Ransomware for your Exchange and mobile vulnerabilities 👾

The topics of email vulnerabilities continue, with more and more sophisticated vulnerabilities being exploited in attacks. Notably, new botnets/malware are automating the exploitation of the newest vulnerabilities by transforming them into worm-like weapon. Ransomware is again breaking the record for the amount of money demanded ("We need more gold!")!
- Vulnerabilities: rare Android vulnerability in the wild, Apache again, 1 week = 1 iOS version, too a lot of Cisco vulnerabilities;
- Tools: forensic tools, attacking and recon staff;
- News: only updated malware with ransomware for Exchange and Acer;
- Research: Automation is a power, schemes, hack reports and videos.
Find short feedback -> here
Vulnerabilities

0-day vulnerability affecting Android devices
Google researchers discovered attacks on the CVE-2020-11261 vulnerability patched in January 2021, which appears on Android devices using Qualcomm chipsets. Usually such attacks require very complex scenarios and are not used en masse, but at least one attacker has already managed to exploit CVE-2020-11261, as reported by Google's Project Zero team.
Apache Software Foundation (ASF) has fixed a critical vulnerability in Apache OFBiz, an ERP system designed for enterprise resource planning. The vulnerability is so severe that it allows an unauthenticated remote attacker to gain control over OFBiz.
Researchers are tracking the vulnerability under the CVE-2021-26295 identifier, it affects all versions of the software before 17.12.06. The bug is about "unsafe deserialization", using this attack vector an intruder can remotely execute code on the target server.

Specified vulnerability was fixed in the iOS 14.4.2, iOS 12.5.2, and watchOS 7.3.3 releases. Apple released security updates for iPhone, iPad, iPod and Apple Watch devices that address a vulnerability actively exploited by hackers.
The vulnerability, identified as CVE-2021-1879, was discovered by the Google Threat Analysis Group. The problem affects the Webkit browser engine and allows for XSS attacks.

