Monthly Vulners Review #3

Monthly review for the first time in four sections.
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities and exploits

Bitdefender fixed the vulnerability in SafePay, a secure browser designed to protect sensitive online transactions, such as online banking and electronic purchases. Exploitation of vulnerability CVE-2020-8102 allows an attacker to remotely execute commands in the context of a user on a system and, depending on the user's privileges, install software, view, modify or delete data, or create new accounts with full user rights.
The vulnerability is relevant for the version of Bitdefender 24.0.20. 116 and earlier. The update has already been released.
https://palant.info/2020/06/22/exploiting-bitdefender-antivirus-rce-from-any-website
Trend Micro InterScan Web Security Virtual Appliance
Metasploit module with three vulnerabilities for Trend Micro security product - InterScan Web Security Virtual Appliance.
- CVE-2020-8604: A remote attacker could potentially gain access to directories on the server, resulting in disclosure of information;
- CVE-2020-8605: An authenticated remote attacker could exploit a command injection vulnerability in the product, resulting in remote code execution (RCE);
- CVE-2020-8606: An unauthenticated attacker can bypass authentication and access part of the application as an administrator if the proxy server is configured for a specific port.
The exploit is based on a combination of three vulnerabilities. RCE + Auth bypass:
https://vulners.com/metasploit/MSF:EXPLOIT/LINUX/HTTP/TRENDMICRO_WEBSECURITY_EXEC
Plex fixes Media Server few vulneravilities
Plex Media Server is a desktop app and the backend server for the Plex media streaming service, designed for streaming movies, TV shows, music, and photo collections to over the Internet and on local area networks.
The three vulnerabilities tracked CVE-2020-5740, CVE-2020-5741, and CVE-2020-5742 were found by Tenable security researcher Chris Lyne and reported to Plex on May 31st. If attackers chain together exploits for all these security flaws, they could remotely execute code as SYSTEM, fully taking over the operating system, gain access to all files, deploy backdoors, or move laterally to other devices on the same network.
CVE-2020-13428
The vulnerability allows an attacker to cause a program to crash or remotely execute arbitrary code on the attacked system with the privileges of the user who launched the VLC. An attacker can do this using a specially prepared file or video stream. The vulnerability is relevant for the video player version 3.0.10 and earlier.

Nvidia released its June product security update, which fixed a number of serious vulnerabilities in drivers and Virtual GPU Manager. Some of the errors are highly critical and can lead to denial of service, privilege escalation, code execution, and information disclosure.
https://vulners.com/threatpost/THREATPOST:972202A633AD7E38B95647F050D95060
Directory Traversal aims to access files and directories that are stored outside the web root folder. This vulnerability was found in the Kyocera Printer d-COPIA253MF (PoC):
Privilege escalation issue in Docker Desktop for Windows. If a local attacker installs their own named channel before running Docker with the same name, this attacker can intercept a connection attempt from the Docker Service (which runs as SYSTEM) and then impersonate their privileges
https://vulners.com/pentestpartners/PENTESTPARTNERS:062566C3D6E8251ED4010F1CF0EBD564
QNAP QTS and Photo Station Local File Inclusion
QTS is an operating system for QNAP NAS. Three vulnerabilities (CVE-2019-7192, CVE-2019-7194 and CVE-2019-7195) in Photo Station can be combined in a chain to bypass authentication, inject malicious code into the PHP session of the application, and then install the web shell on the vulnerable devices. Because Photo Station works with superuser privileges, attackers can use these vulnerabilities to take control of QNAP NAS.
https://vulners.com/metasploit/MSF:AUXILIARY/GATHER/QNAP_LFI
Tools

