OSS-Fuzz data in Vulners

This month, vulners collected Google's open-source OSS-Fuzz data. OSS-Fuzz is a great tool for fuzz testing your projects to uncover different kinds of programming errors in software.
"OSS-Fuzz provides ‘fuzzing as a service’ for open source projects" https://opensource.google/projects/oss-fuzz
It's amazing that this data is now available both for easy visual searching and via the Vulners scanner API. Examples for your requests:
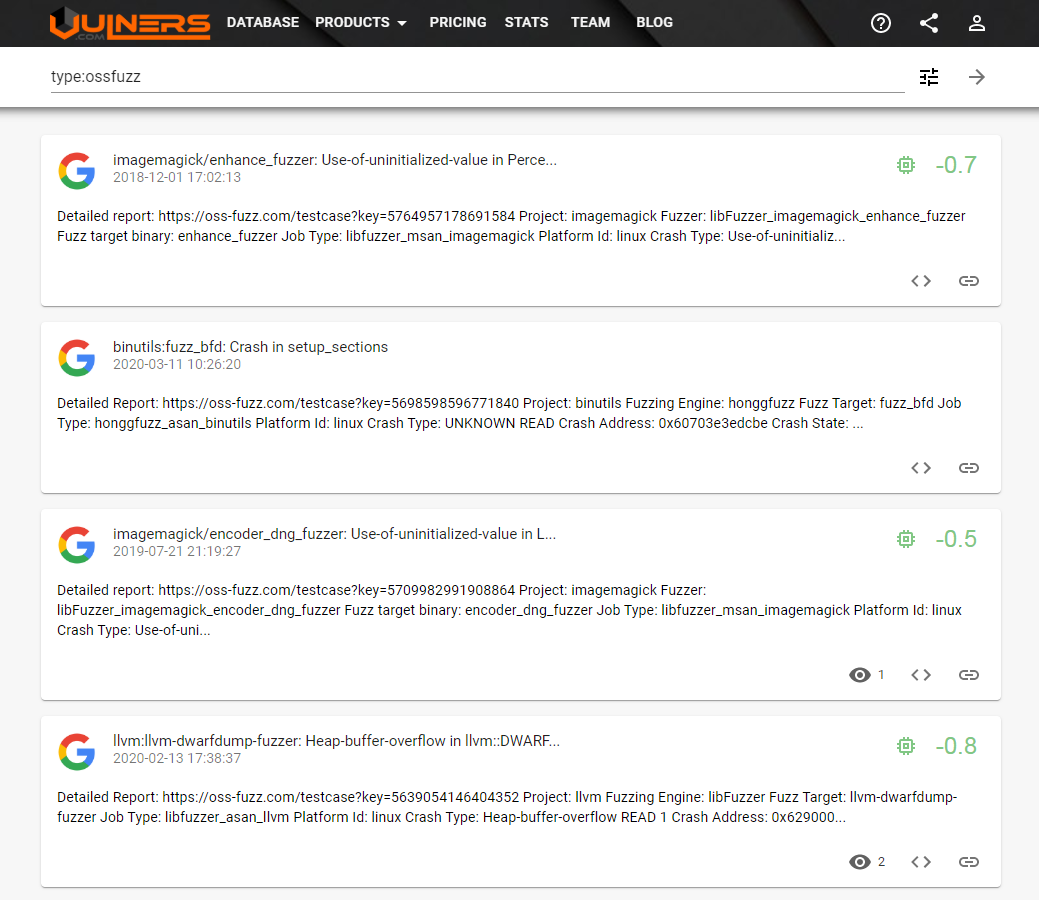
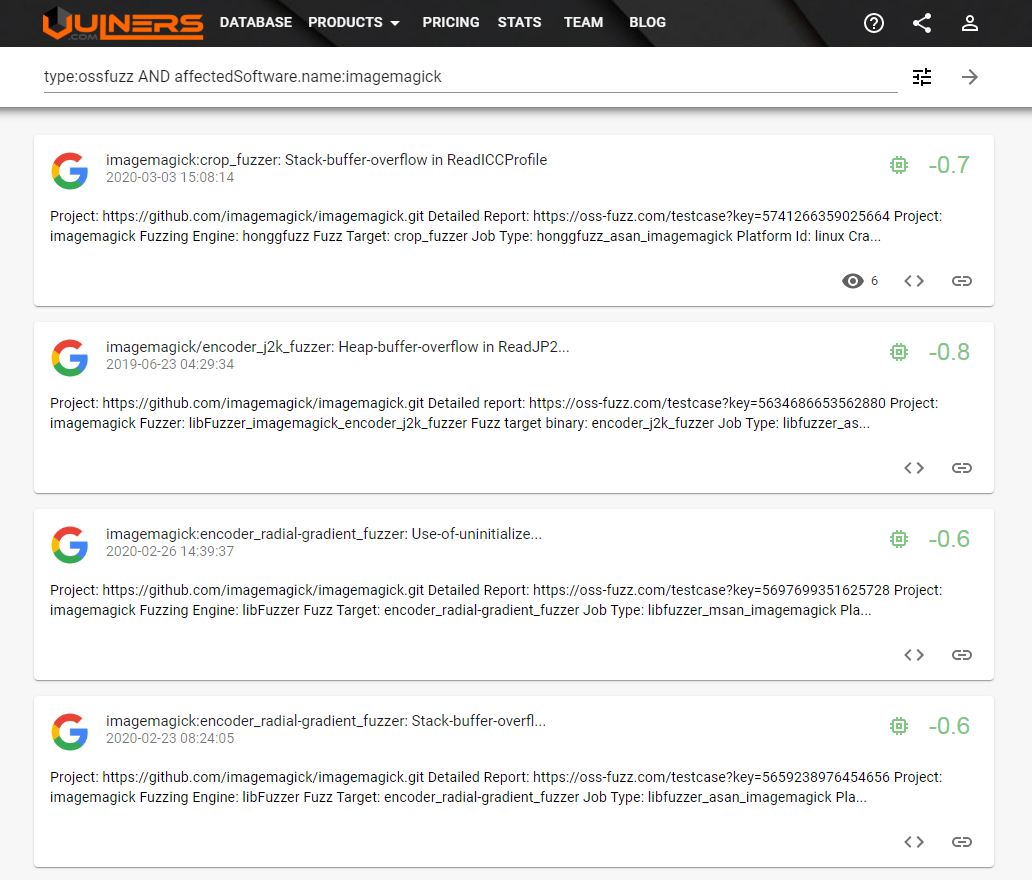
<type:ossfuzz AND affectedSoftware.name:your_package_name>
IMAGEMAGICK CVE-2016-3714
This critical RCE vulnerability is a prime example. Open-source library for image processing that lets users resize, scale, crop, watermarking and tweak images.
By uploading a booby-trapped selfie to a web service that uses ImageMagick, an attacker can execute malicious code on the website’s server and steal critical information. In other words, only those websites are vulnerable that use ImageMagick and allow their users to upload images.
The exploit for the vulnerability has been named: ImageTragick
The vulnerability patched in versions 7.0.1-1 and 6.9.3-10 of ImageMagick.
You can write code perfectly and securely, but you often use open-source libraries that may contain serious vulnerabilities. Why can developers be interested in checking information security in components of their own applications?
Supply chain attacks are kind of threat that target software developers. The main purpose is to access source codes, libraries or update mechanisms by infecting legitimate applications.
Software supply chain attacks explained
Attackers hunt for unsecure network protocols, unprotected server infrastructures, and unsafe coding practices. They break in, change source codes, and hide malware in build and update processes. One of the types of supply chain attacks is compromised software building tools or updated infrastructure.
