Important updates for Cisco and Adobe products, attack on Garmin and Diebold Nixdorf

This week Cisco and Adobe released Emergency updates for their products. And the biggest news of the week are the attacks on Garmin and ATM maker Diebold Nixdorf.
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities

Path traversal in Cisco's network security software CVE-2020-3452. A path traversal aims to access files and directories that are stored outside the web root folder. Potential attacker can exploit vulnerability by crafting HTTP request including directory traversal character.
To fix the vulnerability the researchers encouraged Cisco users to update the Cisco ASA to the latest version.
News and PoC: https://vulners.com/threatpost/THREATPOST:C51D2F2366676BB018956D93916AC33E
Emergency Update for Adobe Photoshop products
Updates fixed 13 vulnerabilities, 12 of which are critical and allow remote code execution. Another vulnerability was fixed in Adobe Mobile Reader for Android. To use them, a attackes needs to force the attacked user to open a malicious file like MOV, MP4 and 3GP, or follow a link to a specially created website.
If you are using these products, you should perform an update.
https://vulners.com/threatpost/THREATPOST:935FDBA342DDD020D66B791DBE0AEA4D
Weaponization against SIGred
SigRed CVE-2020-1350 update: there was already a lot of information about this vulnerability. In this section, exploits are usually published for vulnerabilities, but the link to detection research with suricata IDS rule: https://sensepost.com/blog/2020/seeing-sigred

Mida Solutions eFramework offers multiple services in a single virtual appliance in OVA format running all services. Combo with few vulnerabilities in Mida Solutions eFramework 2.9.0:
- RCE;
- cross site scripting;
- denial of service;
- remote SQL injection;
- path traversal vulnerabilities;
CVE-2020-8559 (Kubelet redirect exec)
Vulnerability allows to redirect on proxied upgrade requests that could allow privilege escalation for an attacker from a node compromise to a full cluster.
PoC: https://github.com/tdwyer/CVE-2020-8559
Tools
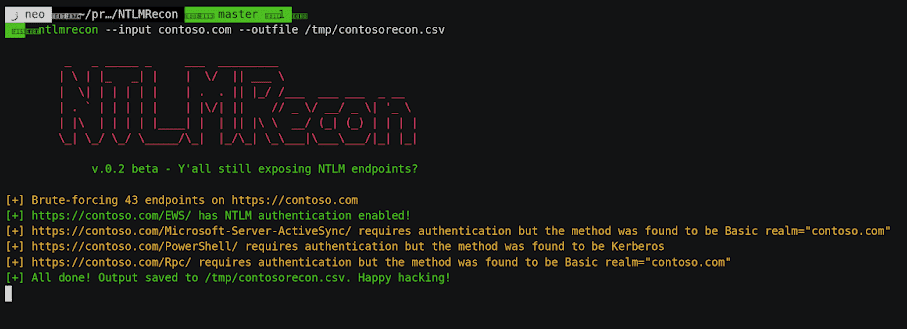
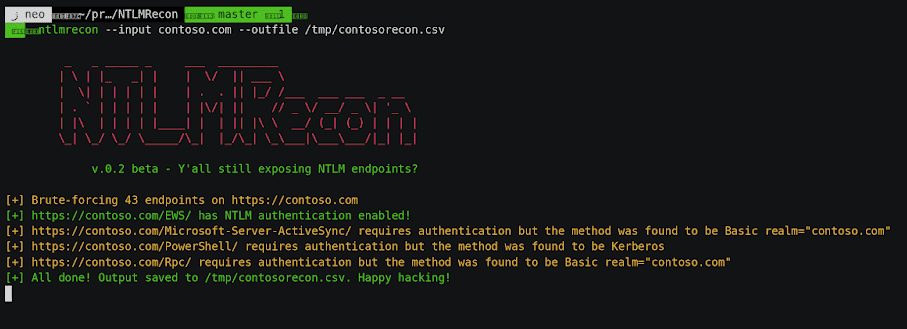
Autoenum
It is a recon tool which performs automatic enumeration of services discovered.
https://vulners.com/kitploit/KITPLOIT:8771218761728918313
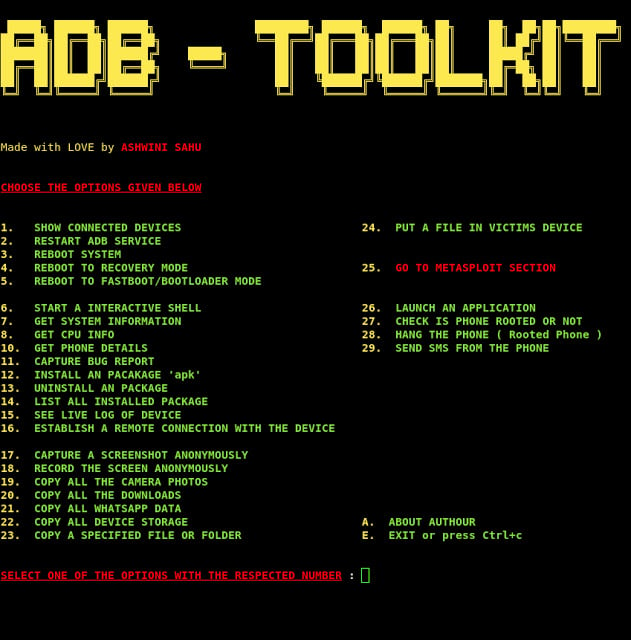
**ADB-Toolkit
**Tool for testing your Android device. ADB-Toolkit is a BASH Script with 28 options and an METASPLOIT Section which has 6 options which is made to do easy penetration testing in Android Device.
https://vulners.com/kitploit/KITPLOIT:3516084899857192644

