The two most important conferences of the year and new facebook tool

This week there were such significant events as Defcon and Black Hat 2020. Some of the materials from these conferences are in today's digest.
- Vulnerabilities: Cool material from Blackhat 2020 and Qualcomm vulnerabilities.
- Tools: New code analyzer from facebook.
- News: Data leak and ransomware for Canon (like Garmin).
- Research: Mostly for the blue/purple teams.
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities

At Black Hat 2020, Patrick Wardle from Jamf talked about a chain of exploits that can bypass Microsoft's protection against malicious macros to infect MacOS devices. The vulnerabilities were named zero-click, meaning that no victim's involvement is required to exploit them. They allow attackers to deliver malware to macOS users using a Microsoft Office macro document. The attack bypasses security measures that Microsoft and Apple have adopted to protect macOS users from malicious macros.
The researcher reported his findings to Microsoft and Apple. Apple fixed the problems in macOS version 10.15.3, but told Wardle that "this problem does not meet the requirements for assigning a CVE identifier". Microsoft said the exploit chain is an issue on Apple's side.
https://vulners.com/threatpost/THREATPOST:48A7F6CD18D7D2DFFF96F9217C6B1D5E

Researchers from the Eset company have identified a new vulnerability variant Kr00k CVE-2020-3702, in wireless chips Qualcomm and MediaTek. Like the first variant to which Cypress and Broadcom chips were exposed, the new vulnerability allows decrypting intercepted Wi-Fi traffic protected using WPA2 protocol.
https://securityaffairs.co/wordpress/106889/hacking/kr00k-variant-qualcomm-mediatek.html

Black Hat USA 2020 researcher Jiahao Lee from 360 Group spoke about 19 identified vulnerabilities in the Mercedes-Benz E-Klasse, which were subsequently patched by the manufacturer. Until the moment of correction, more than 2 million vehicles were potentially affected. These errors were first reported in August last year and now the researchers have revealed technical details.
https://vulners.com/threatpost/THREATPOST:50210848F5C0B6804DBF8A398FD41F24
Features in Microsoft Teams 
Microsoft Teams is still vulnerable to a vulnerability that allows remote extraction and launch of malware. The method was originally unveiled last year and is based on using the "update" command to run arbitrary binary code in the context of the current user. Before Microsoft introduced measures to prevent exploitation of the vulnerability, an attacker could download malware from an external URL and install it on the system from a trusted (signed) executable file.
A patch for the discovered vulnerability is unlikely to appear, as Microsoft has called it a design flaw, and the patch could have a negative impact on the operations of some customers.
https://vulners.com/threatpost/THREATPOST:D819574E836325FD37CCA2E8B9E979A1
Tools

