Several critical updates, evil malware and security research

Collected the coolest news about Apple, Cisco, zero-day and some company hacked via vulnerability in their products (lol). There are not so many cool news, but we were able to collect the most interesting ones about Whatsup, another war with the Emotet malware, a new version of NAT slipstreaming. Next month we will tell you about new events in Vulners!
- Vulnerabilities: Already listed some in our preview. + SAP and QNAP;
- Tools: Update tool from FireEye, Recons, andd offensive;
- News: WhatsUp, Emotet, open elastic server with confedential data and new version of NAT slipstreaming ;
- Research: Little by little tweets, interesting attack visualizations for January 2021, research articles, and other useful stuff.
Really short feedback (why not?) -> here
Vulnerabilities

3 zero-day security vulnerabilities—affecting iOS, iPadOS, and tvOS—in the wild.
- CVE-2021-1780 and CVE-2021-1781 are vulnerabilities in the WebKit engine, on the basis of which, for example, the default Safari browser is built. Both of them can lead to the execution of extraneous code on the device, according to Apple representatives.
- CVE-2021-1782 - vulnerability in the system kernel. Apple describes it as a "race condition" error that could potentially be used to elevate the privileges of a process.
Update iOS and iPadOS to 14.4 as soon as possible on all iPads and iPhones that support this version. According to Apple's website, updates are available for iPhones starting from the 6s model, iPad Air starting from the second version, iPad mini starting from the fourth, and also for the seventh generation iPod touch.

Fresh exploit to get root in SAP was published in the public.
Onapsis Research Labs specialists discovered an exploit for SAP products on GitHub, published by Russian researcher Dmitry Chastukhin on January 14, 2021. According to the experts, the exploit applies to SAP SolMan, a platform for managing the lifecycle of all SAP solutions in a distributed environment. The exploit is full-featured and is intended for a vulnerability in SAP SolMan CVE-2020-6207.

Of course sudo ALARM in our previous post!
According to Qualys, the vulnerability allows an unprivileged user to gain root access bypassing the necessary authorization checks and without authentication. Researchers demonstrated working exploits on Debian 10, Fedora 33 and Ubuntu 20.04. Versions sudo 1.8.2 to 1.8.31p2 and 1.9.0 to 1.9.5p1 are vulnerable. CVE-2021-3156 was fixed as part of the 1.9.5p2 update.

Critical vulnerabilities found in Cisco CMX software and routers
Cisco patched 67 critical vulnerabilities in the AnyConnect Secure Mobility Client and RV110W, RV130, RV130W, and RV215W Small Business Routers. The most dangerous vulnerability CVE-2021-1144 in CMX allows you to change the passwords of any user in the system, including a user with administrator rights.
Five vulnerabilities CVE-2021-1146, CVE-2021-1147, CVE-2021-1148, CVE-2021-1149, and CVE-2021-1150 discovered in Cisco Small Business RV110W, RV130, RV130W, and RV215W routers. Their exploitation could allow an authorized remote attacker to enter arbitrary commands with superuser privileges.
More tech info about all vulnerabilities here.

Vulnerable browsers
A patch release of Firefox 84.0.2 was published this month, fixing a critical CVE-2020-16044 vulnerability that could lead to the execution of attacker code when processing a specially crafted COOKIE-ECHO block in the SCTP (Stream Control Transmission Protocol) package. The vulnerability is caused by a reference to an already released memory space (use-after-free) in the COOKIE-ECHO handler. Detailed information about the vulnerability has not been disclosed yet.
Info about all vulnerable browsers

QNAP device
Networking device vendor QNAP released security updates that fix a number of dangerous vulnerabilities in network attached storage (NAS) running QES, QTS and QuTS hero operating systems.
Exploitation of vulnerabilities allows remote attackers to inject malicious code, elevate privileges on a system, execute arbitrary commands on a compromised device or application, or take control of an operating system.
- CVE-2020-2503: QES Cross-Site Scripting Vulnerability - Allows remote attackers to inject malicious code into File Station.
- CVE-2020-2504: QES Out of Directory Vulnerability - Allows attackers to view files in File Station.
- CVE-2020-2505: Vulnerability in QES - Allows attackers to obtain confidential information by generating error messages.
- CVE-2016-6903: QES Command Injection Vulnerability - Allows remote attackers to run arbitrary commands in Ishell.
- CVE-2020-2499: QES Encrypted Passwords Vulnerability - Allows attackers to log into the system using built-in passwords.
- CVE-2020-25847: QTS and QuTS hero Command Injection Vulnerability - Allows attackers to execute arbitrary commands in compromised applications.
As reported by QNAP, the issues have been fixed in QES 2.1.1 (build 20201006) and earlier, QTS 4.5.1.1495 (build 20201123) and earlier, and QuTS hero h4.5.1.1491 (build 20201119) and earlier.

