Monthly review with zero-day in the wild, BootHole and news about Garmin with "Tamagotchi for hackers"

In this monthly review, the most interesting materials of the month that were not included in previous weekly digests:
- Vulnerabilities: Updates from Apple and Claroty (ICS). Valuable information about zero-day vulnerabilities and etc.
- Tools: This month's most important tools.
- News: Amazing startup, more information aboout attack on a Garmin company and new security features in IOS 14!
- Research: Someone will always be interested in cool research.
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities
Briefly about vulnerabilities of the month:


A remote code execution vulnerability in Microsoft SharePoint was included in the latest monthly update from Microsoft.
The vulnerability is present in two .NET components (DataSet and DataTable) used to manage datasets and affects Microsoft SharePoint, .NET Framework, and Visual Studio. The issue is related to insufficient validation of the tagging source of the input XML file. By exploiting the vulnerability, an attacker could execute arbitrary code in the context of the process responsible for deserializing the contents of the XML file. To do this, attacker must upload a specially configured document to a server that uses one of the vulnerable products to process the contents of an XML file.
Exploitation of empirical deserialization is much more likely compared to other vulnerabilities from the update release
Exploit: https://vulners.com/metasploit/MSF:EXPLOIT/WINDOWS/HTTP/SHAREPOINT_DATA_DESERIALIZATION

Fast research for couple vulnerabilities - CVE-2020-9934 and CVE-2020-9854.
- CVE-2020-9934: https://medium.com/@mattshockl/cve-2020-9934-bypassing-the-os-x-transparency-consent-and-control-tcc-framework-for-4e14806f1de8
- CVE-2020-9854: https://objective-see.com/blog/blog_0x4D.html
15 Jul 2020: Apple releases patch for the bug (Security Update 2020–004)

GNU GRUB2 (Grand Unified Bootloader) has discovered an epic vulnerability.
Almost all versions of the popular GRUB2 boot loader, used in most Linux distributions, are vulnerable to this dangerous vulnerability. With its help, an attacker can compromise the boot process of the operating system even when Secure Boot is enabled.
BootHole allows arbitrary code execution during the OS boot process even when Secure Boot is enabled and consists in incorrect GRUB2 processing of its configuration file (which is not usually signed), which can lead to buffer overflow. The vulnerability was identified by researchers earlier this year and was identified as CVE-2020-10713.
https://gist.github.com/SwitHak/b196844cdc334c84f4e30e3f6efe7a6c
https://vulners.com/thn/THN:885767C284ED14ED2B32F6713F9AA21F

Claroty, a company specializing in industrial information security, has issued a report describing the identified vulnerabilities in VPN solutions for industrial networks. These solutions are mainly focused on industrial automation systems (ICS).
Vulnerable VPN products are used in the oil and gas, water and electricity industries - in general, in more than critical areas of modern life. Errors were detected in Secomea GateManager, Moxa EDR-G902 and EDR-G903, as well as in the eWon eCatcher VPN client from HMS Networks.
https://vulners.com/threatpost/THREATPOST:3C7643A12EE5AC251B015BA884447D7B
https://vulners.com/thn/THN:13D952B7F174C224BB03A3F05C132DC1
CVE-2019–1367
Over time, some vulnerabilities are successfully exploited by different groups. An example of such vulnerability is vulnerability. A complete overview of the APT and attacks in which it was observed: https://blog.confiant.com/internet-explorer-cve-2019-1367-in-the-wild-exploitation-prelude-ef546f19cd30

In the first half of 2020, 11 zero-day vulnerabilities were recorded. According to preliminary estimates of Google Project Zero team, in 2020 there will be as many 0Day vulnerabilities as there were in 2019 - 20. Detailed information about zero-day vulnerabilities: https://docs.google.com/spreadsheets/u/0/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/htmlview#gid=1869060786
FreeBSD LPE
Local Privilege Escalation in FreeBSD (exploit). Vulnerability CVE-2020-7457 in the FreeBSD kernel IPv6 socket handling. Missing synchronization in the IPV6_2292PKTOPTIONS socket option set handler contained a race condition allowing a malicious application to modify memory after being freed, possibly resulting in code execution.
https://vulners.com/metasploit/MSF:EXPLOIT/WINDOWS/NIMSOFT/NIMCONTROLLER_BOF
Tools

