Monthly digest not just about FireEye and SolarWinds hacks

The last monthly digest this year turned out to be intense and interesting. There was a lot of news about various hacks and attacks, new methods of attacks were invented and new malware was discovered. Bottom line of this month: supply chain attacks exist and the secure Security Development Lifecycle is VERY IMPORTANT!
- Vulnerabilities: Apple updates, rare Vulnerabilities, eternally vulnerable WordPress, and never-fixable ICS vulnerabilities;
- Tools: The author liked Depix best this month, but there were other cool tools as well;
- News: FireEye -> SolarWinds, Vietnamese supply chain and what prompted the researchers to LIGHT the laser into the MICROPHONE???;
- Research: Black hat videos, PCAP collection and others.
Really short feedback (why not?) -> here
Vulnerabilities

Remotely stealing cookies from Firefox for Android by visiting an exploit website CVE-2020-15647.
This vulnerability occurs due to an incorrect content Provider configuration, strange file handling inside Firefox and a little magic with iframe. Cool article, with all the proofs, gifs and a clear description of what happens at each stage.

VMware this month released a security update for SD-WAN Orchestrator that addresses multiple vulnerabilities, including those that could allow a remote user to execute arbitrary SQL queries against the CVE-2020-3984 database, gain unauthorized access to the limited functionality of CVE-2020-3985, perform CVE-2020-4000 directory traversal attacks, or gain unauthorized access to CVE-2020-4001.
The US National Security Agency issued a warning that Russian hackers are exploiting a recently discovered vulnerability CVE-2020-4006 in VMware products to install malware on corporate networks in order to steal confidential information.
https://vulners.com/cisa/CISA:040FDAD04D5D46EE1B966151F70C1621

Experts from GitHub Security Labs have discovered a critical vulnerability in the official German Corona-Warn-App CWA application for tracing contacts with patients with coronavirus infection COVID-19. Its exploitation could allow an attacker to remotely execute arbitrary code.
The vulnerable code was in the Submission Service, a microservice built on top of the Spring Boot framework and responsible for validating information submitted by CWA users. To do this, the SubmissionController function is used, which checks various aspects of the information provided by the user.
The team of experts informed SAP about their findings and worked with it to fix the problem.
https://vulners.com/threatpost/THREATPOST:F650274A7E614024DDE8B01C84114DA0

Apple released another security update for its macOS lineup - Big Sur, Catalina, and Mojave. The updates fix 58 vulnerabilities, including some that lead to remote code execution (RCE). Most of the bugs are related to the latest Big Sur. https://vulners.com/apple/APPLE:HT211931
Plus, the 14.3 updates for iOS and iPadOS were recently released, among the fixed vulnerabilities there are also many such that lead to RCE: https://vulners.com/apple/APPLE:HT212003
It's recommended that users of apple devices update urgently. Faster.

Zabbix before 5.x allows stored XSS in the URL Widget.
Exploit (PoC): https://vulners.com/exploitdb/EDB-ID:49202

Pedro Ribeiro and Radek Domanski added a module from the Pwn2Own Miami 2020 competition that uses Rockwell FactoryTalk View SE 2020, the industrial application monitoring software from Rockwell Automation. This module combines five different vulnerabilities to execute code without authentication. FactoryTalk View SE remotely provides several REST endpoints in Microsoft IIS that can be used to remove a file to the IIS server directory. Vulnerabilities: CVE-2020-12027, CVE-2020-12028, and CVE-2020-12029.

