Most critical vulnerabilities, next ransomware and PRE-ATT&CK

What could be more dangerous than a zero-day vulnerability that has been made public and has not yet been fixed? This is what google projecy zero did by publishing zero-day in windows before the patch. The attempts to exploit Oracle weblogic in the wild also started. But as statistics show, not everyone is in a hurry to update their systems.
- Vulnerabilities: Oracle WebLogic, zero-day from Google Project Zero and others;
- Tools: New VM machine from FireEye for hunting(like FLARE-VM or Commando VM);
- News: FBI alert, MITRE and ransomware;
- Research: New course released by Offensive Security and others mainly for pentesters.
Really short feedback -> forms.gle/qhTGPMkJMMKkec5f9
Vulnerabilities

The vulnerability is related to Oracle WebLogic (versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0) and allows compromising vulnerable systems with a simple HTTP GET request.
Exploit? What about detailed analytical research?
Yes, exploit (too easy): https://vulners.com/packetstorm/PACKETSTORM:159769
Hanypots created by SANS Institute experts have already discovered the first vulnerability attacks, as recently an exploit for CVE-2020-14882 has appeared in the public domain. So far, most of the attacks are ordinary pings of potential targets and search for vulnerable systems, although hackers operating from the MivoCloud IP address have already tried to execute the command cmd /c.
https://twitter.com/sans\_isc/status/1321627178916843520?s=20
According to Spyse, more than 3000 Oracle WebLogic servers are still available on the network, potentially vulnerable to CVE-2020-14882. Patch it?
https://vulners.com/oracle/ORACLE:CPUOCT2020
https://vulners.com/rapid7blog/RAPID7BLOG:8E02D06635B184C252A0274FC4A163A6

This week Google Project Zero published information and a PoC code for a zero-day vulnerability in Windows actively exploited by attackers in conjunction with the CVE-2020-15999 vulnerability in the Google Chrome browser (written about it in the last digest).
CVE-2020-15999 allows attacker to run malicious code in browser, and 0Day vulnerability in Windows CVE-2020-17087 is used to get out of Chrome sandbox and run code in operating system.
Vulnerability affects all versions of Windows, starting from Windows 7 and finishing with the last release of Windows 10. Google team provided Microsoft with seven days to fix the vulnerability, but the company did not meet the deadline, as a result specialists disclosed the problem.
https://vulners.com/thn/THN:7AD5261E90CC5E52D9933B8F13139A3E
https://vulners.com/malwarebytes/MALWAREBYTES:40B6CEF3C04EE6E976C145960F0C4FEE
KashmirBlack Botnet last year attacked thousands of sites powered by popular CMS, including WordPress, Joomla, PrestaShop, Magneto, Drupal, vBulletin, osCommerce, OpenCart, and Yeager. The researchers report that KashmirBlack was originally a small botnet, but over the past months it has grown to become a threat capable of attacking thousands of sites per day.
The main distribution method for KashmirBlack is to scan the Internet in search of sites that are running outdated software. The malware then uses exploits for various known vulnerabilities to hack the vulnerable site and take over its server. According to Imperva, the botnet actively abuses 16 vulnerabilities.
https://vulners.com/impervablog/IMPERVABLOG:132460062C8A11A5A73F937DEAA67CB9
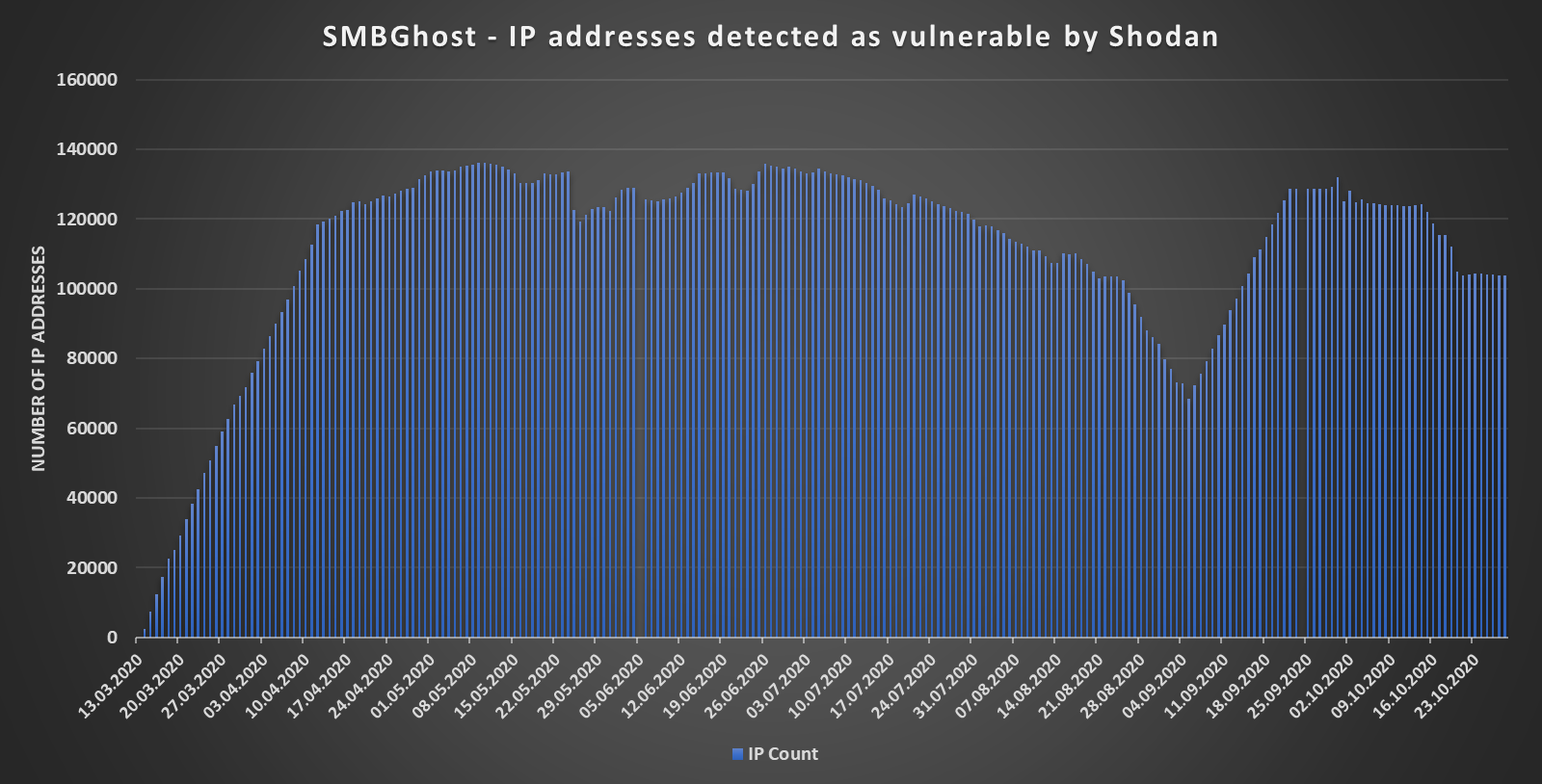
SMBGhost - CVE-2020-0796
IP addresses detected as vulnerable to SMBGhost by Shodan. According to Kopriva, many of these vulnerable resourses (22 percent) are in Taiwan, Japan (20 percent), Russia (11 percent) and the U.S. (9 percent). Microsoft released its fix, KB4551762, as an update for Windows 10 (versions 1903 and 1909) and Windows Server 2019 (versions 1903 and 1909).
https://vulners.com/threatpost/THREATPOST:38C104BCE62E9E24AEFF60D68D7C50BE
Tools
Manuka
Manuka is an Open-source intelligence (OSINT) honeypot that monitors reconnaissance attempts by threat actors and generates actionable intelligence for Blue Teamers.
https://vulners.com/kitploit/KITPLOIT:4382548335947477511