FestIN
It is a tool for discovering open S3 Buckets starting from a domains.
It perform a lot of test and collects information from:
- DNS
- Web Pages (Crawler)
- S3 bucket itself (like S3 redirections)
https://github.com/cr0hn/festin
HawkScan
Security Tool for Reconnaissance and Information Gathering on a website.
https://vulners.com/kitploit/KITPLOIT:148065120186103519

Ciphey
Alternative to the Cyber Chef . This tool is worth trying in the battle against malicious activity / work tasks / CTF / etc.
https://github.com/Ciphey/Ciphey

RustScan
The first release of RustScan, a new network port scanning utility optimized for significantly increased scanning speed.
https://github.com/RustScan/RustScan
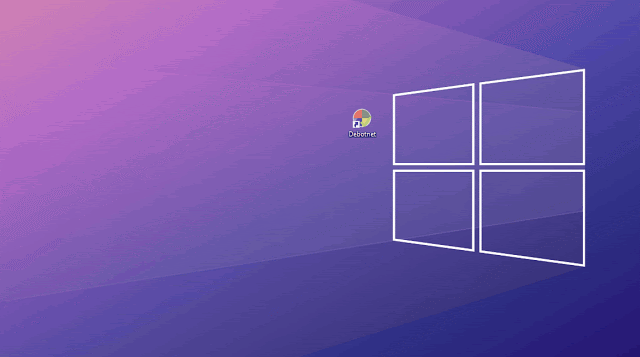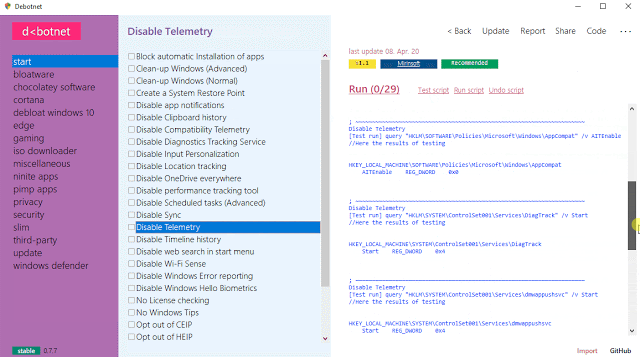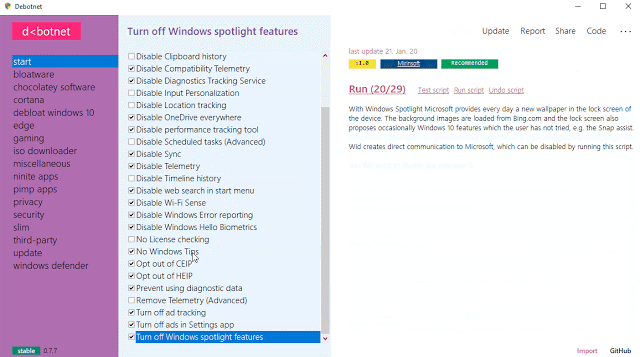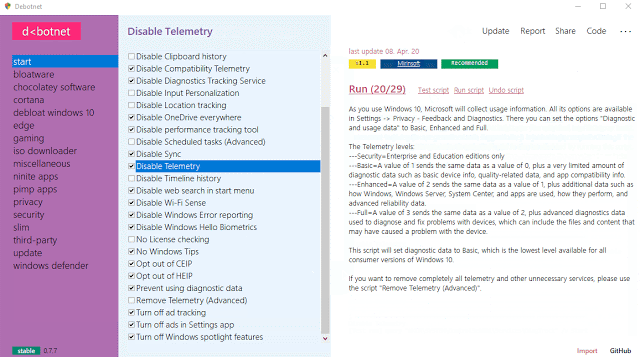
Debotnet
A free and portable tool for controlling Windows 10’s many privacy-related settings and keep your personal data private.
https://vulners.com/kitploit/KITPLOIT:8797042946162128173