Vulners OSS-Fuzz data is one of the components of solving these problems. You can use it for improve your information security and built automation checking process for your applications.
Examples of using via Vulners the proprietary API:
import vulners
vulners_api = vulners.Vulners(api_key="YOUR_API_KEY_HERE")
results = vulners_api.softwareVulnerabilities("httpd", "1.3")
You can get your API key after registration:
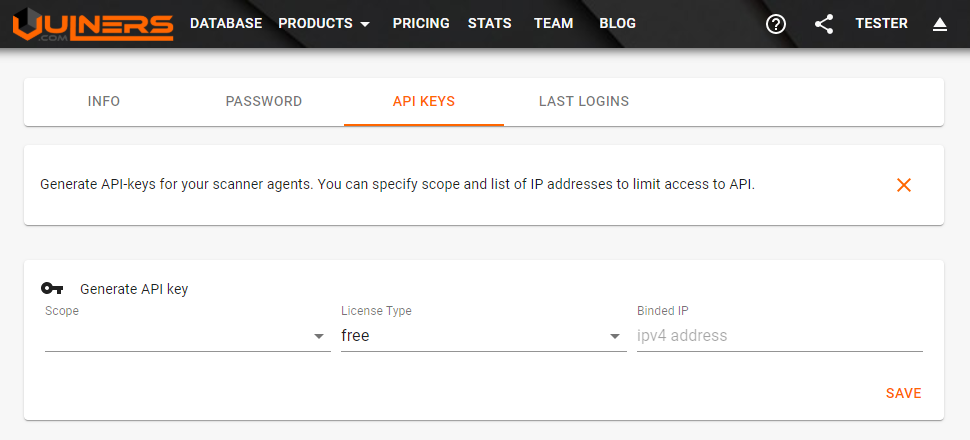
Open API keys tab and generate a new token
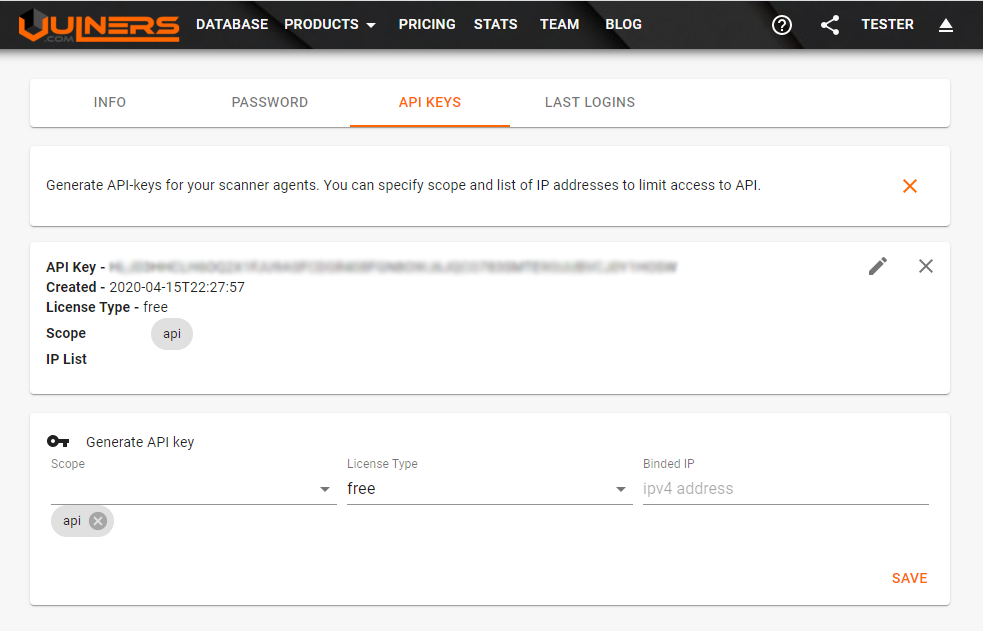
Keep it a secret and don’t show it to anyone
You can use the most popular python framework for automation testing - pytest. Extract all used packages from the development application and check with simple script.
import vulners
import pytest
vulners_api = vulners.Vulners(api_key="YOUR_API_KEY")
checking_packets = {
"imagemagick": "7.0.10-2",
"arrow": "0.17.0",
"wireshark": "3.1.1"
}
@pytest.fixture(scope='module', params=[(k,v) for k, v in checking_packets.items()])
def vulners_checking(request):
"""
Checking packets.
