
Vulristics: Beyond Microsoft Patch Tuesdays, Analyzing Arbitrary CVEs
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C
Hello everyone! In this episode I would like to share an update for my Vulristics project.

For those who don't know, in this project I am working on an alternative vulnerability scoring based on publicly available data to highlight vulnerabilities that need to be fixed as soon as possible. Roughly speaking, this is something like Tenable VPR, but more transparent and even open source. Currently it works with much less data sources. It mainly depends on the type of vulnerability, the prevalence of vulnerable software, public exploits and exploitation in the wild.
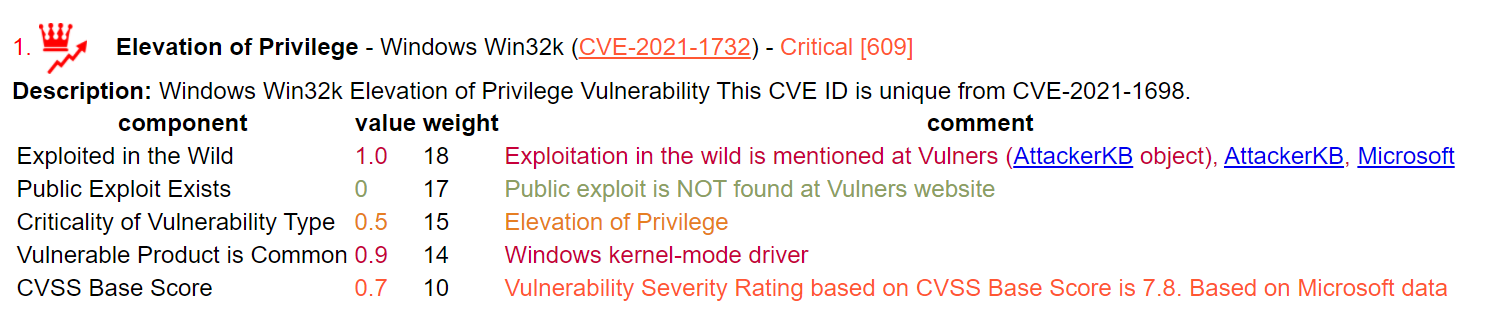
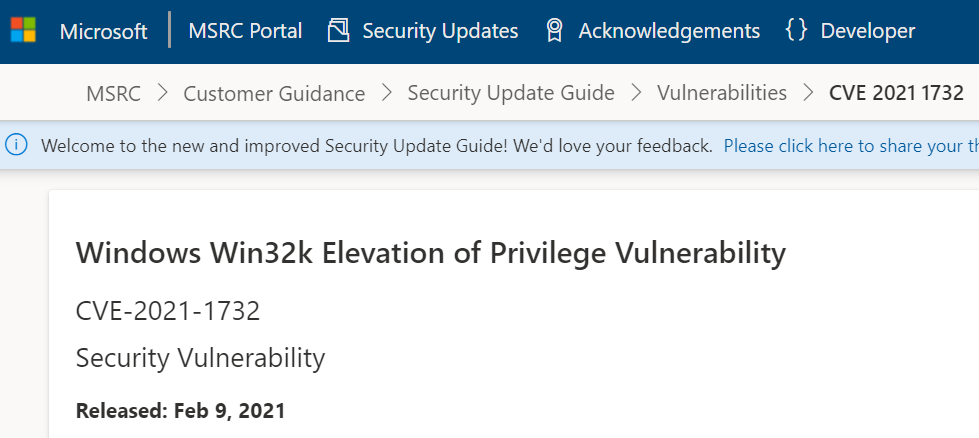
I started with Microsoft PatchTuesday Vulnerabilities because Microsoft provides much better data than other vendors. They have the type of vulnerability and the name of the vulnerable software in the title.
