Lots of zero-day vulnerabilities, and how's your start of the year?
There is one or more zero-day in each vulnerability section. Intel takes care of the threat from ransomware, the attacker gained access to Microsoft accounts, and, as usual, a little bit about the most interesting new malware with the highest impact.
- Vulnerabilities: Mostly zero-days;
- Tools: Outlook research + new tool, OSINT, web testing and defense evasion;
- News: Intel against ransomware, new malware and abused;
- Research: Not much but very useful.
Really short feedback -> here
Vulnerabilities

Microsoft releases Windows updates to patch a total of 83 newly discovered security flaws, including an actively exploited zero-day RCE vulnerability affecting Defender application.
CVE-2021-1647 was in the Malware Protection component. According to reports, it was actively used in the wild. Microsoft does not provide technical details on the vulnerability. If you are using Microsoft Defender - update urgently
https://vulners.com/cisa/CISA:F7C7CFE30EB8A6B7C1DCDEA50F649F74
https://vulners.com/malwarebytes/MALWAREBYTES:C38FDAA2A9E5E349305313C6D17A0D3A

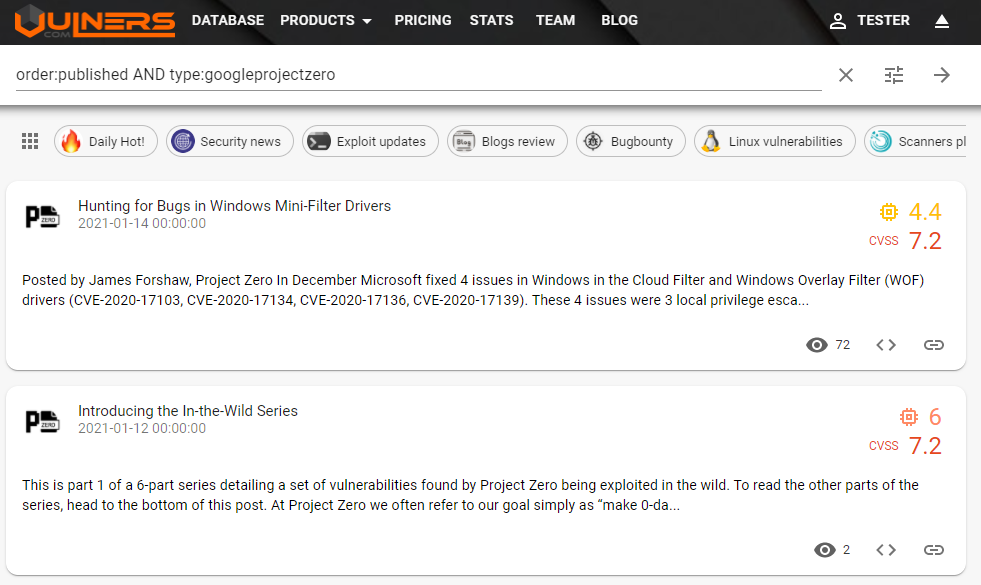
The Google Project Zero team begun to publish materials in the "In the Wild" series, in which it talks about its new program to identify the exploitation of 0-day vulnerabilities.
As part of a series of six articles, the researchers talk about a cyber campaign discovered by this program in the first quarter of 2020 to infect Windows and Android users through an attack on a watering hole.
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:7B21B608699A0775A3608934DB89577B
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:3397E6EF67D4C71C395ED0244548698A
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:9523EA61EA974CED8A3D9198CD0D5F6D
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:814DAD5293CFBE484AFB6C0462210E0D
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:17F00FE391DDA8F6294A34074EF26551
- https://vulners.com/googleprojectzero/GOOGLEPROJECTZERO:C4CBD27E9FA33882CD77C7DAC1496DD3
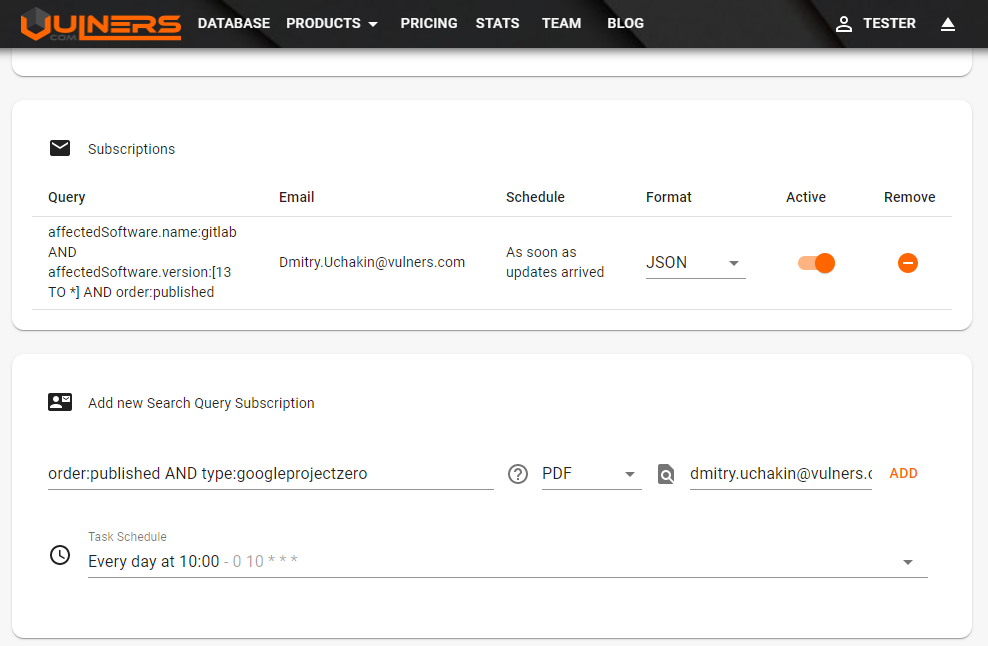
The Google Project Zero team produces incredible posts frequently. Therefore, you can subscribe to them through our subscriptions as follows:
Security researcher Jonas L focus on an unpatched NTFS vulnerability affecting Windows 10. According to the expert, the vulnerability appeared in Windows 10 (build 1803) and continues to exist in the latest version.
The vulnerability lies in the incorrect handling of one of the NTFS attributes, an attempt to access which instantly corrupts the hard drive. The most interesting thing is that the malicious command can be hidden in a Windows shortcut, which doesn't even need to be opened. The vulnerability is triggered by simply opening a folder containing this shortcut. The exploitation methods are numerous, including remote ones.
https://vulners.com/attackerkb/AKB:7D2AA7FE-2311-4FBE-B5E4-130D2602F980
Tools