Pysa
Facebook introduced an open source static analyzer Pysa (Python Static Analyzer) designed to identify potential vulnerabilities in Python code. The new analyzer is designed as an add-on over the Pyre type checking toolkit and placed in its repository. The code is published under the MIT license.
https://engineering.fb.com/security/pysa
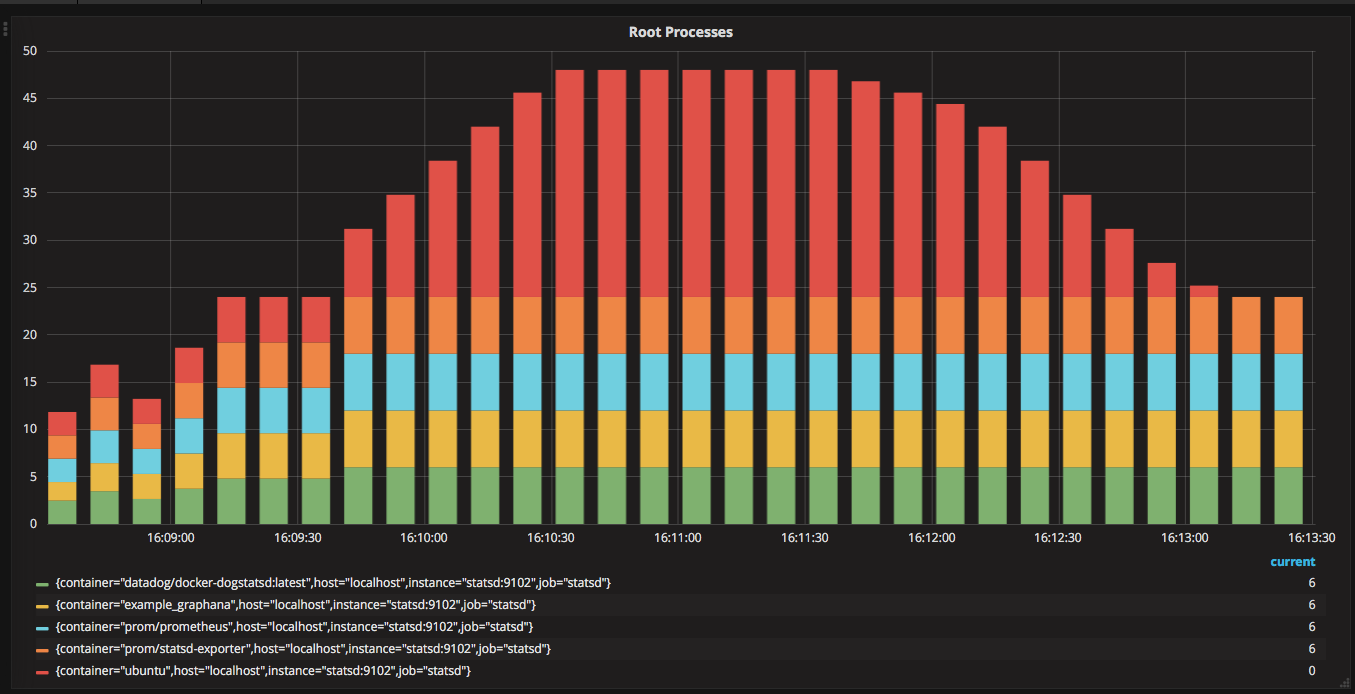
Cnitch
It is a simple framework and command line tool for monitoring Docker containers to identify any processes which are running as root.
https://vulners.com/kitploit/KITPLOIT:8323424105442512397
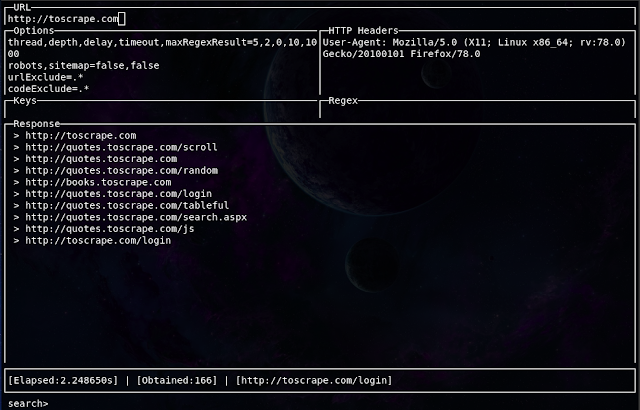
Evine
It is a simple, fast, and interactive web crawler and web scraper written in Golang. Evine is useful for a wide range of purposes such as metadata and data extraction, data mining, reconnaissance and testing.
https://vulners.com/kitploit/KITPLOIT:1538150805868015968
News
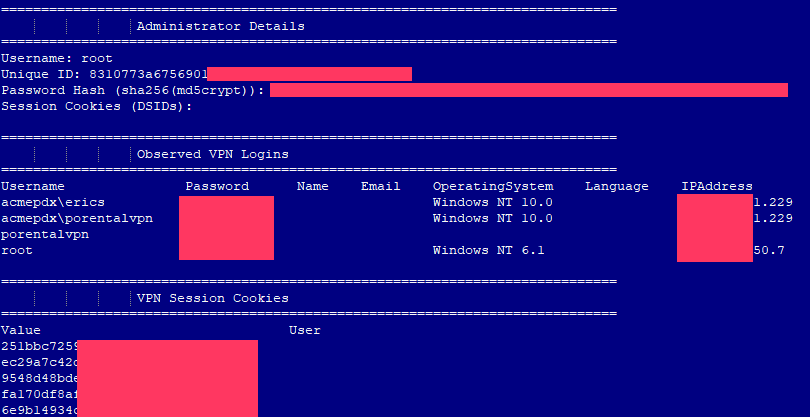
KELA provided journalists with a list of more than 900 corporate Pulse Secure VPN servers with complete data about them, including logins and passwords. The list was distributed at a Russian-language hacker forum actively used by ransomware operators and compiled by an attacker between June 24 and July 8, 2020. Apparently, the hacker used CVE-2019-11510 to get data from vulnerable VPN-servers.
677 companies have not yet installed patches, although Bad Packets experts conducted their first scan for vulnerable servers back in June 2019. The researchers note that even if these companies install patches now, they will still need to change passwords so that hackers don't use the leaked data to capture devices and then develop attacks on internal networks.
https://vulners.com/hackread/HACKREAD:C9A40CAE11DFA1F776A25997A4419BE5

Canon was subjected to a ransomware cyber attack that affected several of its services, including email, Microsoft Teams, Canon's US website and a number of internal applications. image.canon went for maintenance on July 30, which lasted until August 4.
The journalists turned to Maze for a comment and they said that they indeed successfully hacked Canon yesterday morning and stole more than 10 TB of information, including databases, correspondence, etc. The hackers did not disclose the amount of the ransom.
https://vulners.com/threatpost/THREATPOST:EEF9880D43A9ACF1F1B522C1B6D2EF09

Cybersecurity researchers from Malwarebytes talked about a phishing technique in which attackers use homoglyph domain names and modified favicons (website icons) to deploy electronic skimmers and steal data from users' payment cards.
The idea is to use similar-looking symbols to visually trick users. Homoglyph is one of two or more graphemes, signs or glyphs with shapes that either appear identical or cannot be differentiated by a quick visual inspection. For example, Russian "c" and English "c" are homoglyphs.
Attackers used visual similarities to create and register fraudulent versions of existing domains in order to deceive unsuspecting users and force them to visit malicious web sites.
https://vulners.com/malwarebytes/MALWAREBYTES:FFAEA6CD64E911875212E223F0F8303B
Research
Userfull and fresh research for forensics, incident resonse and threat hunters:
https://www.blackhat.com/us-20/briefings/schedule/#detecting-access-token-manipulation-20524
Incident Response: Methodology and Case Study: https://fireh7nter.com/2020/08/04/incident-response-methodology-and-case-study
Build a server 2019 core AD lab walkthrough and a brief how to attack it guide: https://www.pentestpartners.com/security-blog/building-a-lab-with-server-2019-server-core-and-powershell-then-attacking-it/
Fuzzing the Windows API for AV Evasion: https://winternl.com/fuzzing-the-windows-api-for-av-evasion/
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