:param request: Pytest Request object.
:return: result after checking packet via Vulners api.
"""
packet_name = request.param[0]
packet_version = request.param[1]
checking_result = vulners_api.softwareVulnerabilities(packet_name, packet_version)
return packet_name, checking_result
def test_packets(vulners_checking):
packet_name, checking_result = vulners_checking
assert len(checking_result) == 0, f"{packet_name} packet is vulnerable, update it."
Comment: Pytest provides many biult-in features for creating report with results. https://github.com/allure-framework/allure-pytest for generation allure reports, pytest-html for further conversion to the pdf format or rendering a beautiful mail.
Script results with the default startup parameters:
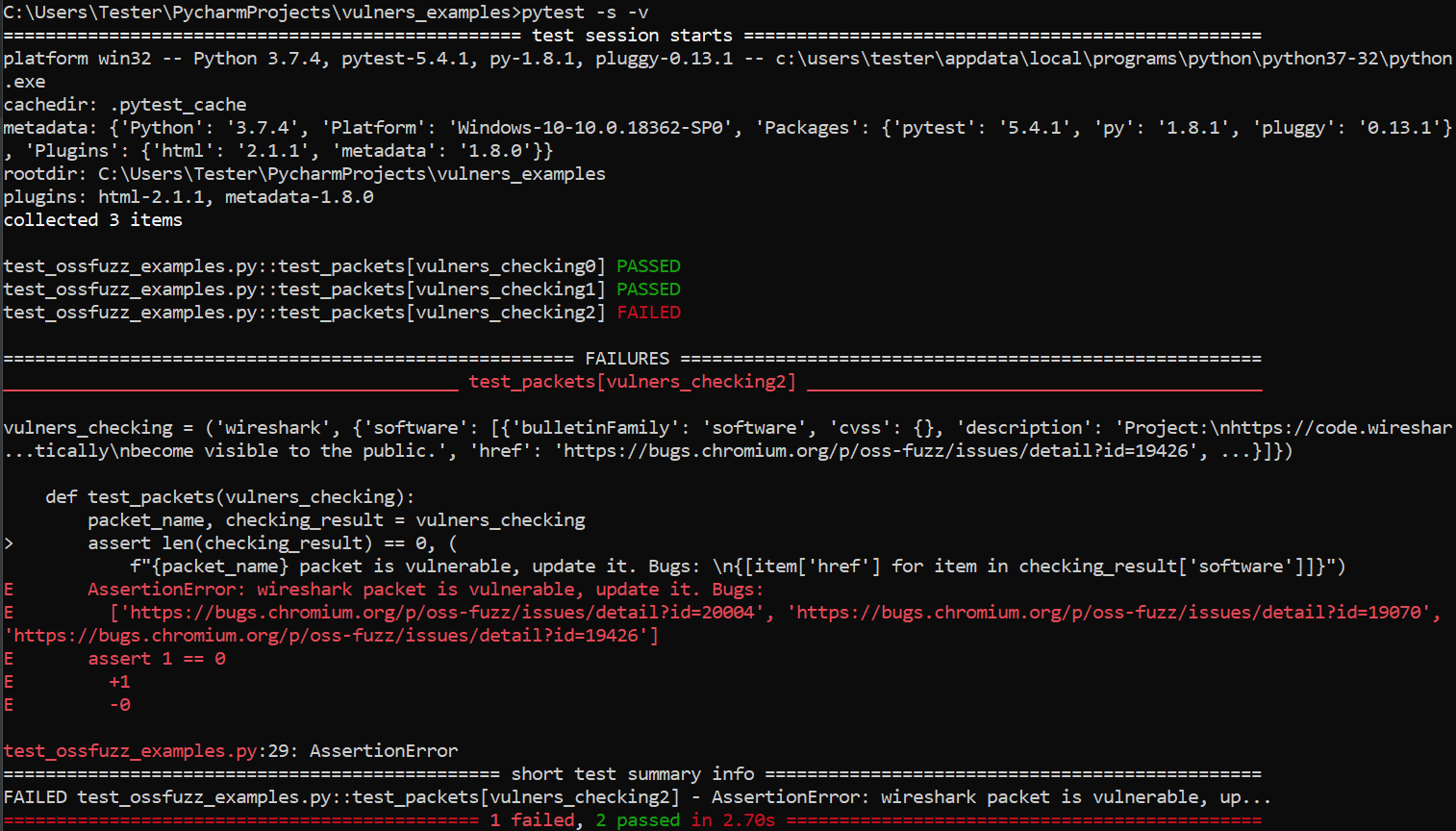
by the
For example, this approach can be integrated into a checking for all the used versions of your libraries when building your projects via CI/CD systems. According to our statistics, this functionality is already in demand - there are about 10 requests per second for checking library versions.
Current pricelist:
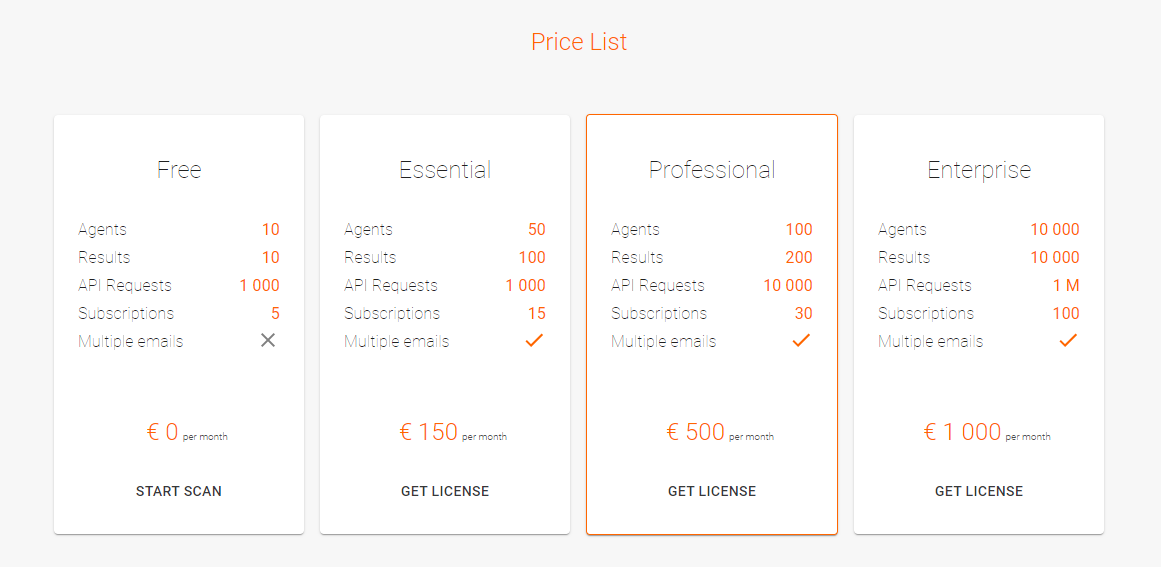
We provide up to 1000 free requests per month to the Vulners api. This is enough to check a typical project for 20-30 libraries every three days. It is possible to test now!
The Vulners platform is constantly improving and adding more and more new integrations that you can use in your projects. Follow our news and new research!