**FastNetMon
**A high performance DoS/DDoS load analyzer built on top of multiple packet capture engines (NetFlow, IPFIX, sFlow, AF_PACKET, SnabbSwitch, netmap, PF_RING (obsoleted), PCAP).
https://vulners.com/kitploit/KITPLOIT:6781207822600695384
News
https://www.kickstarter.com/projects/flipper-devices/flipper-zero-tamagochi-for-hackers
Pavel Zhovner, the founder of the community for techno-enthusiasts Neuron Hackspace, raised over a million dollars on Kickstarter on Kickstarter for "Tamagotchi for hackers".
With Flipper Zero, you can control intercoms, TVs, garage doors, air conditioners and other electronic devices, as well as clone proximity cards. Inside there is a tamagotchi: a "cyber dolphin" that feeds on hacked devices.
Garmin
American company Garmin, which produces digital devices for navigation, outdoor activities and sports, could pay hackers a ransom of $10 million to restore their services. This is the opinion of computer security experts.
Garmin announced a major setback caused by the hack on July 24, and on July 28 it announced that it would restore all its services and applications in the coming days. The company refused to answer the question of whether hackers received a ransom for returning Garmin's stolen data to run its services.
The very fact of paying the ransom, i.e. the actual transfer of funds to Evil Corp, is considered by the U.S. Treasury to be a crime, so if Garmin paid to the fraudsters, the authorities will consider it as a violation of the law and will impose sanctions on the company.
Is it worth saving on information security of such damage?
https://vulners.com/securelist/SECURELIST:840AE0DB139F3BA90694A506FCCE8683
IOS 14 privicy features
Apple introduced new notifications in iOS 14 to alert users when an app accesses the clipboard. As it turns out, this behavior is present in many popular applications. Some services really need access to the clipboard to work, but others get access just like that, for no apparent reason.
One of the apps that access clipboard data on iOS devices is TikTok. According to the developers, this is how TikTok protected users from spam.
When the strange behavior of TikTok became known to the general public, its developers announced their intention to remove the anti-spam feature in the next update. The new version of the application is already in the App Store.
https://vulners.com/threatpost/THREATPOST:89CAF65B555BCDCCFFB2257F0CAFD8BD

An attack on digitally signed PDF documents called Shadow Attack. Research was conducted by scientists at the Ruhr University in Germany. The essence of the attack is to prepare a PDF document with two "layers" containing different content. When signing, one layer is visible, but later an attacker makes the other layer visible, while the digital signature is saved.
Out of 28 applications tested for working with PDF files, 15 were vulnerable to Shadow Attack. These include Adobe Acrobat Pro and Acrobat Reader, Perfect PDF, Foxit Reader and others. Currently, researchers have contacted the developers of the relevant applications and provided them with the necessary technical information to develop the updates.
https://vulners.com/trendmicroblog/TRENDMICROBLOG:C8C4950B7C1ABCC3623954974416E5A2
Research
Athor has a gift explaining hard things in an easy way. Cool write-up that's nice to read with a cup of something: https://shivangx01b.github.io/2fa_bypass
Hunting for bugs in VirtualBox (First Take)
http://blog.paulch.ru/2020-07-26-hunting-for-bugs-in-virtualbox-first-take.html
Atomic Purple Team Framework and Life Cycle:
https://github.com/DefensiveOrigins/APT-Lab-Terraform
https://www.youtube.com/watch?v=_KqtVWrw_Gc
An Analysis of Emotet Malware: PowerShell Unobfuscation: https://medium.com/picus-security/an-analysis-of-emotet-malware-powershell-unobfuscation-4f46b50dcf2b
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