Critical vulnerability in Cisco Jabber allows you to remotely compromise systems
Exploitation of vulnerabilities allows an attacker to run arbitrary programs on the underlying operating system with elevated privileges, etc.
Cisco released software updates that address multiple vulnerabilities in Jabber messaging clients for Windows, macOS, Android, and iOS operating systems.
Exploitation of vulnerabilities allows an attacker to run arbitrary programs on a base operating system with elevated privileges, gain access to confidential information, intercept control over protected network traffic, and more.
Tools
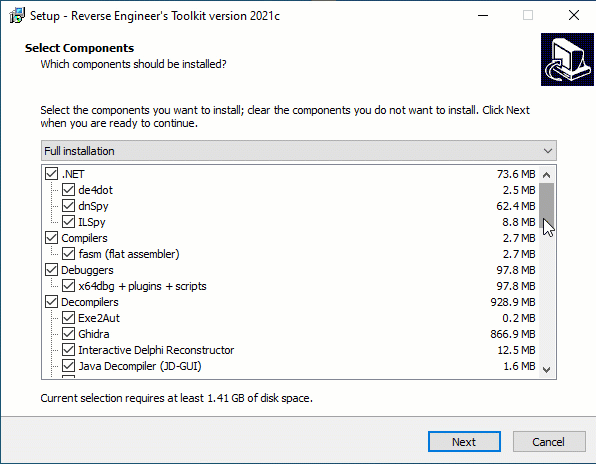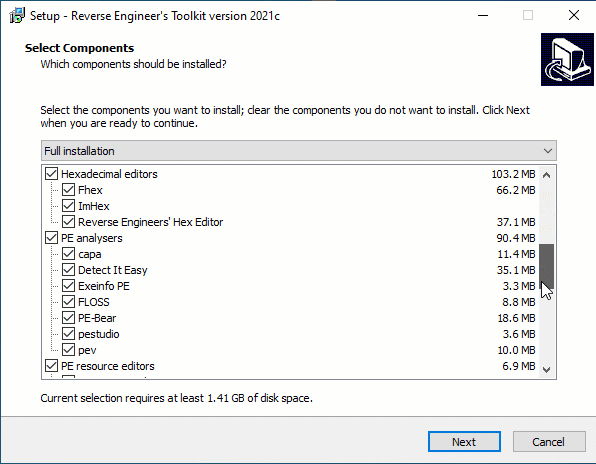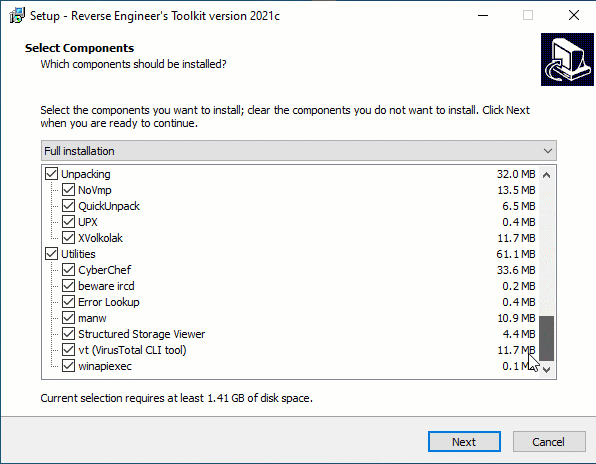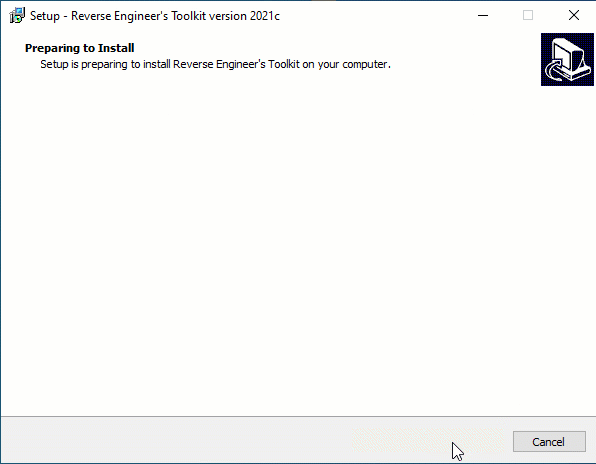
Retoolkit is a collection of tools you may like if you are interested on reverse engineering and/or malware analysis on x86 and x64 Windows systems. After installing this toolkit you’ll have a folder in your desktop with shortcuts to RE tools like these.

Kraker is a distributed password brute-force system that allows you to run and manage the hashcat on different servers and workstations, focused on easy of use. There were two main goals during the design and development: to create the most simple tool for distributed hash cracking and make it fault-toleran.
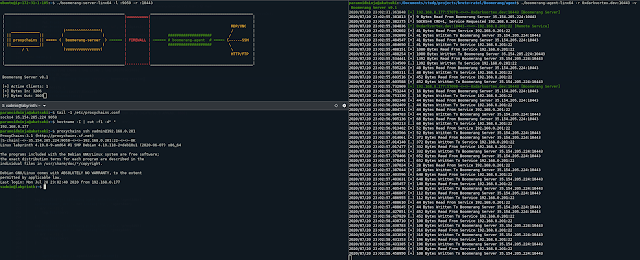
Boomerang is a tool to expose multiple internal servers to web/cloud using HTTP+TCP Tunneling. The Server will expose 2 ports on the Cloud. One will be where tools like proxychains can connect over socks, another will be for the agent to connect. The agent can be executed on any internal host.

Find exposed AWS cloud assets that you did not know you had.
News
Malware received a worm-like module that allows attacks to scan and infect Windows systems available on the Web.
The Purple Fox malware, which previously spread via exploit kits and phishing emails, has now received a worm-like module. The new feature allows the malware to scan and attack Windows systems available on the Web during attacks.
The Purple Fox malware was first detected in 2018 after infecting more than 30,000 devices.