**ThreatPursuit VM
**Virtual Machine (VM) is a fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis and hunting designed for intel and malware analysts as well as threat hunters to get up and running quickly.
https://vulners.com/fireeye/FIREEYE:8E184F339E2DF14FD8EFEEB2435B7D56

**Decoder++
**An extensible application for penetration testers and software developers to decode/encode data into various formats.
https://vulners.com/kitploit/KITPLOIT:4436587334431275989
News

The FBI, Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Department of Health issued a joint statement. It says the attackers are planning a series of attacks against hospitals and other related organizations to infect them with extortionist viruses in the near future. We are talking about the Trickbot software and the target is more than 400 hospitals in the USA.
https://vulners.com/thn/THN:F7CE3EC06C8654BFA437950C0B658EF0
https://vulners.com/carbonblack/CARBONBLACK:A526657711947788A54505B0330C16A0

In Finland hacked psychotherapeutic center. The data of patients are published in the darknet. Attackers demand more than $500,000 ransom from the management of a large network of psychotherapeutic clinics in Finland, Vastaamo. Confidential information about patients has already been partially published in the dachnet, and some Vastaamo hackers contacted some customers directly.
Attackers did not started writing to the clinic, demanding a ransom, but directly to patients - they demand a ransom from patients directly, otherwise the data will be published.
https://vulners.com/threatpost/THREATPOST:4F03600A526FB9211DF15C7913BDA913

MITRE released a new, eighth version of its MITRE ATT&CK framework. Among other innovations is the integration of PRE-ATT&CK matrix with Enterprise ATT&CK matrix. The PRE-ATT&CK domain removed from ATT&CK, and two new tactics appeared in Enterprise - Reconnaissance and Resource Development.
PRE-ATT&CK, it has not received the same popularity and deposits as Enterprise ATT&CK. Enterprise ATT&CK is a collection of cybercriminal techniques and for this reason many organizations did not fully used the matrix. Therefore, the developers of MITRE began the process of integrating PRE-ATT&CK with Enterprise ATT&CK.
Enterprise ATT&CK in MITRE ATT&CK v8 received two sections:
- Intelligence - focused on the attacker trying to collect information that he can use to plan future operations, including methods of active and passive data collection.
- Resource Development - targeted at an attacker trying to install resources that he can use to conduct malicious operations, including methods that involve creating, buying or compromising/stealing resources.
https://medium.com/mitre-attack/the-retirement-of-pre-attack-4b73ffecd3d3
Research

New course meant to be the next level to OSCP released by Offensive Security: https://www.offensive-security.com/offsec/new-course-pen300
Active Directory (AD) Attacks & Enumeration at the Network Layer: https://www.lares.com/blog/active-directory-ad-attacks-enumeration-at-the-network-layer
Active Directory (AD) Attacks & Enumeration at the Network Layer: https://www.lares.com/blog/active-directory-ad-attacks-enumeration-at-the-network-layer
Really short feedback -> forms.gle/qhTGPMkJMMKkec5f9
