New vulnerable pack, undetectable malware and MITRE 3 round tests

Another urgent update has appeared for apple products. However, 21 vulnerabilities in Exim mail servers were recognized as the leader of the past week. Recently, our news section consists of the most interesting malware, but how else? Also, don't forget to check the research section, there are some materials on the latest MITER test.
- Vulnerabilities: Apple emergency patch, tons of bug in Exim servers, Dell vulnerable for a long time and new Spectre methods;
- Tools: Jenkins attack framework, Android RAT and etc;
- News: CISA alert, exfiltration via ICMP and undetectable malware for Windows;
- Research: MITRE 3 round, phishing with Outlook and Teams, IR playbooks and other useful staff.
Vulnerabilities

New methods of exploiting the old Spectre vulnerability have been discovered. Using them, attackers can conduct effective attacks on Intel and AMD processor systems. This new type of attack uses a microoperations cache to break down machine instructions into simple instructions, thereby speeding up the computation process.

Dell driver vulnerability
The vulnerability found has been assigned the identification number CVE-2021-21551. It allows a problem in the DBUtil driver to elevate privileges to the system level. SentinelOne researchers estimate that over 100 million Dell devices released since 2009 are affected by this vulnerability.
Apple releases emergency software security updates for iOS, macOS, and watchOS to patch 3 new 0-day vulnerabilities that are under active attack and extend patches for a fourth vulnerability.

21Nails
Exim is the open source mail server that is currently the most widely used on the Internet. The set of vulnerabilities is called 21Nails, 10 of the vulnerabilities included in it can be exploited remotely. As a result, using these bugs, an attacker can completely take control of the Exim server and among other things, gain access to the mail traffic passing through it.
Vulnerabilities from the 21Nails pack affect absolutely all versions of Exim released in the last 17 years, up to 4.94.2 in which they were fixed.
Tools
Jenkins Attack Framework is an Accenture, internally developed, red team-oriented tool for interacting with Jenkins build servers. Jenkins is an opensource build CI/CD pipeline tool that is commonly used in industry to manage building and testing code.
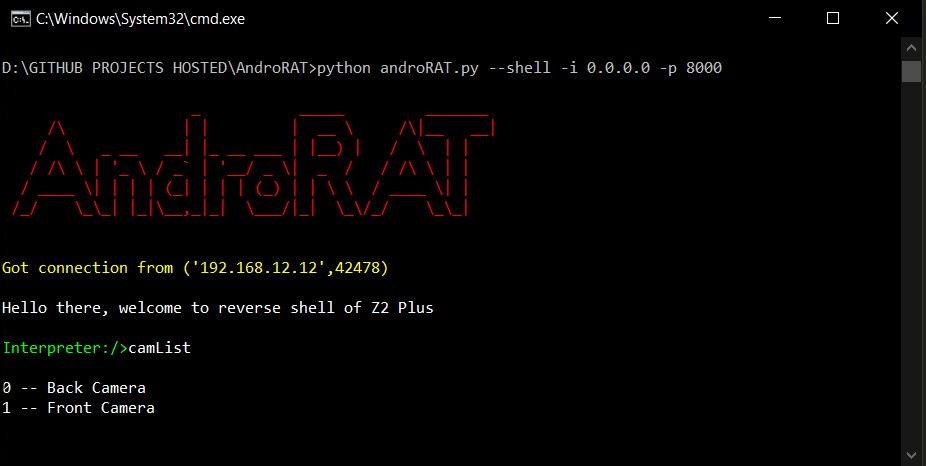
A Simple Android Remote Administration Tool Using Sockets. It uses java on the client side and python on the server side. https://github.com/karma9874/AndroRAT

Kiterunner - Contextual Content Discovery Tool.

KubeArmor - Container-aware Runtime Security Enforcement System.
News

СISA released reports on a new ransomware called FiveHands.
The reports describe the techniques, tactics, and procedures that attackers use during an attack using FiveHands. In addition, CISA experts spoke about indicators of compromise and potential measures to protect, detect and respond to such attacks.
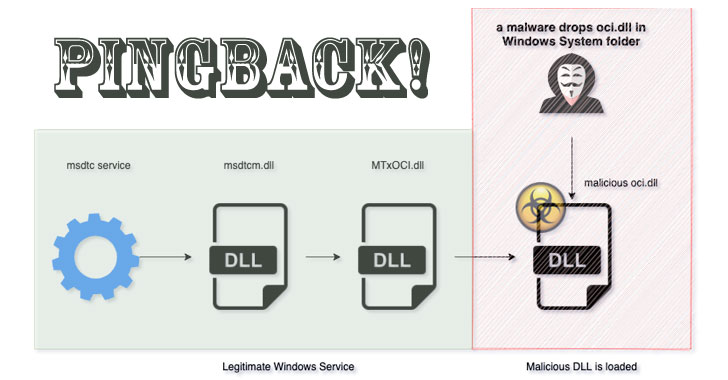
Pingback Malware hides connections to C&C via IMCP
The Pingback malware disguises itself as oci.dll, which is loaded by Microsoft's Distributed Transaction Management service. However, DLL hijacking is by no means a new technique - it has been used by hackers for years and is not a feature of this project. The peculiarity of Pingback Malware is that it uses the protocol (IMCP) to communicate with the command and control server.

Moriya is designed for Windows and has been around since at least 2018, until recently the rootkit went unnoticed. According to the company, during this time it was used for very limited and narrowly targeted attacks (so far less than a dozen have been affected).
Moriya has gone unnoticed for so many years as it uses a well-known tactic, for example, injecting itself between the Windows TCP / IP stack and incoming network traffic, and then intercepting data packets before they even reach the operating system and any locally installed antivirus.
To infiltrate a targeted organization's network and install Moriya, attackers usually compromised vulnerable IIS web servers. For example, in one of the confirmed attacks, the entry point was a server that did not have a patch for the old CVE-2017-7269 vulnerability. Exploiting this bug, the attackers installed a web shell on the server and then used it to deploy Moriya.
Research
Domain Fronting With Firebase: Hide you traffic as Mobile App traffic:
https://www.redteam.cafe/red-team/domain-front/firebase-domain-front-hiding-c2-as-app-traffic
Phishing with fake meeting invite: https://www.exandroid.dev/2021/04/24/phishing-with-fake-meeting-invite
Incident response playbooks: https://docs.microsoft.com/en-us/security/compass/incident-response-playbooks
MITRE 3 round results:
Bypassing EDR real-time injection detection logic: https://blog.redbluepurple.io/offensive-research/bypassing-injection-detection
https://vulners.com/mmpc/MMPC:8CC46BE74AAF7D44E67B0C67075B6661
A Malware Configuration Extraction Tool: https://mwcfg.info
Detecting Lateral Movement via Service Configuration Manager: https://snorlax-security.hilo21.com/detection-engineering-and-threat-hunting/lateral-movement/detecting-lateral-movement-via-service-configuration-manager
Feedback
-service-configuration-manager](https://snorlax-security.hilo21.com/detection-engineering-and-threat-hunting/lateral-movement/detecting-lateral-movement-via-service-configuration-manager)