The developer of a common WordPress plugin called Contact Form 7 has released a fix for the dangerous vulnerability CVE-2020-35489 the exploitation of which allows an unauthorized attacker to take control of a website.
The vulnerability allows an unauthorized user to bypass any limitations of the file-type form in Contact Form 7 and upload an executable binary file to the site running the vulnerable version of the plugin. In addition to taking control of a vulnerable website, an attacker can also take control of the server hosting the resource, if containerization is not used, the researchers say.
https://vulners.com/threatpost/THREATPOST:0E15C66722D04D8B54AE59F8976CEDAF
Tools
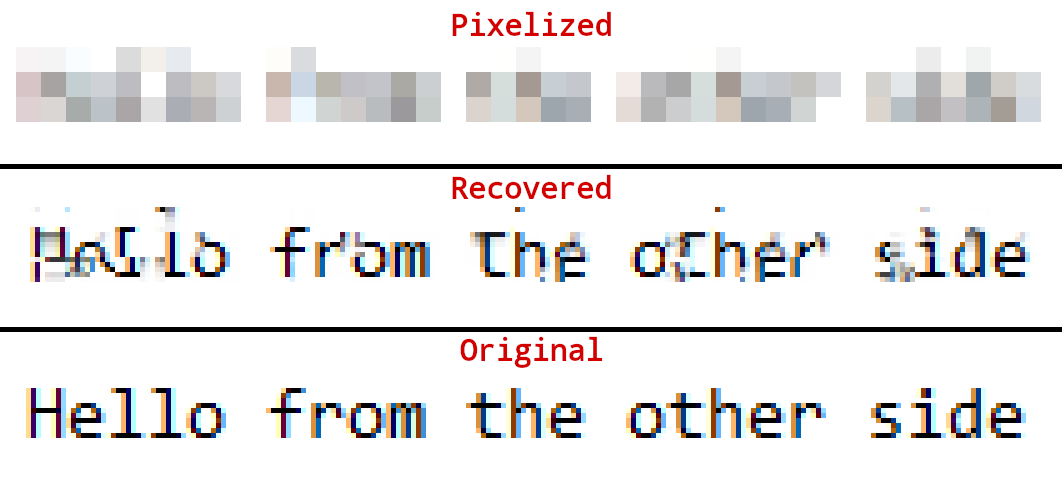
Depix is a tool for recovering passwords from pixelized screenshots | Actually a red team tool, but it's important that the blue side of this world is aware of this as well.
