Frameworks: https://nasbench.medium.com/understanding-detecting-c2-frameworks-ares-8c96aa47e50d
An Introduction to Memory Analysis With Volatility. A multi-part series.
- Memory Analysis For Beginners: Part 1
- Memory Analysis For Beginners: Part 2
- Memory Analysis For Beginners: Part 3
https://www.youtube.com/watch?v=wfX\_bppAbbU
Feedback -> here
.medium.com/TUwRi8qLvgb)
https://www.youtube.com/watch?v=wfX\_bppAbbU
Feedback -> here
