Too many vulnerabilities on one Tuesday from 2 vendors, not to mention zero-days

Almost every week there is a new vulnerability pack with a new name, this time it's Frag Attacks (wi-fi). Another Microsoft patch has been released - there will be exploits soon. Also, a huge number of Adobe design and office products have been patched. Attackers through ransomware are becoming more and more vicious, for example, attackers begin to threaten the police and large enterprises that influence the fuel market.
- Vulnerabilities: Wi-Fi for everyone, tons of vulnerabilities from Adobe and Microsoft, + rare vulnerability in VMware product;
- Tools: mostly offensive;
- News: Colonial Pipeline hack, Babuk vs Police, Rapid7 code leaks;
- Research: Reports and research articles + OSCP cheat sheets.
Vulnerabilities

Researcher Maty Vanhof presented a report that all Wi-Fi devices released after 1997 are vulnerable to Frag Attacks. All security protocols of the standard are affected, including the latest WPA3. The researcher promises to provide full information in the corresponding report at the USENIX Security '21 conference in August this year.
These vulnerabilities allow an attacker in Wi-Fi range to collect information about the device's owner and execute malicious code.

VMware Realize Business for Cloud CVE-2021-21984
VMware Realize Business for Cloud is used to visualize and plan costs, as well as analyze costs and compare business metrics. The discovered vulnerability allows an unauthenticated attacker to remotely execute commands on the target device. As a result, the attacker will be able to gain complete control over the target's server.
CVE-2021-21984 is critical, so all affected organizations are encouraged to install pre-existing patches as soon as possible.

CVE-2021-28550 affects eight software versions, including those running on Windows and MacOS systems: Windows Acrobat DC and Reader DC (versions 2021.001.20150 and later), MacOS Acrobat DC and Reader DC (versions 2021.001.20149 and older), Windows and MacOS Acrobat 2020 and Acrobat Reader 2020 (versions 2020.001.30020 and later), Windows and MacOS Acrobat 2017 and Acrobat Reader 2017 (versions 2017.011.30194 and later).
Adobe did not provide technical details for the zero-day vulnerability. The developers have released a patch that fixes this problem, as well as 43 other vulnerabilities in 12 products, including Adobe Creative Cloud, Illustrator, InDesign and Magento applications.

Fixed 55 vulnerabilities, 4 of which are critical. Three fixed vulnerabilities - 0-day.
- CVE-2021-31207: in Exchange, which was discovered in April as part of the Pwn2Own competitions. Although the vulnerability criticality score is relatively low (6.6 on CVSS), the exploit has not yet been published;
- CVE-2021-31200: RCE;
- CVE-2021-31204: privilege escalation of .NET and Visual Studio;
- CVE-2021-31166: vulnerability in Microsoft IIS HTTP stack and can lead to memory corruption and, as a result, remote code execution in the OS kernel.
Also closed two critical vulnerabilities leading to remote code execution.
Tools
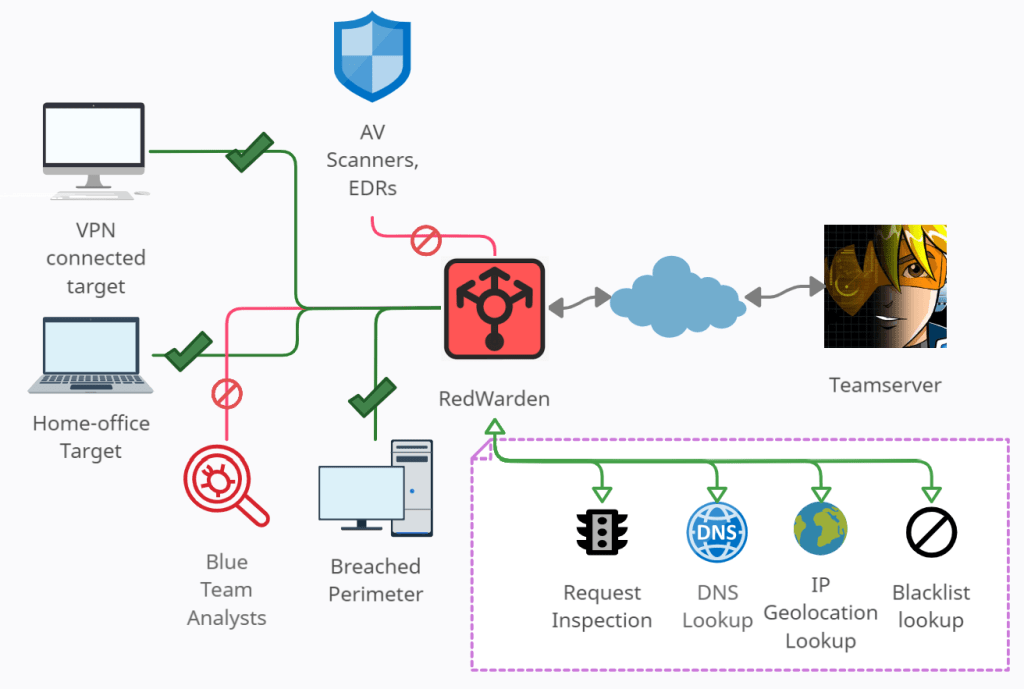
RedWarden - Flexible CobaltStrike Malleable Redirector - created to solve the problem of IR/AV/EDRs/Sandboxes evasion on the C2 redirector layer. It's intended to supersede classical Apache2 + mod_rewrite setups used for that purpose.
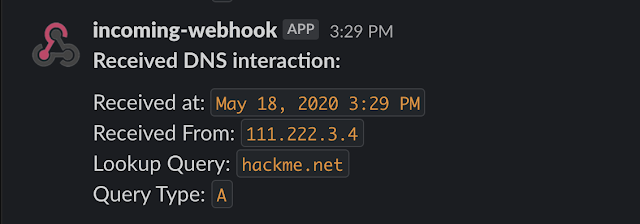
DNSObserver - A handy DNS service written in Go to Aid in the detection of several types of blind vulnerabilities.