https://vulners.com/kitploit/KITPLOIT:4183330359513990152
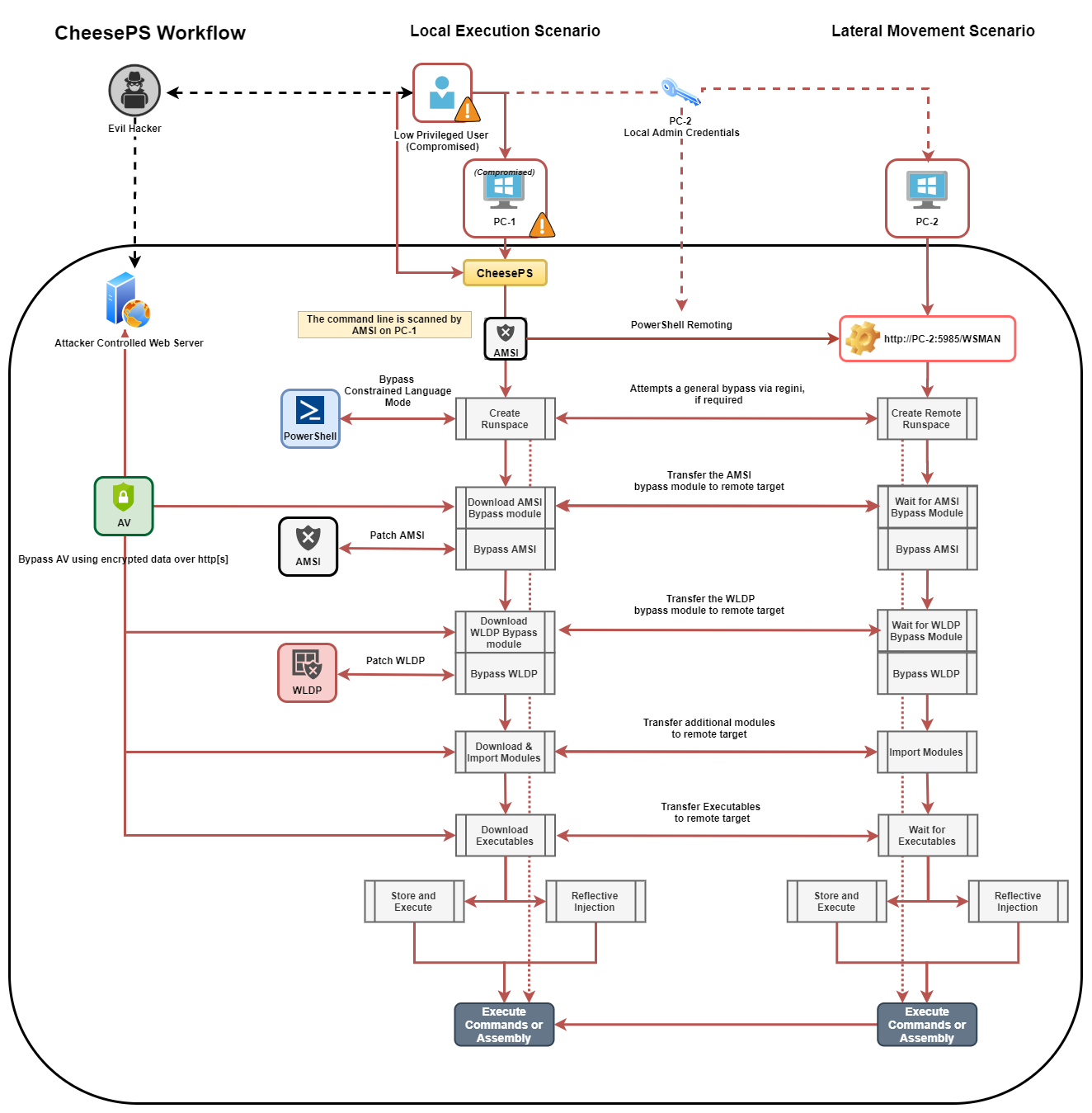
CheeseTools: Self-developed tools for Lateral Movement/Code Execution.
https://github.com/klezVirus/CheeseTools
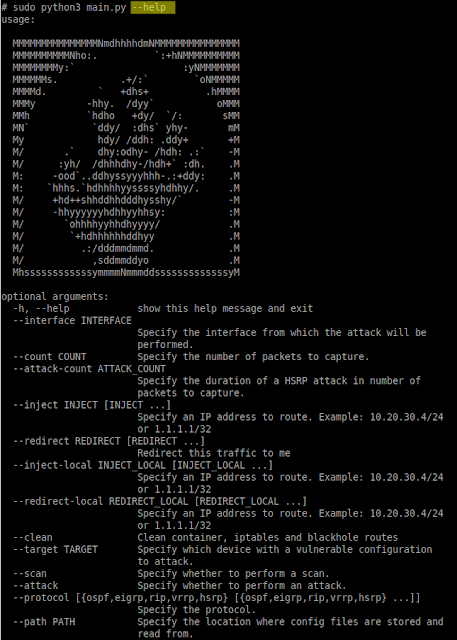
Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic Routing Protocols and First-Hop Redundancy Protocols. Most of the attacks currently implemented make use of a weaponised ‘virtual router’ as opposed to implementing protocols from scratch. The tooling is not limited to the virtual routers, and allows for further attacks to be implemented in python3 or by adding additional containers.
https://vulners.com/kitploit/KITPLOIT:7554343162461014135
Galer: A fast tool to fetch URLs from HTML attributes by crawl-in.
https://github.com/dwisiswant0/galer