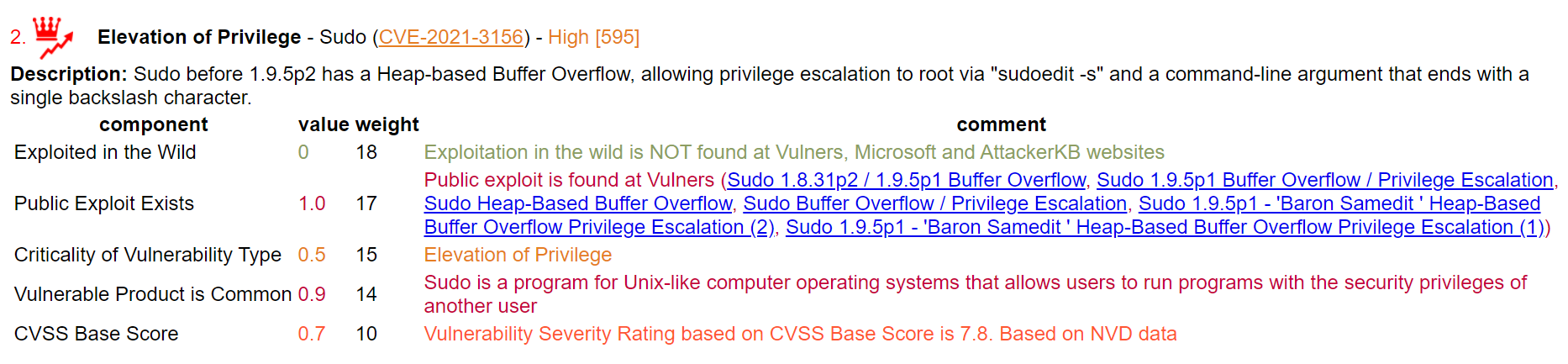
But it's time to go further and now you can use Vulristics to analyze any set of CVEs. I changed the scirpts that were closely related to the Microsoft datasource and added new features to get the type of vulnerability and name of the software from the CVE description.
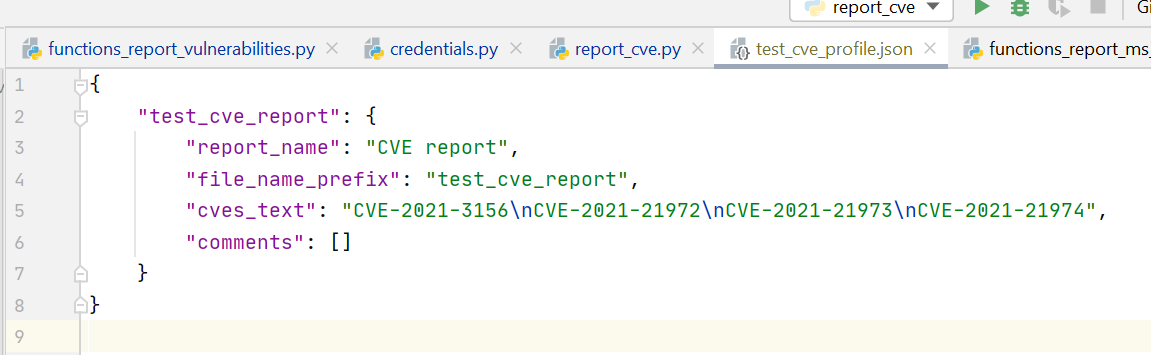
How to use it?
So the general process now looks like this:
- create a profile in JSON where you specify a list of CVEs to be processed
- start the analysis process to get a report
The profile format is the same as I used to generate Microsoft Patch Tuesday reports.
For Microsoft Patch Tuesday, the profile and report can be generated automatically by setting only the year and month.