SonicWall was hacked via 0-day vulnerabilities in its own products
SonicWall, a well-known manufacturer of firewalls and VPN products, became a victim of a well-planned attack on internal systems. Cybercriminals reportedly exploited 0-day vulnerabilities in SonicWall's VPN. Among the affected products, according to the vendor itself, were NetExtender VPN (version 10.x) and Secure Mobile Access (SMA), which provides users with remote access to internal resources.
The new SMA 1000 line, SonicWall and SonicWall SonicWave AP firewalls are not affected by the vulnerability.
Tools

Emulation of Kernel Mode Rootkits With Speakeasy. This tool can be used to quickly sort kernel binaries that would otherwise be difficult to parse dynamically.
SysWhispers2
It helps with evasion by generating header/ASM files implants can use to make direct system calls.
APT-Hunter: Threat Hunting Tool via Windows Event Log - Shells.Systems. Get results in csv or

A collection of tools used by Mobile hackers. Happy hacking and happy bug-hunting.

BigBountyRecon tool utilizes 58 different techniques using various Google dorks and open source tools to expedite the process of initial reconnaissance on the target organization. Reconnaissance is the most important step in any penetration testing or a bug hunting process.
News

Emotet
Europol shut down the Emotet botnet infrastructure. As a result of a joint operation by law enforcement agencies of several countries, specialists managed to seize control over the infrastructure and stop the malicious activity of the Emotet botnet. After gaining access to the infrastructure, Europol began distributing a new module on the devices of botnet victims, which will remove the malware starting March 25 this year.
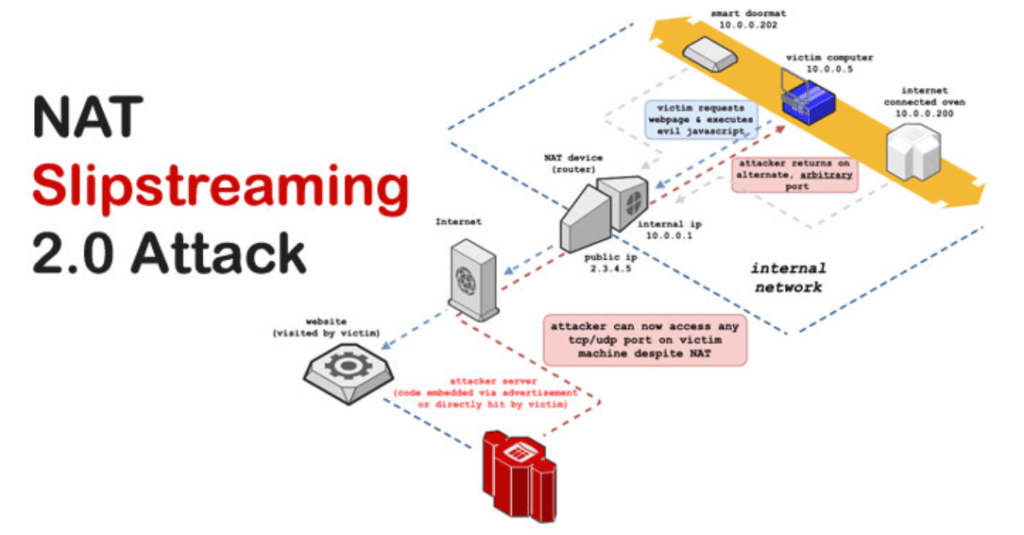
A new way of the NAT slipstreaming attack was published, which allows establishing a network connection from the attacker's server to any UDP or TCP port on the system of a user who opens a web page prepared by the attacker in a browser. The attack allows the attacker to send any data to any port of the user, regardless of the internal address range (192.168.x.x, 10.x.x.x) used on the victim system, with direct network access not available and only through the address translator.
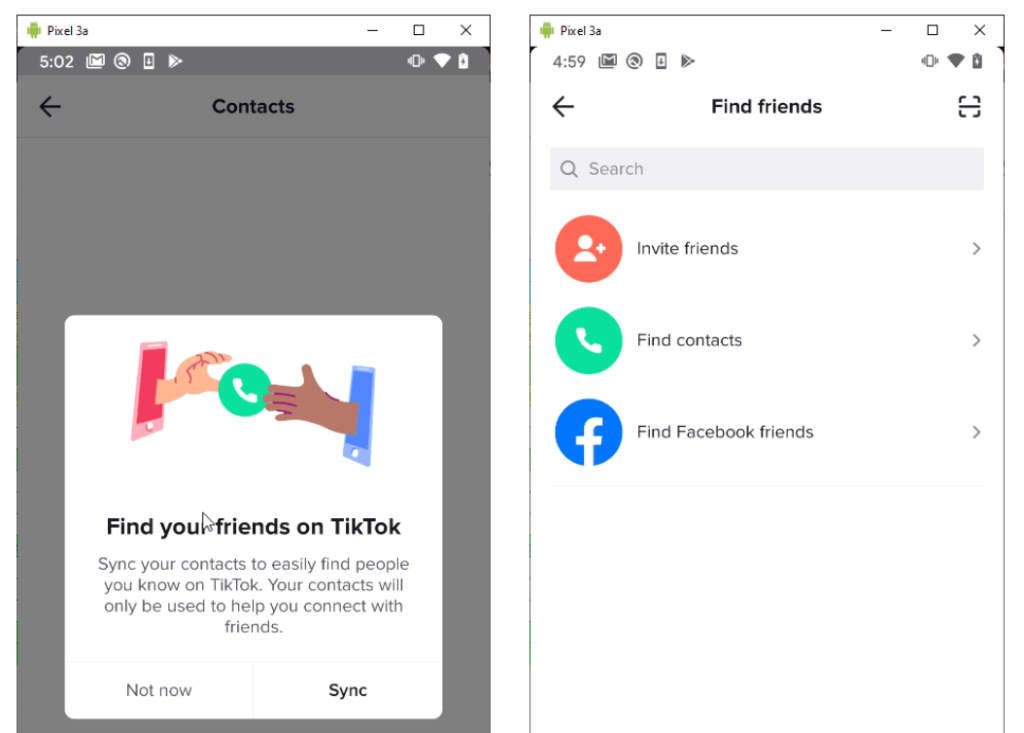
Checkpoint discovered a flaw in TikTok's "Find Friends" feature. If left unchecked, this vulnerability would allow attackers to gain access to personal data in user profiles, including the phone number attached to the account, nickname, unique user ID, profile picture, and certain settings, including the ability to hide the profile and manage subscriptions. Attackers can use this information for criminal purposes.

