Vulners weekly digest #8
Three traditional sections in our weekly digest. Enjoy!
Vulnerabilities and attacks
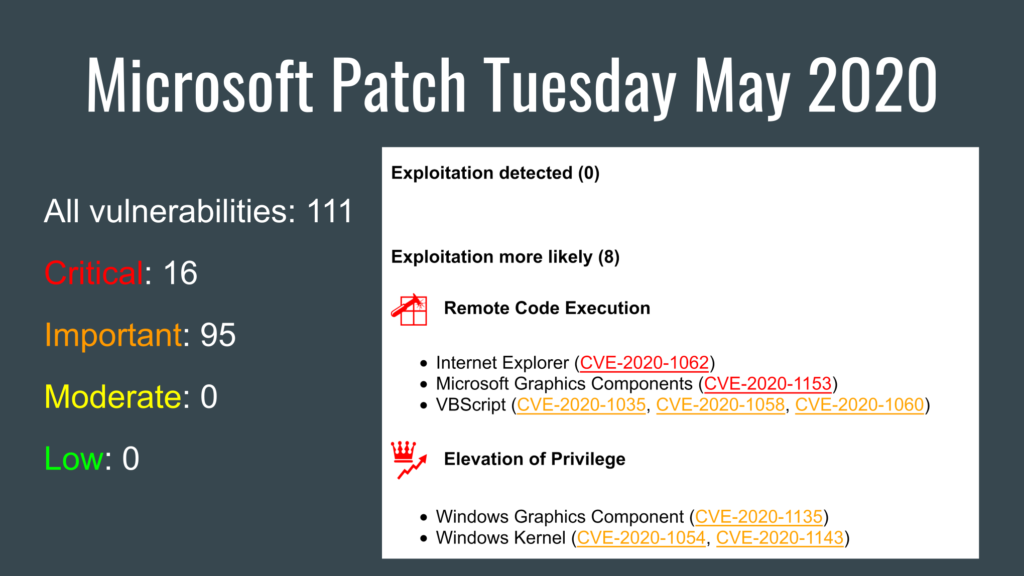
Last week, Microsoft released its monthly update - 'the second Tuesday patch', which we haven't mentioned yet, but it was done by Aleksendr Leonov in his blog. On his blog, he gave a brief overview of this update.
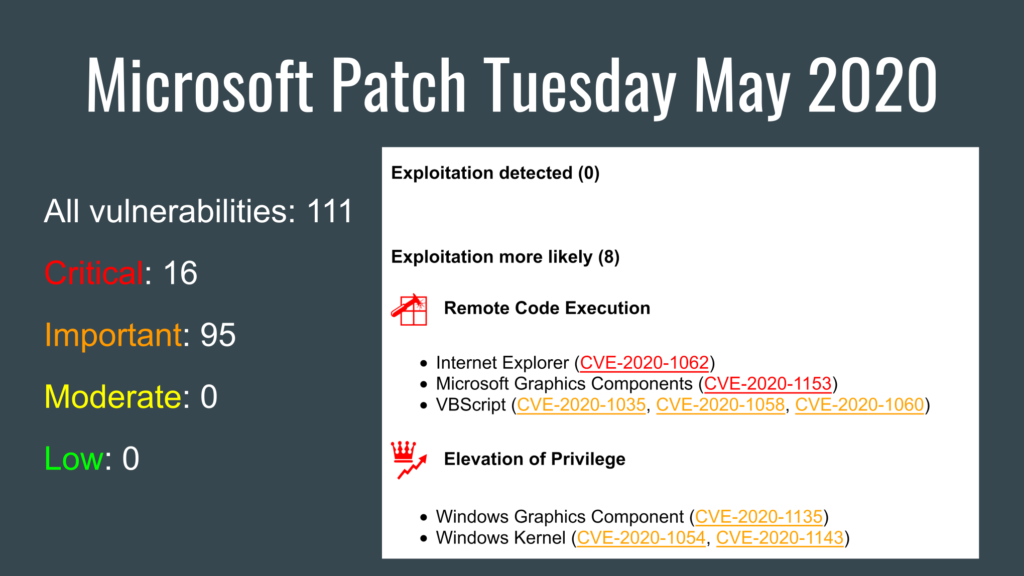
Various researches have been published this week on several vulnerabilities from the Microsoft's patch. Any road to an exploit starts with strong research :)
Ntlm relay with CVE-2020-1113
For a long time, many attackers like to use the NTLM realy technique in their operations. Firstly, there are many different protocols with which this can be implemented. Secondly, such attacks are difficult to detect at all stages of implementation.