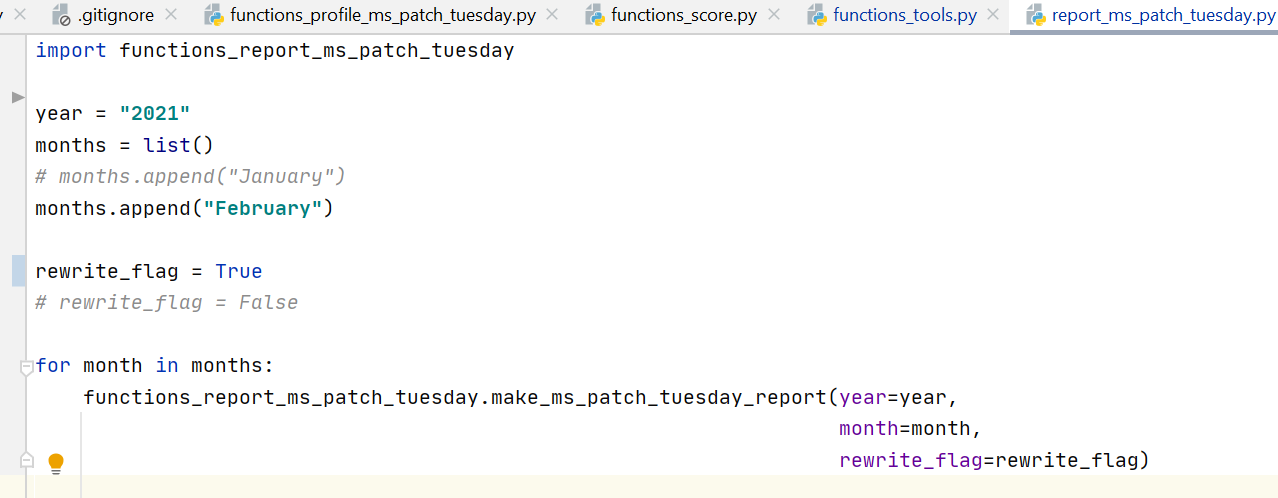
And you can easily create a profile to generate a report for any CVE set.
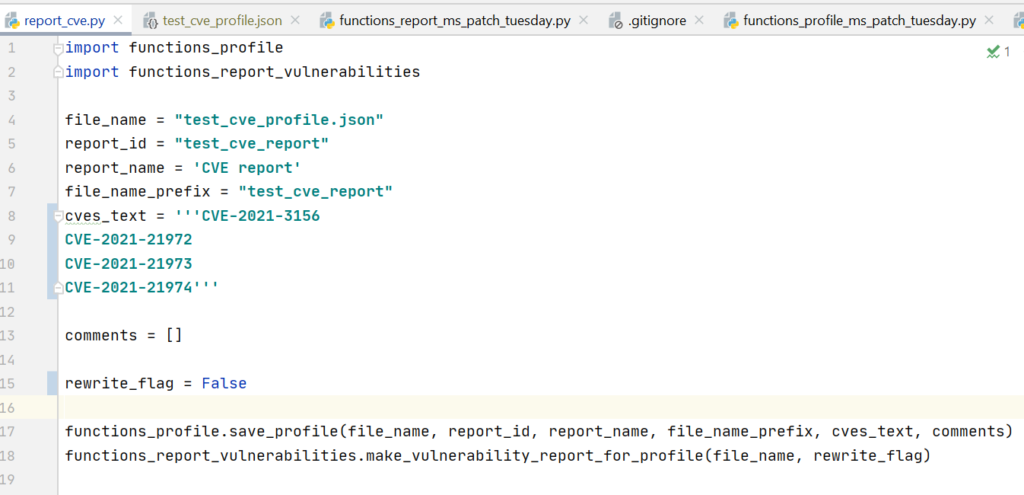
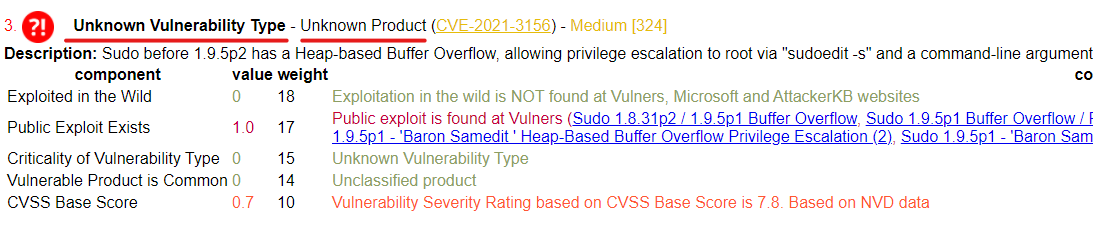
How does the detection for Vulnerability Type and Product work?