A security researcher from ESET reported a new malware for Android devices that automatically spreads through WhatsApp messages. The main purpose of the malware is to get users to fall for adware scams or subscriptions. The malware spreads through WhatsApp by automatically sending replies to messages.
According to the researcher, how the initial infection occurs has not been established. However, it should be noted that worm malware can spread incredibly quickly from multiple devices to many others via SMS, email, social media posts, channels/chat groups, etc.

The Safety Detectives team discovered Bykea's open source Elasticsearch server, which contained 400 million customer records.
Bykea is a Pakistani company specializing in delivery, motorcycle taxi services and car sharing.
The 200 GB of data on the open server contained a database of the company's production servers, which contained information about the names, phone numbers, addresses of Bykea's customers and drivers. As well as information about the place of delivery, data about cars with GPS coordinates, unencrypted login-password pairs of company employees, and more.
Research
Potential LFR and RCE on node JS apps
Windows Privilege Escalation Explained: http://www.fuzzysecurity.com/tutorials/16.html
Process Herpaderping – Windows Defender Evasion: https://pentestlaboratories.com/2021/01/18/process-herpaderping-windows-defender-evasion
Cyber Attacks/APT timeline (cool visualization): https://www.hackmageddon.com/2021/01/25/1-15-january-2021-cyber-attacks-timeline
Offensive Windows IPC Internals 1: Named Pipes:
https://csandker.io/2021/01/10/Offensive-Windows-IPC-1-NamedPipes.html
How I hijacked the top-level domain of a sovereign state | Detectify Labs
Really short feedback -> here
PC-1-NamedPipes.html)
How I hijacked the top-level domain of a sovereign state | Detectify Labs
Really short feedback -> here