Red-Kube: Red Team K8S adversary emulation based on kubectl.
News

Colonial Pipeline, the largest fuel company in the USA, was attacked by the Ransomware. The attack was implemented by the cybercriminal group DarkSide. The cybercriminals compromised the company's network and blocked about 100 GB of data on the servers. For these data, the group demanded a ransom, and in case of non-payment, threatens to put them in the public domain. To limit the spread of the ransomware, Colonial Pipeline was forced to shut down its computer network, resulting in the company's fuel pipeline shutting down. According to Bloomberg, the fuel company paid out about $ 5 million to the cybercriminals.

Babuk Locker threats the police
In April of this year, Babuk Locker ransomware operators hacked into the internal network of the DC Police Department. The hackers said that police officials allegedly entered into negotiations with them. However, the parties failed to agree.
Now the attackers published the data of twenty law enforcement officers on their website. According to unconfirmed reports, cybercriminals are going to lay out in the public domain full information about all employees of the police department.

Rapid7 reports that attackers gained access to the company's source code after a recent breach of Codecov, an online software testing platform.
In January of this year, unknown attackers managed to compromise Codecov and added a credential collector to one of the tools. The compromise affected the Bash Uploader product, which allows Codecov customers to submit code coverage reports for analysis
Research
Leveraging Microsoft Teams to persist and cover up Cobalt Strike traffic: https://www.blackarrow.net/leveraging-microsoft-teams-to-persist-and-cover-up-cobalt-strike-traffic
Detecting Lateral Movement via Service Configuration Manager: https://snorlax-security.hilo21.com/detection-engineering-and-threat-hunting/lateral-movement/detecting-lateral-movement-via-service-configuration-manager
From pentest to APT attack: cybercriminal group FIN7 disguises its malware as an ethical its malware as an ethical hacker’s toolkit: https://bi-zone.medium.com/from-pentest-to-apt-attack-cybercriminal-group-fin7-disguises-its-malware-as-an-ethical-hackers-c23c9a75e319
https://www.youtube.com/watch?v=\_E0PWQvW-14
All about OSCP
Offensive Security Certified Professional is an ethical hacking certification offered by Offensive Security that teaches penetration testing methodologies and the use of the tools included with the Kali Linux distribution.
OSCP Buffer overflow concepts and tutorials
http://strongcourage.github.io/2020/04/19/bof.html
OSCP Cheat sheets:
https://github.com/slyth11907/Cheatsheets
Pentest-Cheat-Sheets
This repo has a collection of snippets of codes and commands to help our lives! The main purpose is not be a crutch, this is a way to do not waste our precious time! This repo also helps who trying to get OSCP. You'll find many ways to do something without Metasploit Framework.
Link: https://github.com/Kitsun3Sec/Pentest-Cheat-Sheets
Hacking/OSCP cheat sheets
https://ceso.github.io/posts/2020/04/hacking/oscp-cheatsheet/
All about OSCP:
https://oscp.infosecsanyam.in
OSCP preparation
https://github.com/rewardone/OSCPRepo
https://github.com/0x4D31/awesome-oscp#resources
https://ired.team/offensive-security-experiments
OSCP methodology:-
https://paper.dropbox.com/doc/OSCP-Methodology-EnVX7VSiNGZ2K2QxCZD7Q
https://github.com/OlivierLaflamme/Cheatsheet-God
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation
https://github.com/foobarto/redteam-notebook/blob/master/README.md
https://github.com/RustyShackleford221/OSCP-Prep
https://johnjhacking.com/blog/the-oscp-preperation-guide-2020
Feedback
rep](https://github.com/RustyShackleford221/OSCP-Prep)
https://johnjhacking.com/blog/the-oscp-preperation-guide-2020
