Microsoft update with zero-days, few tools, Alexa hack and research

Traditionally, Microsoft in the spotlight after monthly update
- Vulnerabilities: Microsoft patched zero-day which detected in the wild!
- Tools: Cool zeek tool and others
- News: Alexa hacked and Canon update (again)
- Research: You know what to do
Feedback -> here
Vulnerabilities

Microsoft released a monthly security update (every other Tuesday) that fixed 120 vulnerabilities, 17 of which received the highest criticality rating and two were zero-day vulnerabilities.
https://vulners.com/qualysblog/QUALYSBLOG:22507355C87630C1D3B720E2ED98701A
Main part with zero-day:
- The first 0-day vulnerability CVE-2020-1464 concerns the mechanism of checking Windows files signing and allows an intruder to download an incorrectly signed file during exploitation;
- The second 0-day, CVE-2020-1380, is in the mechanism for processing Internet Explorer scripts. Since this mechanism is also used by other Microsoft software, such as Office, these products are also subject to error. The vulnerability allows the hacker to remotely execute arbitrary code and was found in the wild.
https://vulners.com/threatpost/THREATPOST:F9CF34A304B5CA2189D5CEDA09C8B0CB
The last vulnerability was discovered by Kaspersky's lab. The day after the monthly update was released, the technical details were published. An exploit for this vulnerability was discovered in May this year during an attack called Operation PowerFall. At that time, a company from South Korea was hit.
https://vulners.com/securelist/SECURELIST:6E5BCE8A736D28A7E168E1CD5131CE3D
CVE-2020-17506
RCE at Artica Web Proxy. Solution allowing to manage proxy-server via Web Ajax console with Squid. Vulnerability allows an attacker to bypass privilege discovery and obtain web server administrator rights using SQL injection.
RCE is back (patch your vBulletin again!)
In September 2019, an anonymous researcher discovered a dangerous zero-day vulnerability in the forum engine vBulletin. The bug allowed any PHP command to be executed on a remote server. Amir Etemadieh said on his blog that the patch for CVE-2019-16759 was ineffective, could be bypassed and the bug could still be exploited by attackers.
A fix for this bug was released just a day after the problem was disclosed, but not everyone has yet managed to install the update in time.
curl -s http://SITE/ajax/render/widget_tabbedcontainer_tab_panel -d 'subWidgets[0][template]=widget_php&subWidgets[0][config][code]=echo%20shell_exec("id"); exit;'
Exploit: https://vulners.com/packetstorm/PACKETSTORM:158830
https://vulners.com/thn/THN:7EC88D1EE2BF2C54F23228C61EC1A5B0

Combo of Cisco 7937G vulnerabilities:
- CVE-2020-16139 denial-of-service (with reset);
- CVE-2020-16138 denial-of-service;
- CVE-2020-16137 Change SSH credentials.
Good luck in your internal pentests!
Tools
This analyzer parses GQUIC traffic in Bro/Zeek for logging and detection purposes. It examines the initial exchange between a client and server communicating over GQUIC, and extracts the information contained in the connection's client hello packet and server rejection packet. Currently, this protocol analyzer supports GQUIC versions Q039 to Q046.
https://engineering.salesforce.com/gquic-protocol-analysis-and-fingerprinting-in-zeek-a4178855d75f

**AWS Report
**It is a tool for analyzing amazon resources.
https://vulners.com/kitploit/KITPLOIT:7117215495877982328
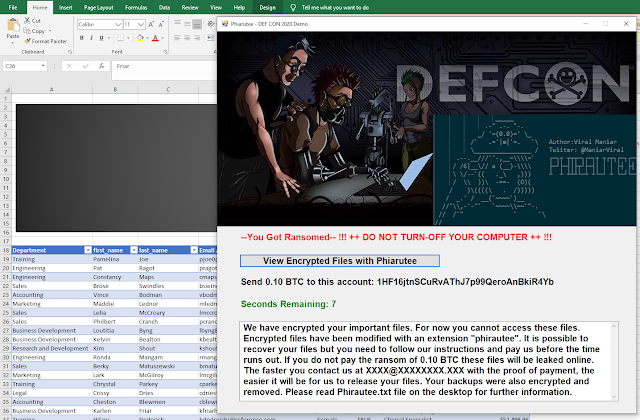
Phirautee
A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written purely using PowerShell and does not require any third-party libraries.
https://vulners.com/kitploit/KITPLOIT:8768868102969454497
Spybrowse
Code developed to steal certain browser config files (history, preferences, etc)
https://vulners.com/kitploit/KITPLOIT:805694896302514626
News