Apple has released a free set of tools for developers of password managers and other applications that allows you to generate strong passwords:
https://github.com/apple/password-manager-resources
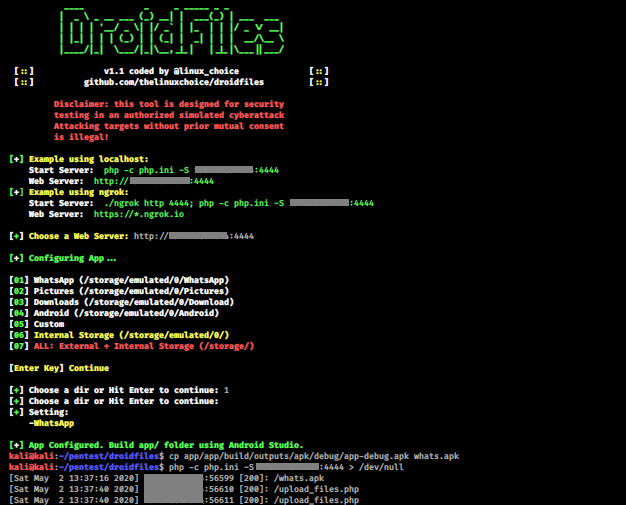
**DroidFiles
**Get files from Android directories, internal and external storage (Pictures, Downloads, Whatsapp, Videos)
https://vulners.com/kitploit/KITPLOIT:1927190131487103720
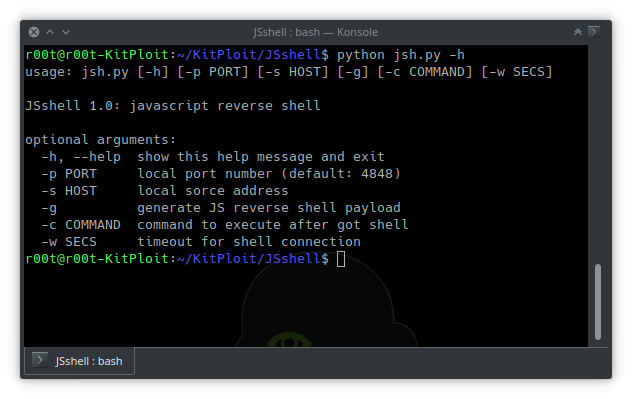
JSshell
A JavaScript reverse shell. This using for exploit XSS remotely, help to find blind XSS and etc.
https://vulners.com/kitploit/KITPLOIT:2751138742638729202
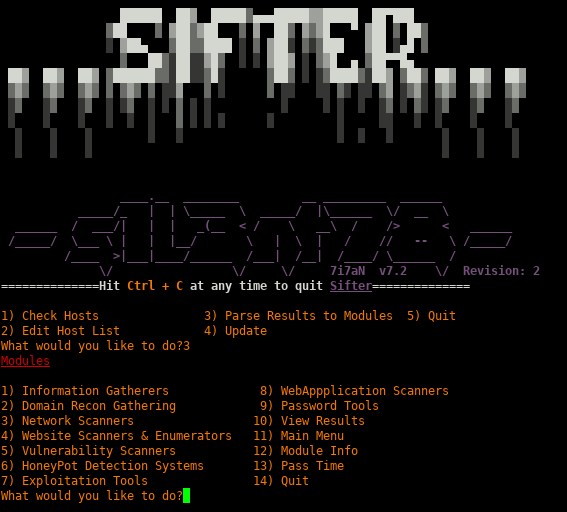
Sifter
Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to quickly perform recon tasks, check network firewalling, enumerate remote and local hosts, and scan for the 'blue' vulnerabilities within microsft and if unpatched, exploit them.
https://vulners.com/kitploit/KITPLOIT:2626669278370748953
News

On June 24, the US authorities published a new indictment against Julian Assange. According to the press service of the U.S. Department of Justice, the document does not contain any new charges, but expands the list of persons with whom the defendant conspired. Thus, according to the new indictment, the founder of WikiLeaks is accused of collusion with members of Anonymous and LulzSec.
The new indictment also contains charges for 18 counts presented in the previous document, which was approved in May 2019. In particular, Assange is charged with violating the Espionage Act for his involvement in the alleged publication of secret documents of the U.S. Department of Defense received from U.S. Army soldier Chelsea Manning in 2010.
https://vulners.com/thn/THN:988138E552E716DA1CBA18AA04A920A1