Collecting materials for each new post, we find the most interesting and non-standard tools. Check out the release of a new tool that helps stealing NetNTLM Hashes via Outlook Signatures:
https://github.com/nccgroup/nccfsas/tree/main/Tools/Sigwhatever

**Token-Hunter
**Collect OSINT for GitLab groups and members and search the group and group members’ snippets , issues , and issue discussions for sensitive data that may be included in these assets.
https://vulners.com/kitploit/KITPLOIT:7822299295723551865

A cli for cracking, testing vulnerabilities on Json Web Token (JWT).
https://vulners.com/kitploit/KITPLOIT:6633342161631791813
SysWhispers
It helps with evasion by generating header/ASM files implants can use to make direct system calls.
https://vulners.com/kitploit/KITPLOIT:2540835356600323182
News
Experts have discovered a new remote access Trojan for Android Check Point researchers found that a malware developer known as Triangulum has teamed up with a certain HeXaGoN Dev to release a new malware called Rogue. Malware for Android is capable of intercepting control of victims' devices and stealing data, including photos, geolocation data, contacts and messages. The new combination of two old malware is up for sale on hack forums for just $ 29.99 a month or $ 189.99 indefinitely.
https://vulners.com/hackread/HACKREAD:B3C126964CC3A28A6A8F01F96CEB0CBE

Attackers abused Mimecast's certificate to access Microsoft 365 accounts. Mimecast, which develops cloud-based email management products, warned its customers that an unknown hacker had one of its digital certificates in his possession. The attacker abused it to gain access to some Microsoft 365 customer accounts.
A law enforcement and third-party cyber forensics team is currently investigating the incident.

Intel: the next generation of Core vPro processors will receive protection from ransomware at the hardware level. At CES, which is taking place online this year, Intel announced 11th Gen Core vPro processors with Hardware Shield and Threat Detection Technology (TDT) capabilities to detect ransomware attacks at the hardware level.
https://vulners.com/thn/THN:F53A163CB772E31FC1EF3D2D3905C1B5
Research
macOS Post-Exploitation Shenanigans with VSCode Extensions: https://www.mdsec.co.uk/2021/01/macos-post-exploitation-shenanigans-with-vscode-extensions
The best security conferences of 2021: https://techbeacon.com/security/best-security-conferences-2021
Malware:
- Obfuscated DNS Queries https://isc.sans.edu/diary/rss/26992
- Detecting Mylibot, Unseen DGA Based Malware https://blogs.akamai.com/sitr/2021/01/detecting-mylobot-unseen-dga-based-malware-using-deep-learning.html
- Advanced Emotet Updates https://www.netskope.com/blog/you-can-run-but-you-cant-hide-advanced-emotet-updates
Sailing Past Security Measures In AD: https://luemmelsec.github.io/Circumventing-Countermeasures-In-AD
Really short feedback -> here
ng Past Security Measures In AD: https://luemmelsec.github.io/Circumventing-Countermeasures-In-AD
Really short feedback -> here