enum4linux-ng is a rewrite of Mark Lowe’s (former Portcullis Labs now Cisco CX Security Labs) enum4linux.pl, a tool for enumerating information from Windows and Samba systems, aimed for security professionals and CTF players
https://vulners.com/kitploit/KITPLOIT:6656296684263688913
News

This month we already wrote about the FireEye hack in a previous post. Let's continue.
FireEye has released a report on the identified large-scale cyber operation carried out using a backdoor dubbed SUNBURST. The hackers previously carried out an attack on the supply chain - they hacked into the American supplier of IT products SolarWinds and introduced SUNBURST into the legal installer of Orion software (this is a network management system - NMS). According to FireEye estimates, the date of the compromise of the company is March-May 2020.
FireEye reports that the networks of many SolarWinds customers around the world - in North America, Europe, Asia - have been compromised. In this case, the goals are not only government organizations, but also companies in various sectors of the national economy - consulting, telecom, technology, mining, etc.
SolarWinds filed a report with the US Securities Commission (SEC), in which it said that out of 33,000 of its clients using the compromised SolarWinds Orion software, less than 18,000 downloaded the infected update. Yes, 18,000 computer networks around the world have downloaded this misunderstanding.
https://vulners.com/thn/THN:6B90D9183C3AAA5CD727DF908307EA53
Additional info:
SolarWinds Exposed FTP Credentials Publicly in a Github Repo: https://savebreach.com/solarwinds-credentials-exposure-led-to-us-government-fireye-breach
Elastic Security provides free and open protections for SUNBURST: https://www.elastic.co/blog/elastic-security-provides-free-and-open-protections-for-sunburst
SolarWind F*ckups:
- After the publication of information about the hack in the media and the scandal that followed, SolarWinds did not bother to remove several infected assemblies from their server.
- SolarWinds' technical support page advised users to disable anti-virus scanning of files and folders of NMS Orion (which was just infected with the Trojan).

