Uncommon but enlightening vulnerabilities with Microsoft and more

Not as many critical vulnerabilities as last week. This time it's mostly cool and non-standard vulnerabilities that are important to know about. For example, the KindleDrip attack shows a new way to exploit vulnerabilities. Or another vulnerability is that your kids could be little bug hunters.
- Vulnerabilities: No zero-days, DNSpooq, kids and bughunting;
- Tools: POCs and offensive;
- News: IObit hacked, RDP DDOS and miners/ransomware;
- Research: Mostly useful for Purple guys.
Really short feedback -> here
Vulnerabilities

Researchers identified seven vulnerabilities in Dnsmasq software, collectively called DNSpooq. Three of them allow to spoof the contents of DNS server cache, and four allow remote execution of malicious code. Users are recommended to update to build 2.83.
DNSMasq package allows you to raise and quickly configure a DNS forwarder with caching feature, as well as DHCP or TFTP server in the local network. This software is intended for use in home networks and small businesses that use Network Address Translation (NAT).

Yogev Bar-On discussed the new KindleDrip attack technique and the three bugs that have already been fixed. The expert received $18,000 from the bug bounty program for these vulnerabilities.
The first vulnerability in the KindleDrip exploit chain involves the "Send to Kindle" feature, which allows users to send MOBI e-books to their device via email. By abusing this feature, it was possible to send a specially prepared ebook to the device, which allows the execution of arbitrary code on the target Kindle.
The code execution was made possible by a second vulnerability related to the library that Kindle devices use to parse JPEG XR images. Exploiting the bug only required the user to simply click on a link inside the book containing the malicious JPEG XR image.
A third problem that allowed the user to elevate privileges and execute code with root rights, gaining full control over the target device.
Problems with code execution and privilege escalation are fixed in December 2020 with the 5.13.4 release.

More details have emerged about a security feature bypass vulnerability in Windows NT LAN Manager (NTLM) that was addressed by Microsoft as part of its monthly Patch Tuesday updates earlier this month. CVE-2021-1678 (CVSS score 4.3), was described as a “remotely exploitable” flaw found in a vulnerable component bound to the network stack, although exact details of the flaw remained unknown. This vulnerability allows an attacker to relay NTLM authentication sessions to an attacked machine, and use a printer spooler MSRPC interface to remotely execute code on the attacked machine.
Successful exploits could also allow an adversary to remotely run code on a Windows machine or move laterally on the network to critical systems such as servers hosting domain controllers by reusing the NTLM credentials directed at the compromised server.
In addition to installing the January 12 Windows update, the company has urged organizations to turn on Enforcement mode on the print server, a setting which it says will be enabled on all Windows devices by default starting June 8, 2021.

According to a bug report on GitHub, two children pressed random keys on both the physical and on-screen keyboards of a locked device. This caused the Linux Mint splash screen to fail, which eventually gave them access to the desktop without a password. The user noted that this was not an isolated incident: children managed to bypass the lock screen a second time as well.
Fortunately, Linux Mint developers fixed the vulnerability last week.
https://vulners.com/hackread/HACKREAD:A6EB028653B33477E63F8FD8A3A77E14
Tools

ATMMalScan
It is a cmd tool for Windows operating systems version 7 and higher, which helps to search for malware traces on an ATM during the DFIR process. This tool examines the running processes of a system, as well as the hard disk, depending on the specified file path.
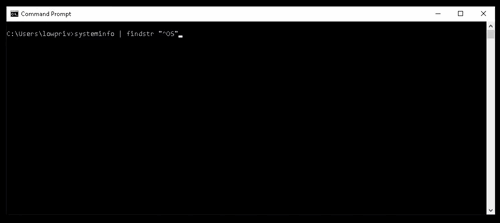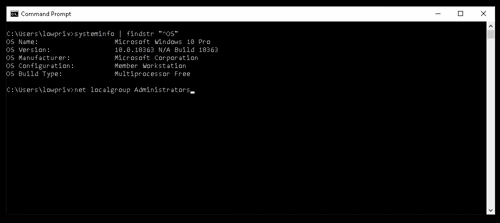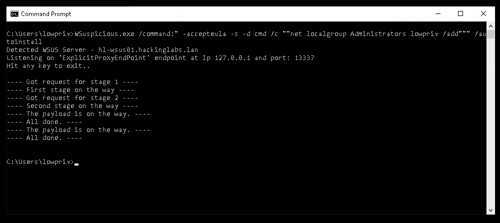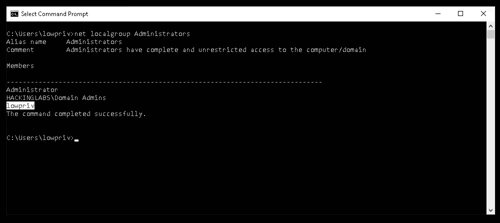
WSuspicious
This is a proof of concept program to escalate privileges on a Windows host by abusing WSUS.
CDK
It is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers without any OS dependency.
News

Sophos uncovered evidence linking the operators of the MrbMiner mining botnet to a small software development company operating in Iran. MrbMiner, is used to install cryptocurrency miners on Microsoft SQL (MSSQL) servers.
The botnet expands solely by scanning the Internet in search of MSSQL servers and subsequent bruteforce attacks on them. Once in the system, the malware operators download the assm.exe file, which they then use to gain a foothold in the system and create a new account, representing a backdoor for future access. This account, as a rule, uses the Default user name.
The last stage of the infection is to connect to a C&C server and download an application that mines Monero cryptocurrency (XMR) using the power of the infected system.

The attackers hacked into the forum of the IObit company, which is the developer of the popular suite of utilities for home PCs, such as Advanced SystemCare, in order to distribute the ransomware DeroHE.
Forum users began to receive emails with information about their free annual license and a link to the forum page, which had been compromised in advance. On this page there was an archive containing the ransomware.
When the IObit License Manager contained in it was launched, a warning was displayed about the inadmissibility of shutting down the computer during the license installation process, and files were encrypted. The ransom note contained information about the need to pay 200 DERO cryptocurrency coins, which is equivalent to approximately $ 100.
Netscout reported that it detected a new DDoS attack amplification vector through Microsoft Windows RDP servers operating over UDP port 3389. When receiving specially shaped UDP packets, the RDP server starts responding with a gain of 85.9 (up to 750 Gbps). Researchers have identified more than 14 thousand RDP servers that can be used for DDoS.
Research
Deep dive into the Solorigate second-stage activation: From SUNBURST to TEARDROP and Raindrop - Microsoft Security. Link
A day in the life of a purple teamer, to highlight how red/blue teams can work together.
MSSQL Lateral Movement – NCC Group Research: https://research.nccgroup.com/2021/01/21/mssql-lateral-movement
Really short feedback -> here
ral-movement/)
Really short feedback -> here