And does it always work? Of course not. As I stated in the title of this project, it works heuristically.
> A heuristic technique, or a heuristic (/hjʊəˈrɪstɪk/; Ancient Greek: εὑρίσκω, heurískō, 'I find, discover'), is any approach to problem solving or self-discovery that employs a practical method that is not guaranteed to be optimal, perfect, or rational, but is nevertheless sufficient for reaching an immediate, short-term goal or approximation.
There is no AI magic in it, only the rules that you, as a practitioner, can set within th Vulristics framework. Vulnerability types and product names are searched by name in the rule or a set of additional strings.
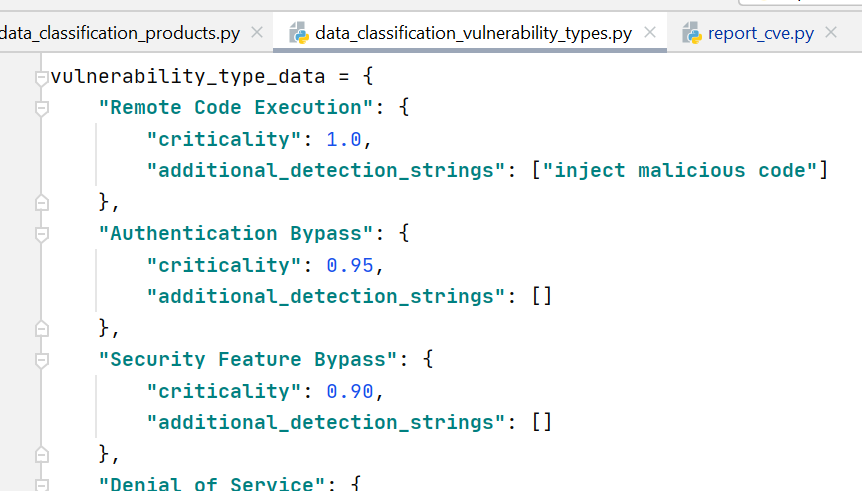
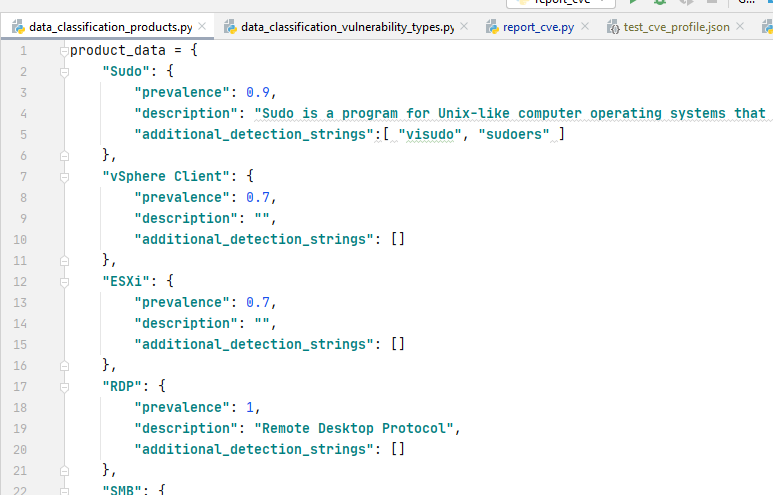
Therefore, if some software or type of vulnerability is not found, you can easily add a rule, and next time it will work fine. If you share these discovery rules somehow, we can grow this database together. 
When the description-based detect failes Vulristics shown "Unknown Vulnerability Type" or "Unknown Product".
What for can you use it?
Basically, it can be used with any tool that operates with CVE:
- Vulnerability scan results for one host/docker container or the entire infrastructure
- Vendor's Security Bulletins
- Differences in the knowledge bases of the Vulnerability Scanners
Any other ideas?
That's all for today! If someone wants to participate in the project, you are welcome to write to me on Telegram or in any other social network. Subscribe on youtube, press like buttons and leave your comments. 
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C