Vulners updated ElasticSearch 7.10 - what changes for you?
It's over! We updated our Elasticsearch from version 6.8 to 7.10! The latest version of ElasticSearch appeared on 11.11!
We use elastic stack in our service + several other technologies. We also try to keep the concept of "stay on latest" and constantly get better.
For us, there are several main advantages of updating to the most current version:
- Performance. With each release, the Elasticsearch team tries to increase the performance and efficiency of the entire stack. For example, by introducing a new snapshot search engine and using high-cost "hot" nodes to lower cost "warm" nodes with less performant disks. Searchable snapshots, a new beta feature that allows us to directly search our snapshots without a restore. "Store more and spend less"
- Improvements to the compression mechanism. Elastic tests show that the new version allows us to reduce the space taken up by up to 10% with new compression of saved fields! "be smaller, in a big way"
- Elasticsearch reduced aggregation memory consumption by maintaining serialized results, and in 7.9 they increased the search.max_buckets limit to 65,535.
- Fix tons of different bugs that were from 6.8 to 7.10.
The main benefits for our users/customers are faster search and use of all its new features. Few examples with search.
Underestimated exploits of the month with cvss score lower than Vulners AI score:
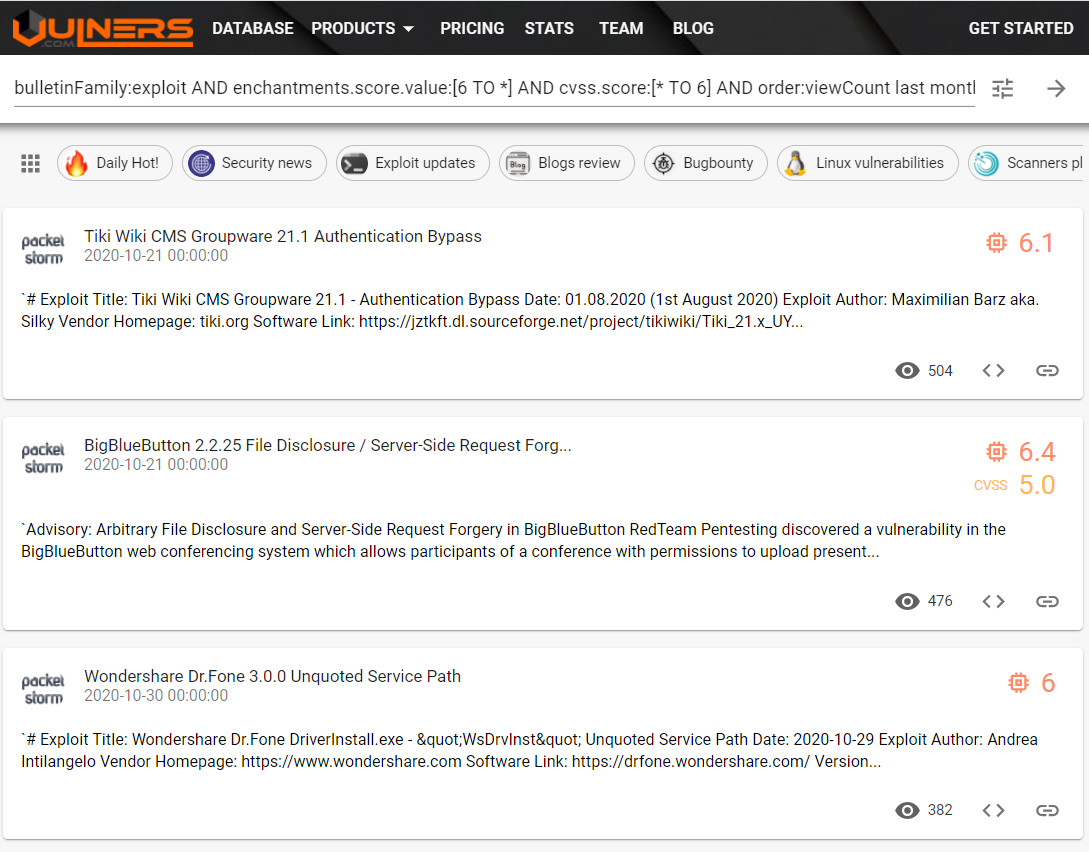
[bulletinFamily:exploit AND enchantments.score.value:[6 TO 10] AND cvss.score:[0 TO 6]](https://vulners.com/search?query=bulletinFamily:exploit AND enchantments.score.value:[6 TO 10] AND cvss.score:[0 TO 6] AND order:viewCount last month)
Google chrome releases zero-day vulnerabilities fix every week this month. Let's take a look at them:
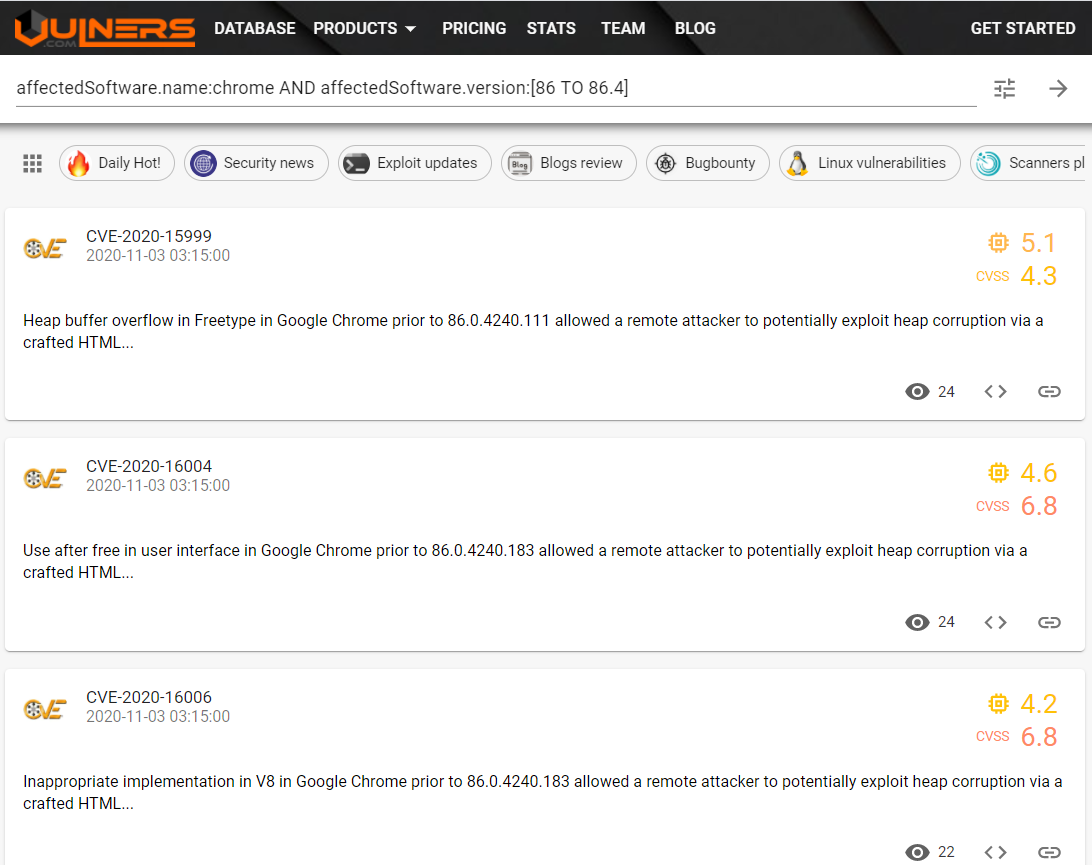
[affectedSoftware.name](https://vulners.com/search?query=affectedSoftware.name:chrome AND affectedSoftware.version:[86 TO 86.4])[:chrome AND affectedSoftware.version:[86 TO 86.4]](https://vulners.com/search?query=affectedSoftware.name:chrome AND affectedSoftware.version:[86 TO 86.4])
The same option using the vulners API wrapper:
import vulners
vulners_api = vulners.Vulners(api_key="YOUR_API_KEY_HERE")
all_short_results = vulners_api.search(
'affectedSoftware.name:chrome AND affectedSoftware.version:[86 TO 86.4]')
full_documents_info = vulners_api.documentList(
[doc_id['id'] for doc_id in all_short_results], fields=["*"])
Those who regularly use the Vulners API will feel the greater effect of the new performance.