Check Point reported that it was able to hack Amazon Alexa's virtual assistant. It was reported that 200 million Alexa-powered devices were sold, a significant part of which are smart home components. Amazon says Alexa is powered by artificial intelligence. Users can enhance its capabilities using skills - additional features developed by third parties. Through this mechanism, the researchers hacked Alexa.
To carry out the attack, it is enough for the user to follow the malicious link sent to him by the attackers. Researchers with the hacked Alexa were able to obtain data: history of voice commands, personal information of the victim, technical data of the compromised device, etc.
https://vulners.com/hackread/HACKREAD:79AD386028622C0CE6DCA89D53DC5A39
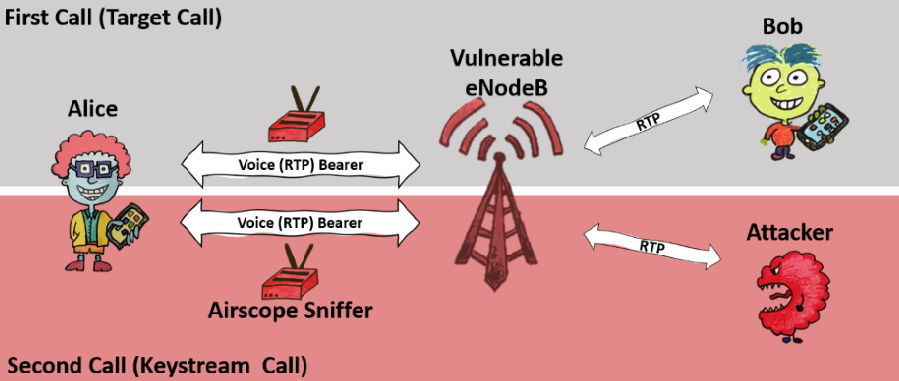
ReVoLTE Attack
This attack allows you to intercept VoLTE voice calls on 4G and 5G networks. VoLTE (Voice over LTE) - transmission of voice over LTE as a data stream. The attack is based on the fact that most mobile operators do not configure their base stations well, as a result of which VoLTE uses the same keys in two consecutive close calls.
To check the vulnerability of the ReVoLTE attack, the researchers released the Mobile Sentinel application for Android, which determines whether a specific base station is vulnerable or not. The app requires a Rooted Qualcomm-based smartphone.
https://vulners.com/hackread/HACKREAD:79AD386028622C0CE6DCA89D53DC5A39

Canon was able to restore the functionality of their systems in a short time, which indicates the presence of a backup, but they did not pay the ransom and Maze began to publish the data stolen from the company.
So far, the attackers claim that they have posted only 5% of the stolen information on their website. The published file is a 2.2 GB STRATEGICPLANNINGpart62.zip archive. No critical data available.
https://vulners.com/threatpost/THREATPOST:EEF9880D43A9ACF1F1B522C1B6D2EF09
Research
New redteaming story, hope you guys enjoy it!
https://medium.com/@securityshenaningans/chaining-multiple-vulnerabilities-to-exfiltrate-over-250gb-of-pia-2d624f030ed1
Did you play in Open SOC? Informative write-up: https://pberba.github.io/security/2020/08/11/defcon-28-blueteam-opensoc-ctf
Windows Debugger API — The End of Versioned Structures:
https://medium.com/swlh/windows-debugger-api-the-end-of-versioned-structures-ac4acaa351bd
List of bug bounty writeups (2012 - 2020): https://pentester.land/list-of-bug-bounty-writeups.html
Feedback -> here