Best explanation of how it works:
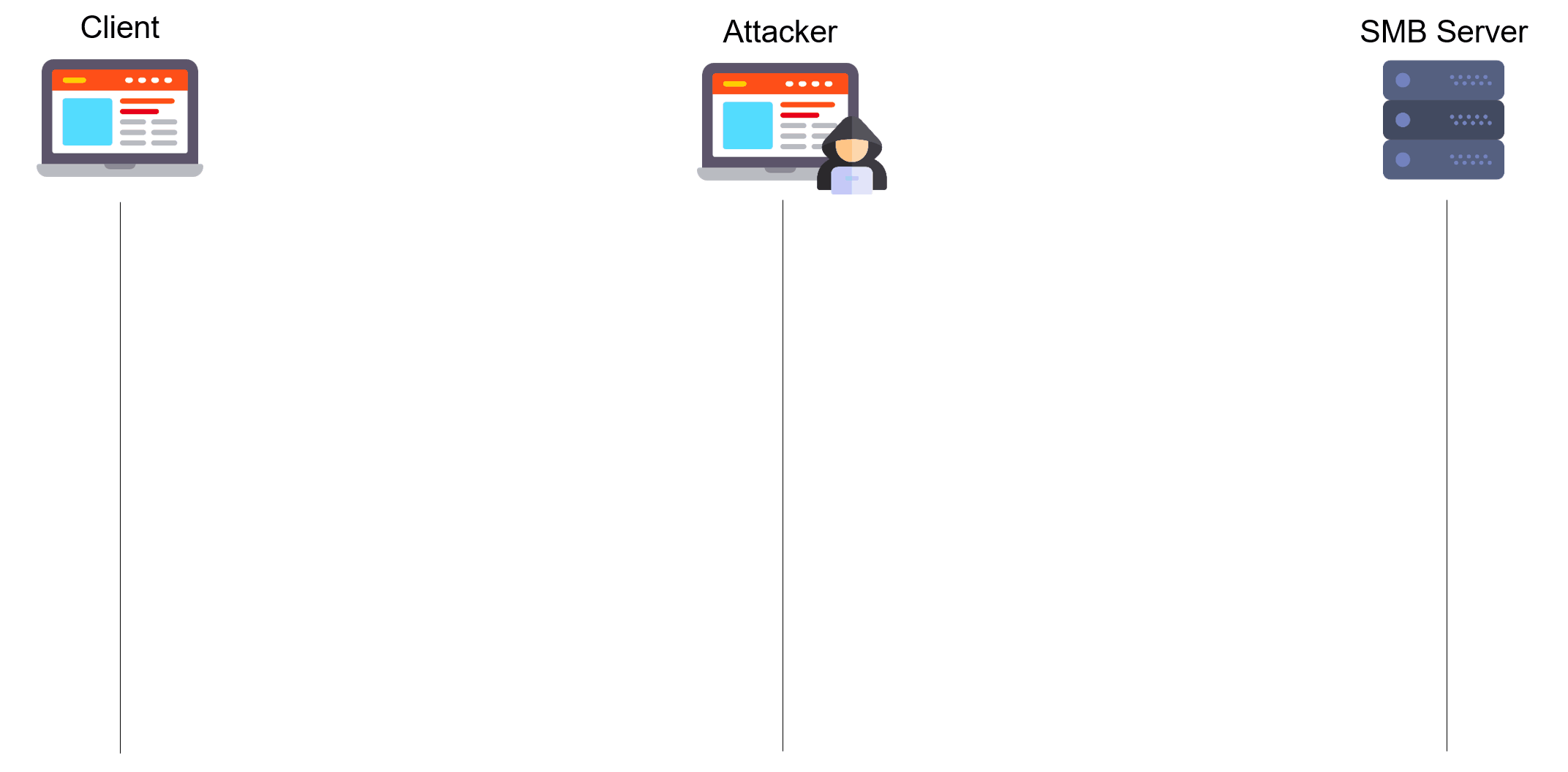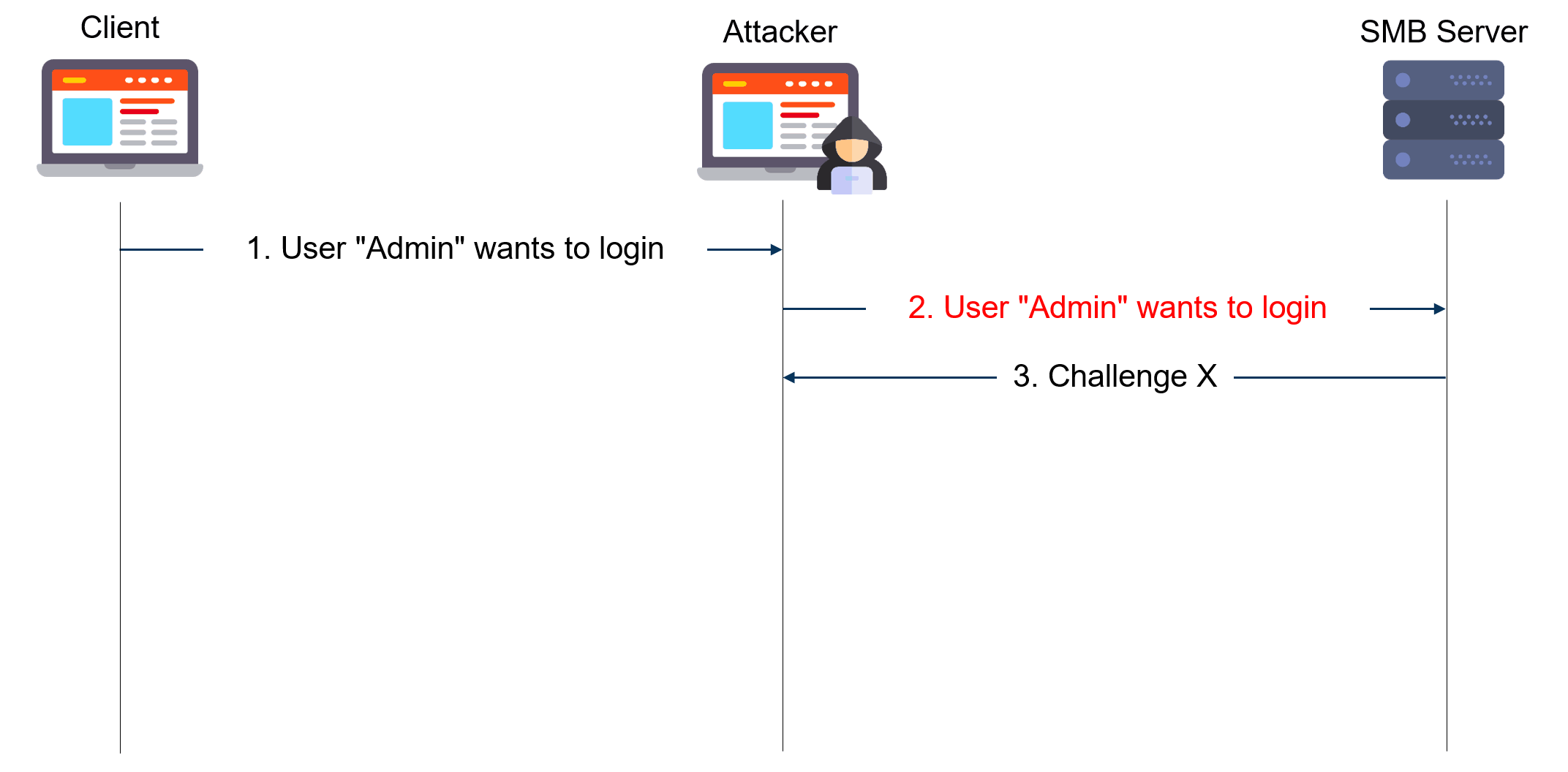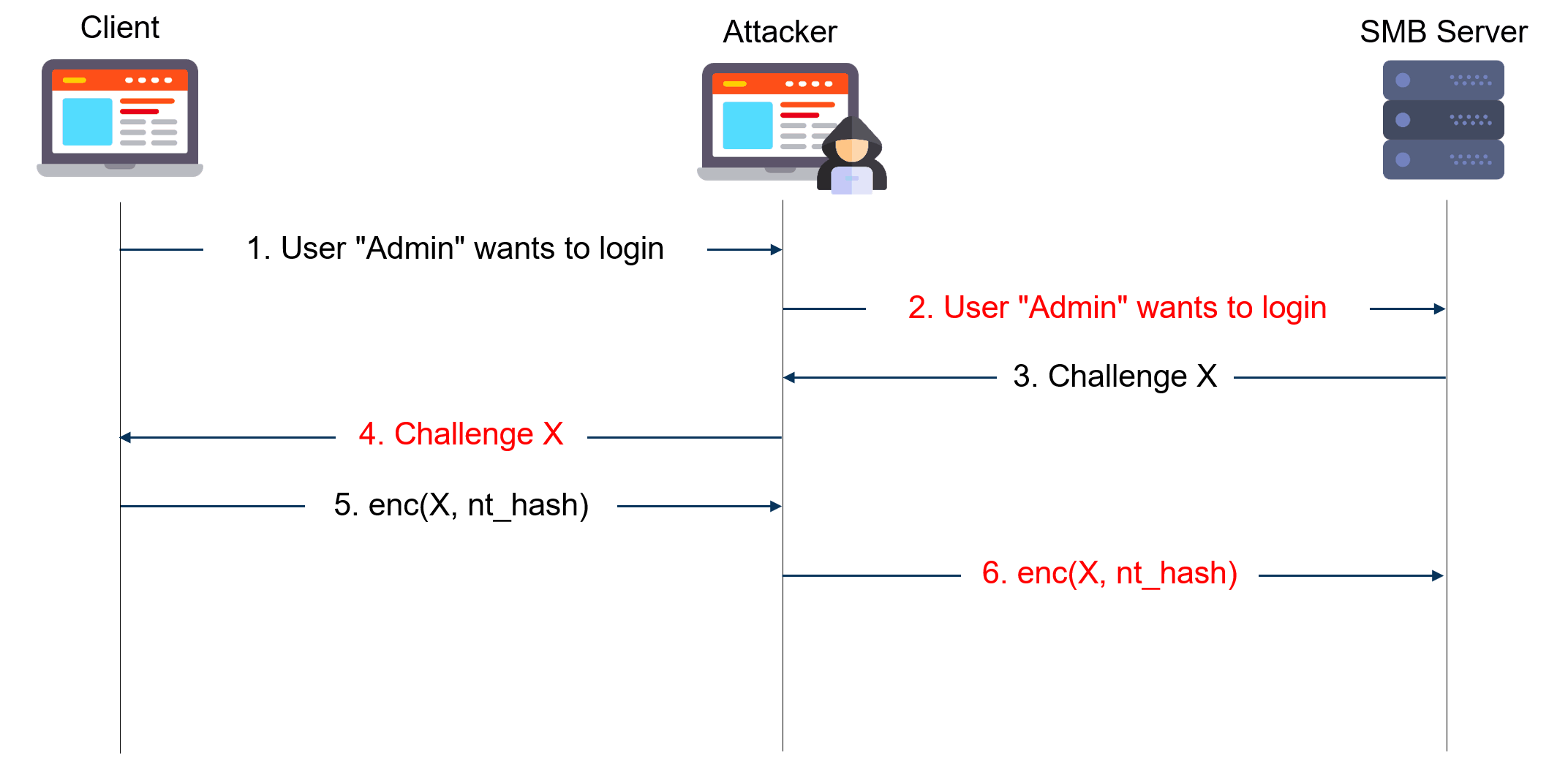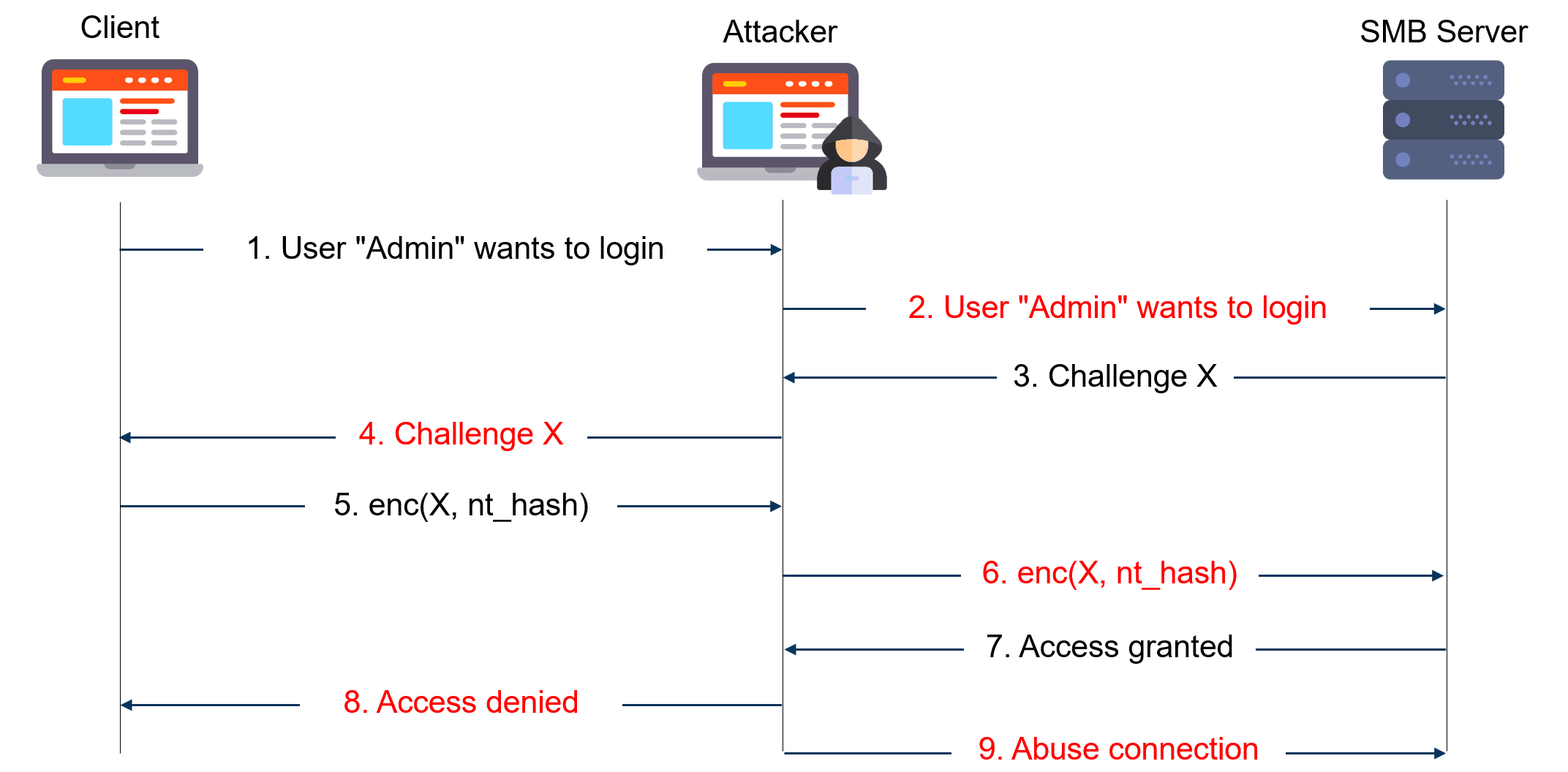
NTLM relay has been used and reused in several attacks:
- The Printer Bug – a nice way to trigger SMB connections from Windows Server (particularly handy in combination with Unconstrained Delegation)
- PrivExchange – or how to escalate from any user having an Exchange mailbox to Domain Admins
- Drop the MIC – or how to bypass completely protection against relaying
CVE-2020-1113 was fixed in the may update of Microsoft's. Read detailed research about update ntlmrelayx in impacket and adding support for the RPC protocol:
https://blog.compass-security.com/2020/05/relaying-ntlm-authentication-over-rpc
PrintDemon: Print Spooler Privilege Escalation, Persistence & Stealth CVE-2020-1048
CVE-2020-1048 was fixed in the May update of Microsoft's. The research was released on the same day as the vulnerability fix ;) Using Windows Print Spooler to elevate privileges, bypass EDR rules, gain persistence, and more. The full research consists of 2 parts:
- https://windows-internals.com/printdemon-cve-2020-1048
- https://windows-internals.com/faxing-your-way-to-system
PoC with Empire: https://github.com/BC-SECURITY/Invoke-PrintDemon
CVE-2020-1143
This vulnerability is also from the may update. Analysis in reasearch from checkpoint: https://cpr-zero.checkpoint.com/vulns/cprid-2152
Saltstack
It's time to close the topic with saltstack, because everything has already been overwied:
- Recommendations have been made for the blue team: https://gist.github.com/SwitHak/8e7fa45b5656c691ddf13c8c47e8fda6
- Full technical description has been published (specified in our previous digest)
- Public exploit has been released
Metasploit module: https://vulners.com/metasploit/MSF:EXPLOIT/LINUX/MISC/SALTSTACK_SALT_UNAUTH_RCE
vBulletin SQL Injection CVE-2020-12720

vBulletin is a commercial forum engine and WCMS developed by Internet Brands Inc. This software is written in PHP and uses a MySQL server to maintain its database.
National Vulnerability Database (NVD) is also analyzing the flaw and revealed that the critical flaw originated from an incorrect access control issue that affects vBulletin before 5.5.6, 5.6.0 before 5.6.0, and 5.6.1 before 5.6.1.
Automation for exploit: https://vulners.com/packetstorm/PACKETSTORM:157716
Easy for CVE-2019-15083
PoC for Cross-Site Scripting in ManageEngine Service Desk 10.0 (Software for IT support service). It might be interesting for red team operations to gather additional info or lateral movements:
Win Brute Logon
Our strength is in undocumented opportunities
Useful information about password brute force in Windows.
Open Account Lockout Policy and edit value Account lockout threshold with desired value from (1 to 999). Value represent the number of possible attempt before getting locked.
LockDown Policy wont work on Administrator account. At this moment, best protection for Administrator account (if Enabled) is to setup a very complex password.
BloodHound reports for blue teams

The tool was released on May 14th, 2020 during a Black Hills Information Security webcast, A Blue Teams Perspective on Red Team Tools.