Other example about subscriptions. Suppose you are interested in IOS and GitLab, which are so often used. New vulnerabilities are often found in this software, so you should subscribe to them:
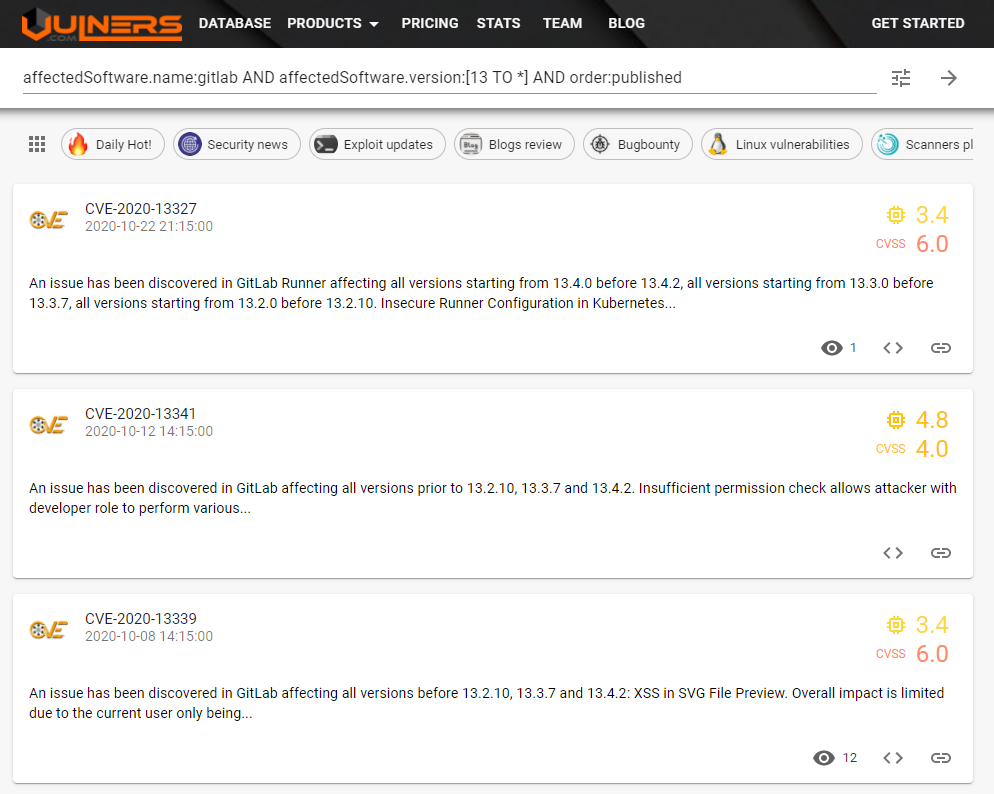
*[affectedSoftware.name:gitlab AND affectedSoftware.version:[13 TO *] AND order:published](https://vulners.com/search?query=affectedSoftware.name:gitlab AND affectedSoftware.version:[13 TO ] AND order:published)
Or if you update your software only when critical vulnerabilities appear:
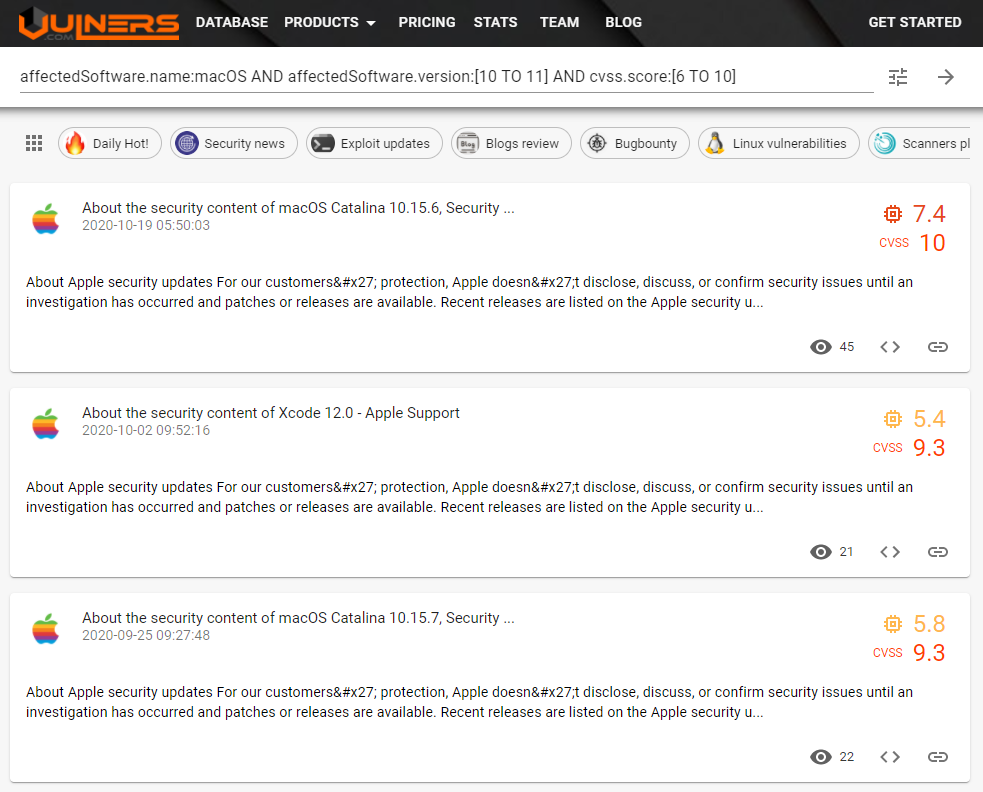
[affectedSoftware.name:macOS AND affectedSoftware.version:[10 TO 11] AND cvss.score:[6 TO 10]](https://vulners.com/search?query=affectedSoftware.name:macOS AND affectedSoftware.version:[10 TO 11] AND cvss.score:[6 TO 10])
Try our custom subscriptions:
- Go to the subscriptions page: https://vulners.com/subscriptions
- Fill all necessary fields and add new subscribe:
- Done!
Welcome!
Really short feedback -> here