REMnux
Linux distro is now available for malware researchers, packed with hundreds of tools to dissect malicious executables, documents, scripts, and ill-intended code.
https://remnux.org
News

Smartwatch and other gadget maker Garmin was forced to shut down a number of its online services due to a ransomware attack that encrypted its internal network and production systems.
Garmin took a few days to recover from the cyberattack and temporarily shut down the official website, Garmin Connect user data sync service, flyGarmin aviation navigation service and even some production lines in Asia. According to a Twitter post by the company, the cyberattack shut down call centers, depriving it of communication with customers.
Officially Garmin does not provide any explanations. The company manufactures mapping and tracking equipment for the automotive and shipbuilding industries. It is unknown whether user data and the impact of the entire attack were affected.
https://vulners.com/thn/THN:995F5255D00E2BBCAEAA6CDB8A5EE84B
https://vulners.com/threatpost/THREATPOST:EE45051DD8877CF5DC5BFA4E01A0B240

ATM maker Diebold Nixdorf issued an alert informing that attackers began hacking its ATMs across Europe using Black Boxes in a Jackpotting attack.
The hackers got hold of the internal software of Diebold Nixdorf ATMs and built on its basis Black Box devices that emulate the ATM software. Next, the attackers physically disassemble the front casing of the ATM to gain access to the USB cable of the CMD-V4 dispenser.
By connecting the Black Box to it, the hacker makes the ATM almost fontain with bills - hence the name of the attack Jackpotting. The main issue is the source of Diebold internal software samples.
https://vulners.com/threatpost/THREATPOST:1BC44B2402EC1BF1456FABF7A161A915

Researchers from Tencent's Xuanwu Lab team have developed a new attack called Adpower, with which it is possible to change the output voltage of fast chargers and, in some cases, set fire to the charging equipment.
Fast charges exchange information with the device being charged and, if necessary, are able to raise the voltage to the desired values. By changing the fast charging firmware, the recorders were able to exceed the maximum allowable voltage value for a specific device being charged. That is, for example, a smartphone asks for a hacked 5 V charge, and the charging gives it 20 V.
Researchers analyzed 35 fast charging models and found that 18 of them (from 8 suppliers) are vulnerable, 11 can be attacked from a pre-compromised charger. Sometimes it is enough to update the charger's firmware to fix the vulnerability.
https://vulners.com/hackread/HACKREAD:BAA7FE13C91D69CF52FBD1E3B7B319D4
Research
Automatically obfuscate API Imports for AV bypass: https://blog.scrt.ch/2020/07/15/engineering-antivirus-evasion-part-ii
So rare posts from an excellent author on AD security topics: https://dirkjanm.io/abusing-azure-ad-sso-with-the-primary-refresh-token
Become a Microsoft Defender ATP Ninja. The most complete material about ATP: https://techcommunity.microsoft.com/t5/microsoft-defender-atp/become-a-microsoft-defender-atp-ninja/ba-p/1515647
Lateral Movement for begginers: https://pentestlab.blog/2020/07/21/lateral-movement-services/amp
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
