Apple weekly digest with mobile apps

This week, the first computer malware was discovered on the Apple M1, whose creators are quick to adapt. Mobile app developers take their time to update them for their products and zero-day often takes too long to fix. We collected all the main most interesting news of the week with Apple and quite a bit not about them.
- Vulnerabilities: Apple, Telegram, zero-day for popular App;
- Tools: top reverse tool, couple for RECON and new C2 framework;
- News: Apple again and source code leak for Microsoft products;
- Research: Vulnerability reports and useful stuff for DFIR guys.
Really short feedback -> here
Vulnerabilities

Apple app with zero-day
The popular Android app SHAREit, which has been downloaded over a billion times, contains an unpatched vulnerability that threatens the security of mobile device owners. The vulnerabilities identified in the application allow remote execution of malicious code on mobile devices. For three months the developers have not been able to prepare a correct update that fixes the bug.
The vulnerabilities identified in the application allow remote execution of malicious code on mobile devices.

Shielder specialists discovered a vulnerability in the versions of the application for iOS, Android and macOS. The core of the security problem lay in the way animated stickers were handled in secret chats. Attackers can send modified stickers to unsuspecting users and access messages, photos and videos in regular and secret chats. An update has been released to date that fixes this vulnerability.

Malvertisers
Over the past three months the number of malvertisements from ScamClub has reached 16 million a day.
Researchers initially discovered the vulnerability on June 22, 2020, and notified Apple and Google on June 23, since Chrome for iOS also uses the WebKit engine and is vulnerable to the exploit. It wasn't until Feb. 1 that Apple assigned the bug a CVE and fixed it in another update, while Chrome fixed the vulnerability in early December.
ScamClub exploited CVE-2021-1801 in the WebKit engine used in various web browsers, to redirect victims to fraudulent sites. Over the past three months, the number of malicious ad impressions has reached 16 million per day. ScamClub is known for distributing a huge number of malicious ads. Even if most of the ads are blocked, their volume is so large that undetected ads result in a significant number of malvertisements.
Tools

Researchers often have to deal with application reverse engineering, especially for iOS or native Android libraries. Ghidra is an Open Source project, open source, quite convenient and accessible for all platforms.
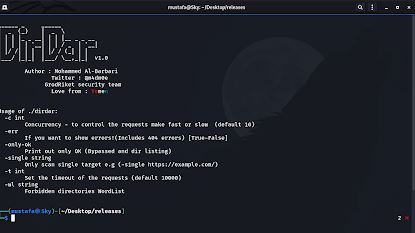
DirDar a tool that searches for (403-forbidden) directories to break it and get dir listing on it.
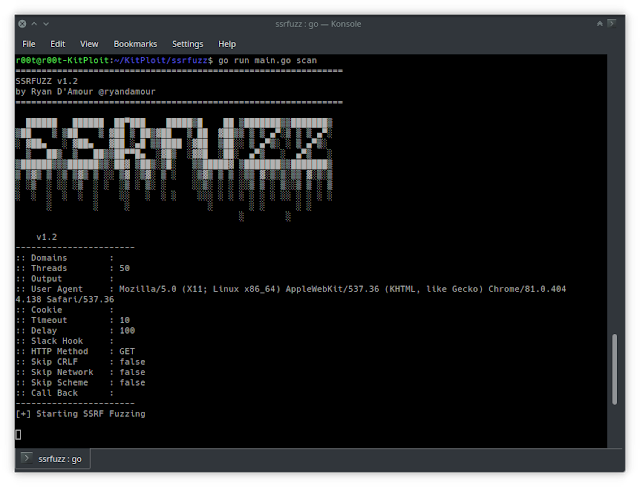
SSRFuzz is a tool to find Server Side Request Forgery vulnerabilities, with CRLF chaining capabilities.

BlackMamba is a multi client C2/post exploitation framework with some spyware features. Powered by Python 3.8.6 and QT Framework.
News
The next iOS 14.5 will include a feature that redirects all Safari Safe Browsing traffic through proxy servers controlled by Apple. In this way, the company wants to preserve user privacy and prevent Google from knowing their IP addresses. As a result of this feature, all Safe Browsing requests through Apple's own proxy server will appear as coming from the same IP address.

A researcher discovered a modification of the Pirrit malware designed to run on the M1 chip. It is one of the first malware of its kind.
The Apple M1 was introduced in November 2020 and many developers have prepared new versions of their apps to ensure better performance and compatibility. The researcher writes that malware authors are now taking similar steps, adapting their malware for the Apple M1.
The researcher describes in detail the GoSearch22 ad malware disguised as an extension for Safari. It collects data about the sites the user viewed and displays a huge number of ads, including banners and pop-ups that link to suspicious sites that distribute the malware. The tool was originally written to run on Intel x86, but has since been ported to ARM-based M1 chips.

Microsoft announced that it has completed its official investigation into the SolarWinds hacking attack. After all, the attackers did manage to steal the source code, but it was only the source code of several components related to the company's cloud products. Thus, the compromised repositories contained:
- part of the Azure components;
- part of Intune components;
- part of Exchange components.
Microsoft officials summarize that this leak will have no impact on the company's products and that the incident as a whole did not allow hackers to gain broad access to user data.
Research
WebShell report from Microsoft: https://arstechnica.com/information-technology/2021/02/microsoft-is-seeing-a-big-spike-in-web-shell-use
RCE on a Laravel Private Program: https://medium.com/@y.shahinzadeh/rce-on-a-laravel-private-program-2fb16cfb9f5c
One thousand and one ways to copy your shellcode to memory (VBA Macros): https://adepts.of0x.cc/alternatives-copy-shellcode
fw extraction to rce: https://pwner.fun/2021/02/16/firmware-extraction-rce.html
Great article and blog for DFIR and threat hunting guys:
- https://nasbench.medium.com/finding-forensic-goodness-in-obscure-windows-event-logs-60e978ea45a3
- https://nasbench.medium.com/forensics-artifacts-symantec-edr-localdatastore-folder-9bff91d2876d
If you want to know more about .lnk files
Feedback -> here
d2876d](https://nasbench.medium.com/forensics-artifacts-symantec-edr-localdatastore-folder-9bff91d2876d)
If you want to know more about .lnk files
Feedback -> here