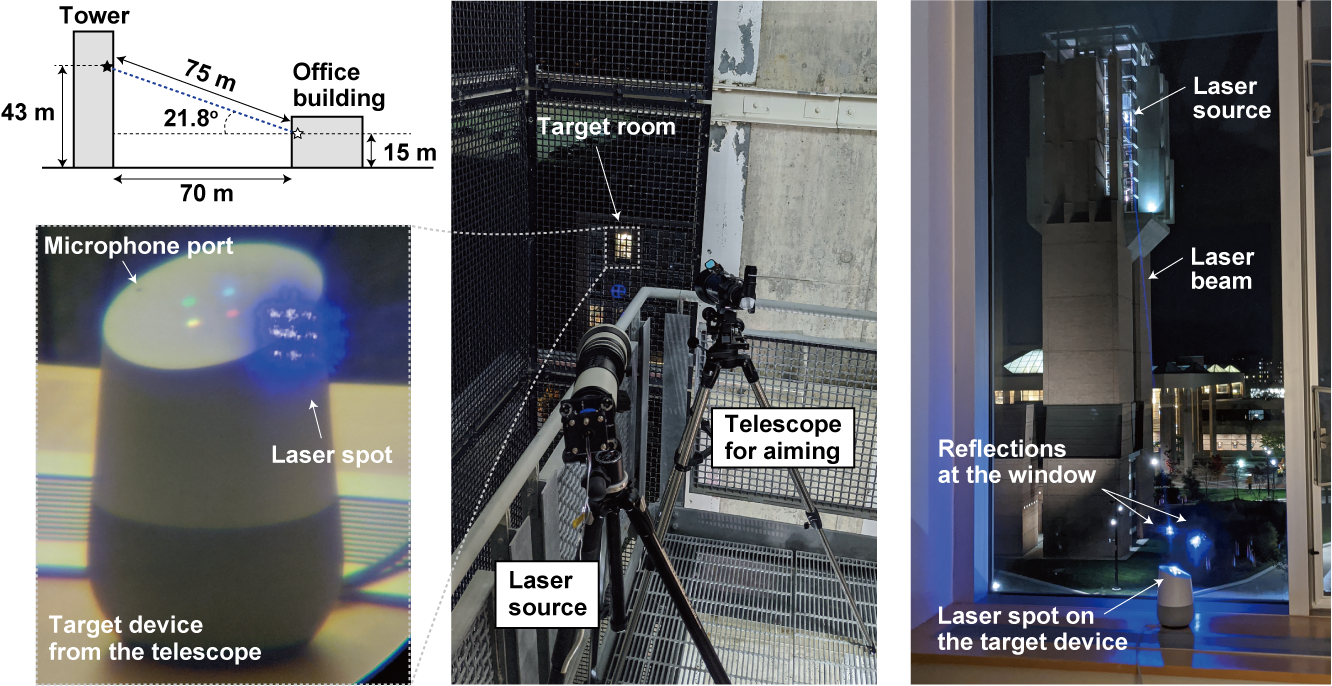
Last year, researchers from the University of Michigan and Tokyo Electric Communication University discovered the attack.
They found that directional laser beams from MEMS microphones, which are heavily used by home voice assistants like Amazon Alexa, Apple Siri, and Google Assistant, were somehow taken as sound. Thanks to this, the reservers, by changing the intensity of the laser beam, were able to send inaudible commands to the voice assistant from a distance of up to 110 meters and thus intercept its control. And the glass is not an obstacle for this.
Nevertheless, they haven't figured out the reason why this happens in the past year. Reserchers are now trying to investigate, on a physical level, why microphones respond to light as they do to sound. At the same time, they are fine-tuning the attack mechanism by trying it out on new versions of voice assistants.
https://vulners.com/threatpost/THREATPOST:38074E668BC178B8DDED7F5126F4EB88
A group of researchers from Israel's Ben-Gurion University led by Mordechai Guri reported an interesting new attack on physically isolated (air-gapped) networks via Wi-Fi signals, which does not require a Wi-Fi module in the attacked system. The attack was named AIR-FI.
In the new attack, the USB stick is used at the initial stage to deliver malware to the target machine. The next step for attackers is to infect an Internet-connected device with a Wi-Fi module on board, such as a router, located near the attacked computer.
Further, the malware collects the information of interest, encodes it and uses the DDR SDRAM bus to generate electromagnetic radiation in the 2.4 GHz Wi-Fi range. After conducting experiments the researchers found that in this way it is possible to organize a communication channel at a speed of 1 to 100 bits per second at a distance of up to several meters.
https://vulners.com/thn/THN:93B05FF3A260222D0C6B13CF5AFE7F14