SayCheese
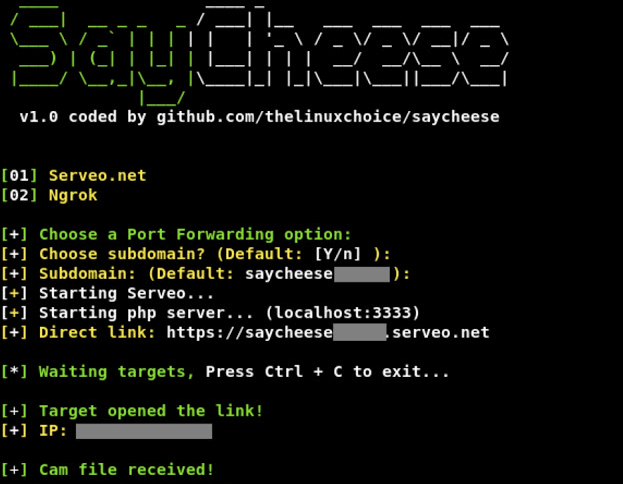
Take webcam shots from target just sending a malicious link
Evilreg
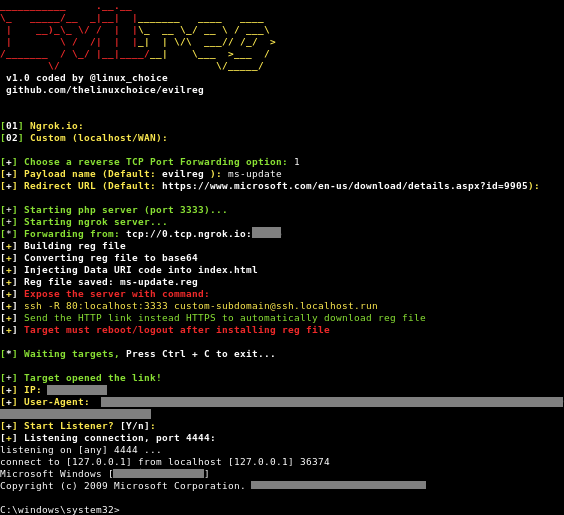
Reverse shell using Windows Registry files (.reg)
Ransomware Hit ATM Giant Diebold Nixdorf

Diebold Nixdorf, a major provider of automatic teller machines (ATMs) and payment technology to banks and retailers, recently suffered a ransomware attack that disrupted ProLock operations
The Ransomware is delivered to the compromised system using the Qbot Trojan. ProLock was first recorded in March 2020. What's interesting about ProLock is that, as the FBI says, ransomware is written with mistakes, so it can spoil encrypted files larger than 64MB when decrypted.
https://vulners.com/krebs/KREBS:844FF2B9143930EF190E45B7C1C84F58
Pay $42m or Trump’s 'dirty laundry' goes online

On May 12, hackers attacked the resources of the New York law firm Grubman Shire Meiselas & Sacks and stole 756 Gb of confidential documents from its clients. Founder Allen Grubman is the most famous entertainment lawyer who works, among others, with Madonna, Lady Gaga, Elton John, Robert De Niro and U2.
Then the hackers demanded a ransom of $ 21 million. The investigation was undertaken by the FBI. At the same time, the feds reported that this hacking is an act of international terrorism (?!), And they are not negotiating with terrorists and will not pay the ransom. The group responsible for ransomware Sodinokibi was named guilty of hacking.
However, on Thursday the situation changed. Hackers said that they had scanned the stolen data array and found there the “dirty laundry” of US President Trump, so the ransom amount doubled - up to 42 million dollars.
https://vulners.com/hackread/HACKREAD:EB8C10DB0B0A37DC44A7D11B10F66A47
'ThunderSpy' Attack

Research from the Dutch engineer björn Rotenberg (Björn Ruytenberg), who revealed new attack vectors for the Intel Thunderbolt 3 Protocol.
Thunderspy, as the researcher called his new attack vectors that allow an attacker to steal data from encrypted disks or read and write all system memory, even if the computer is locked or in sleep mode.
There is no protection for vulnerable devices other than physically disabling Thunderbolt. Even the software shutdown of Thunderbolt was bypassed by Roitenberg. Windows, Linux, and partially MacOS PCs - vulnerable.
Such vulnerabilities have little application to commercial hacking because they require even short-term, but mandatory physical access to the device under attack. But for law enforcement agencies, organizing such access is a common thing. That is, knowledgeable agencies have been able to gain access to computer content without compromise since at least 2011, when Thunderbolt appeared.
https://vulners.com/threatpost/THREATPOST:103AFBDE6D261555120729CAF7A921A4