Researchers from the German company Protected discovered in July last year that the traffic lights of the Austrian company SWARCO can be hacked.
The vulnerability CVE-2020-12493, which was fixed by the manufacturer only in April this year, affected the traffic light controller of the LS4000 SWARCO CPU. From the explanations of German researchers, it follows that there was no point of entry from the Internet, but it was possible to connect physically to one of the devices, and then get access to the entire city traffic light network.
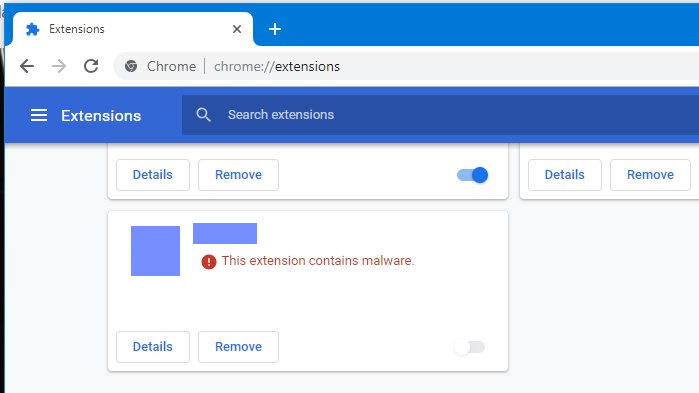
Specialists from Awake Security reported on a large-scale spy campaign in Google Chrome, where criminals registered thousands of domains and used extensions in Chrome to install malware on victims' devices.
According to experts, the detected spyware installation campaign turned out to be the largest for Google Chrome in terms of the number of downloads. Malware developers provided false contact information when they confirmed extensions to Google.
https://vulners.com/threatpost/THREATPOST:1E6E149F47007B9457A6C47B58381035
https://vulners.com/thn/THN:E679FDDE71D71EBB83D3B49D5D0E605D

**$100k for critical vulnerability 'Sign in With Apple'
**Security researcher Bhavuk Jane discovered a dangerous vulnerability in the Apple Entry feature. Exploiting the vulnerability allows an attacker to remotely bypass authentication and take control of target user accounts in third-party services and applications that used the Apple Login feature to authenticate.
According to the expert, the vulnerability can be exploited even if the user has hidden his e-mail ID from third party services, and can also be used to register a new account with the ID of Apple victim.
https://vulners.com/threatpost/THREATPOST:DF1387D21FA2EBF23BBB67081E7B75EC
https://vulners.com/thn/THN:625732FBF95E8A31678B76BF342368CC
Microsoft decided to join IBM and Amazon and take a stand against the use of face recognition technology by law enforcement agencies. As company president Brad Smith said during an online interview at the Washington Post Live event, Microsoft has already taken a “principled position” regarding the proper use of this technology.
According to Smith, Microsoft will also introduce other “review factors” that govern the use of technology in “different scenarios.” The US House of Representatives Oversight and Reform Committee held a series of hearings on the use of face recognition technology, but has not yet submitted a bill regulating them.
https://vulners.com/threatpost/THREATPOST:80908F6B687257A93CBB1FDE1BA3CEB2
Research
Hijacking DLLs in Windows: https://www.wietzebeukema.nl/blog/hijacking-dlls-in-windows
Evasor - Automated DLL/EXE Injection Tool For AppLocker/ACL Bypasses: https://github.com/cyberark/Evasor
Active Directory Exploitation Cheat Sheet: https://github.com/Integration-IT/Active-Directory-Exploitation-Cheat-Sheet
Exfiltrate data from the browser using DNS: https://github.com/veggiedefender/browsertunnel
Analyzing Malware Techniques
Fileless Malware - A self loading technique
https://danusminimus.github.io/Analyzing-Modern-Malware-Techniques-Part-1
A case of Powershell, Excel 4 Macros and VB6
https://danusminimus.github.io/Analyzing-Modern-Malware-Techniques-Part-2
https://danusminimus.github.io/Analyzing-Modern-Malware-Techniques-Part-3
Please leave your feedback. A few questions will take no more than one minute and helps us become better: https://forms.gle/D17BaFwD5hJnKkUUA