InfoSec experts from Prodraft published a report detailing the investigation into the activities of a new APT group, which they named SilverFish. Prodraft experts say they managed to gain access to attackers' servers and malicious samples that link SilverFish to the attack on SolarWinds. At the same time, some of these servers are also used by the EvilCorp group, which distributes the Dridex and WastedLocker malware.
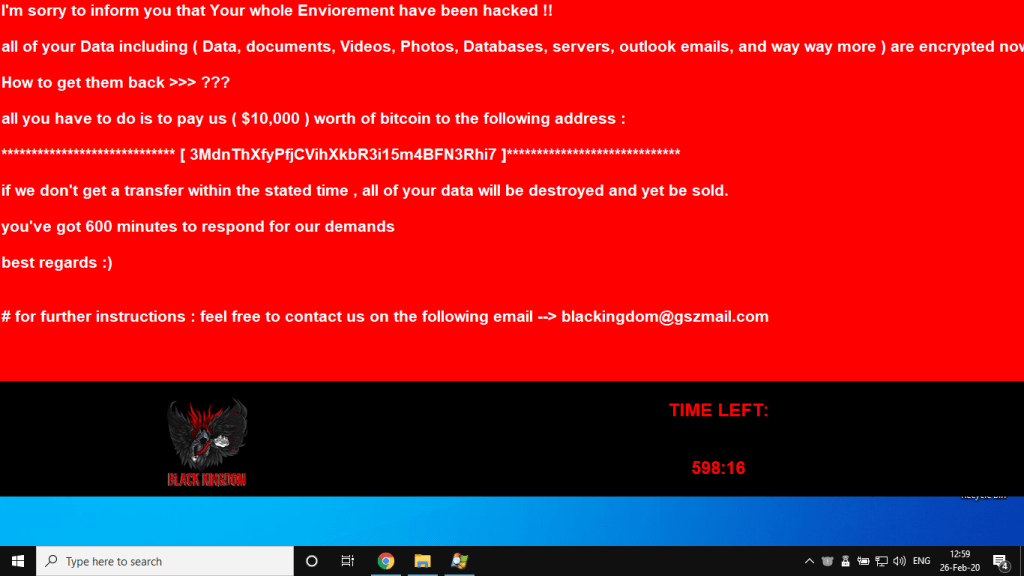
Microsoft Exchange attacks Black Kingdom ransomware
Researchers discovered that vulnerable Microsoft Exchange servers are now being attacked by another encryption attacker. Meanwhile, Microsoft reports that about 92% of servers vulnerable to ProxyLogon problems have already received patches.
Previously vulnerable Microsoft Exchange servers were attacked by the DearCry ransomware.
Microsoft experts report that the fight against ProxyLogon is in full swing. Microsoft said last weekend that roughly 92% of all Exchange servers have received patches and are now protected from malicious attacks. So, according to the OS manufacturer, out of 400,000 Exchange servers deployed worldwide, only 30,000 are still vulnerable to attacks.

The journalists said that information about the auction of documents stolen from Acer was published on one of the hacker forums. Among the stolen documents are financial statements and banking communications. Employees of the French edition LegMagIT managed to find out that the operators of the ransomware REvil were behind the attack on Acer. At the moment, the criminals are demanding a record $ 50 million from the affected company. At the same time, according to ransom-note, this price will double on March 28.
It is the largest public ransom in history, and leaked images of allegedly stolen files have also been posted on their website.
Research
Nessus2Word: Generate .docx report from .nessus files!
Writing reports can be tedious, so let's automate the process.
Includes ability to replace vulnerability summaries with custom text as well as displaying CSSv3 vectors.
Work smarter not harder: https://github.com/jeffjbowie/Nessus2Word
Scaling Forensics Across Many Systems
Become a Microsoft Defender for Endpoint Ninja: https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/become-a-microsoft-defender-for-endpoint-ninja/ba-p/1515647
Threat Hunting with Data Science: Registry Run Keys: https://mergene.medium.com/threat-hunting-with-data-science-registry-run-keys-9ae329d1ad85
reat Hunting with Data Science: Registry Run Keys: https://mergene.medium.com/threat-hunting-with-data-science-registry-run-keys-9ae329d1ad85
