Vulners weekly digest #14

There are 4 sections:
Vulnerabilities
Tools
News
Research
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities

Not so long ago, the 0-day vulnerability of CVE-2019-19781 was discussed in Citrix ADC and Citrix Gateway, which went unnoticed for at least a month and was used by various hacker groups.
This week, Citrix released security updates for Citrix ADC, Citrix Gateway and Citrix SD-WAN WANOP, which revealed as many as 11 new vulnerabilities that allow to bypass authentication mechanisms, increase local privileges, remotely execute code, implement denial of service and much more. To do everything to get the maximum result when penetrating corporate networks.
https://vulners.com/threatpost/THREATPOST:575F655420B93C2305DEE73F769E7E0B
CVE-2020-5902 detection bypass
Another CVE-2020-5902 operating method for remote code execution was identified, which differs from those presented earlier. It allows you to access the embedded HyperSQL or HSQLDB database and, together with authentication bypass, allows remote unauthorized code execution on the Tomcat server.
- Exploit: https://vulners.com/metasploit/MSF:EXPLOIT/LINUX/HTTP/F5_BIGIP_TMUI_RCE
- Snort rule: https://vulners.com/talosblog/TALOSBLOG:07EF8115BB6D3EE80E914E6572FFCD88
- https://vulners.com/nessus/F5_CVE-2020-5902.NASL

A PlayStation 4 user found a way to hack the console and received $ 10,000 from Sony. Data about the vulnerability is published on HackerOne.
User theflow0 told about the find on his Twitter page. An exploit in firmware number 7.02 and earlier versions in tandem with the WebKit exploit existing in firmware 6.72 and earlier versions allows you to hack the console to launch pirated games, manipulate and steal user data.
Earlier, Sony announced a program to search for bugs and vulnerabilities – the company is ready to pay from 100 to 50 thousand dollars for errors found.
Mozilla Firefox browser security bug.
Tools

Microsoft Launches Free Linux Forensics and Rootkit Malware Detection Service
https://thehackernews.com/2020/07/microsoft-linux-forensics-rootkit.html
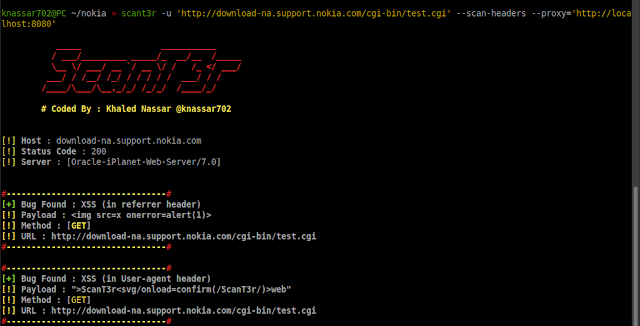
ScanT3r
Cross-platform light web security scanner
https://vulners.com/kitploit/KITPLOIT:5053244869903696578

Airshare
Python-based CLI tool and module that lets you transfer data between two machines in a local network, P2P, using Multicast-DNS. It also opens an HTTP gateway for other non-CLI external interfaces.
https://vulners.com/kitploit/KITPLOIT:8466805870741748712

Santa is a binary authorization system for macOS. It consists of a kernel extension that monitors for executions, a userland daemon that makes execution decisions based on the contents of a SQLite database, a GUI agent that notifies the user in case of a block decision and a command-line utility for managing the system and synchronizing the database with a server.
https://vulners.com/kitploit/KITPLOIT:6286724659591250825
News

July 8, the release of the new version (v7) of the MITER ATT & CK knowledge base took place. In the new version, the categories “Techniques”, “Groups” and “Software” were updated for both ATT & CK for Enterprise and ATT & CK for Mobile. Most of the new MITER ATT & CK v7 features were available in beta released in March this year.
Digital Shadows found 15 billion credentials on various trading floors on the darknet. Compromised credentials were stolen as a result of more than 100 thousand hacks and provide access to various accounts, including domain administrator accounts, banking and financial accounts, as well as social network services and streaming platforms.
According to experts, the credentials for financial accounts with confirmed cash or accounts with privileged access to networks and systems of large enterprises were sold at very high prices. At clandestine forums, dozens of advertisements for administrator accounts were found that were auctioned to bidders at prices ranging from $ 500 to $ 120,000.
https://vulners.com/threatpost/THREATPOST:86BA1E0CE60EEEE378094397278F2553

German law enforcement officers seized the BlueLeaks website web server, which stored internal documents of US police departments. The server belonged to a group of activists DDoSecrets, which published more than 1 million files in the middle of last month.
Four days after the publication of the stolen documents, the DDoSecrets Twitter account was blocked for violating the rules for using the platform prohibiting the publication of links to stolen materials. Twitter has begun blocking tweets with links to BlueLeaks.
https://vulners.com/threatpost/THREATPOST:F58BA2EB9C5D19D2AF83AACC46A88019
Research
SMB-based lateral movement in a Windows environment:
https://medium.com/palantir/restricting-smb-based-lateral-movement-in-a-windows-environment-ed033b888721
Low-Level Process Hunting on macOS:
https://themittenmac.com/low-level-process-hunting-on-macos
Top 16 Active Directory Vulnerabilities:
https://www.infosecmatter.com/top-16-active-directory-vulnerabilities
LOLbas is becoming more popular. Upload and download small files with CertReq.exe: https://dtm.uk/certreq
Other examples: https://pentestlab.blog/2020/07/06/indirect-command-execution/amp
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