Armis has dropped data regarding a set of 11 vulnerabilities in the VxWorks operating system, which powers more than 2 billion devices in industrial, medical and corporate information systems. Among those affected are SCADA systems, elevator equipment, programmable logic controllers (PLCs), medical MRI machines and more. The researchers called this set of vulnerabilities Urgent/11.
Another set of five critical vulnerabilities published and patched this February is CDPwn. The flaws were contained in the CDP protocol of Cisco equipment and affected all IoT devices manufactured by this company - switches, routing, IP-cameras, etc.
Now Armis published a fresh report, which reported that according to their analysis, 97% of OT-devices affected by Urgent/11, and 80% of IoT-devices affected by CDPwn have not been updated to a safe state since then.
The combined use of Urgent/11 and CDPwn by hackers could lead to a Stuxnet-like attack.
https://vulners.com/threatpost/THREATPOST:018A5896B52734EF63419DC7D2122C0A
Vietnamese Certification Authorities is the Vietnamese State Certification Authority (VGCA), which is subordinate to the local Ministry of Communications. VGCA, among other things, develops and distributes digital signature tools used by both government organizations and the private sector.
According to ESET, between at least July 23 and August 16 this year, the ca .gov .vn site was compromised and hosted two Smanager-infected installers. Smanager, according to NTT Security, is a variation of the RAT Tmanager used by the Chinese APT TA428.
ESET received information regarding this attack on the supply chain in early December, after which it was notified to the VGCA and the Vietnamese CERT. The Vietnamese confirmed that they are already aware of the hack and all affected users have been notified.
https://vulners.com/thn/THN:79F7B312B4A279A7C2B01047DED9E286
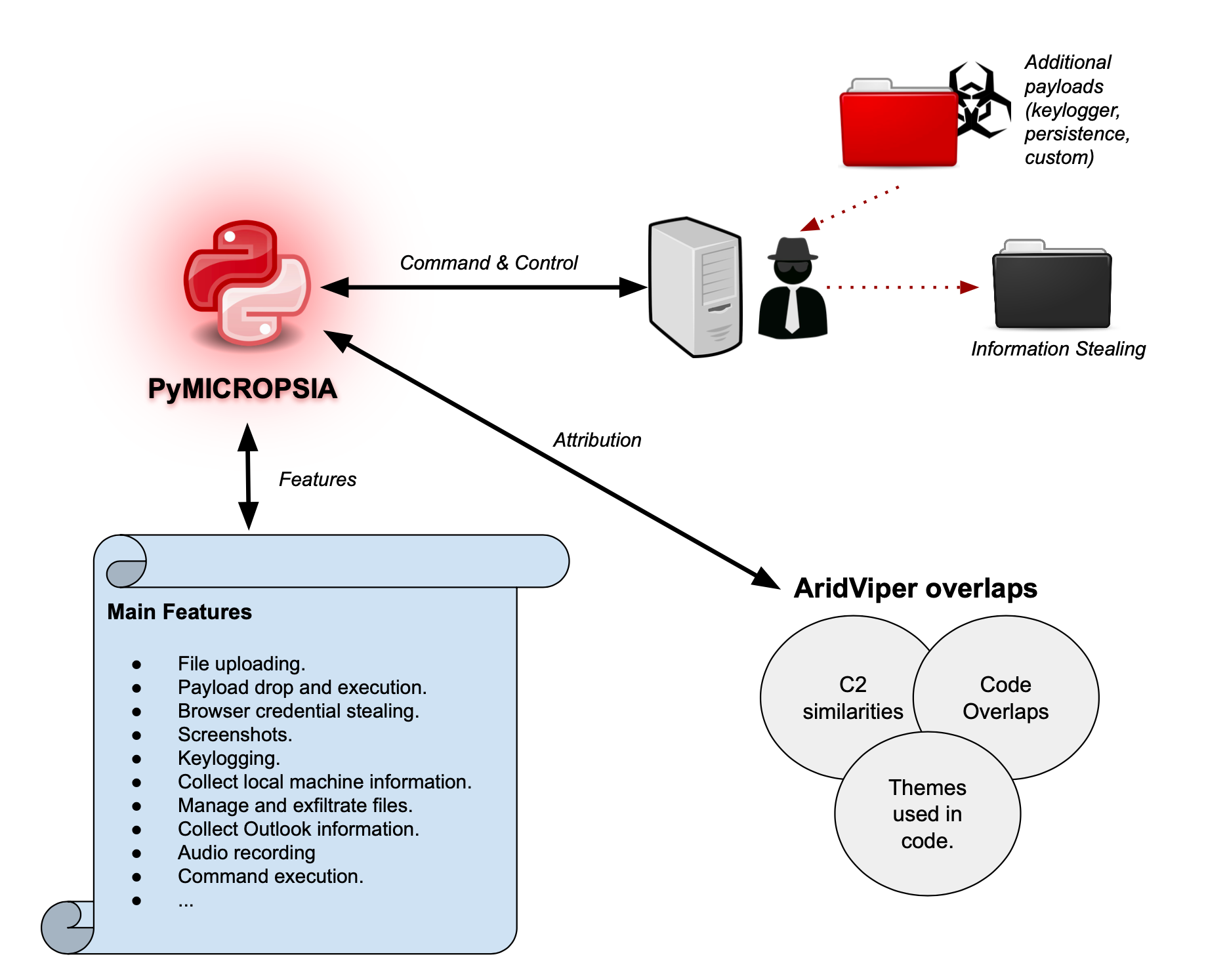
The guys at Unit42 working at Palo Alto Networks have published a report on a new type of malware called PyMICROPSIA. The authors of the malicious MICROPSIA family are considered APT AridViper aka Deserts Falcons aka Two-tailed Scorpion.
PyMICROPSIA is written in Python and is a full-fledged RAT with functions for collecting and exfiltering information, keylogging, recording audio and screenshots, etc. Analysis of the code indicates that the malware is under active development. The identified PyMICROPSIA sample is intended for Windows, but its code contains inserts that indicate the interest of the virus developers in Linux and macOS.
https://vulners.com/hackread/HACKREAD:3254A047107CD16665AF8430BE4029C4
Research
A really great repo of publicly available PCAP files - ‘cyber’ related. Worth a browser / bookmark for that time you need that PCAP! https://www.netresec.com/?page=PcapFiles
New access credential added to Application or Service Principal Azure Sentinel Alert detection rule - as used by the Solar Winds attackers: https://github.com/Azure/Azure-Sentinel/tree/master/Detections/AuditLogs
Dark Halo Leverages SolarWinds Compromise to Breach Organizations: https://www.volexity.com/blog/2020/12/14/dark-halo-leverages-solarwinds-compromise-to-breach-organizations
Information security companies Sophos and ReversingLabs announced the release of the SoReL-20M database, consisting of 20 million Windows Portable Executable files. Of these, 10 million files are malware images.
https://vulners.com/thn/THN:1CAAD105D10A43F1BAD7FB6F0C37AF2B
Top 200 most common passwords of 2020: https://nordpass.com/most-common-passwords-list
Really short feedback (why not?) -> here
tps://nordpass.com/most-common-passwords-list](https://nordpass.com/most-common-passwords-list)
Really short feedback (why not?) -> here
